Spam prevention solutions: how to protect oneself from email threats
1. Email and Spam
Today, any web user is very familiar with “spam” and suffers its increasingly persistent inconveniences. We can safely say that, by now, most of the emails that we receive on a daily basis can be classified as spam. And there are so many of these emails!
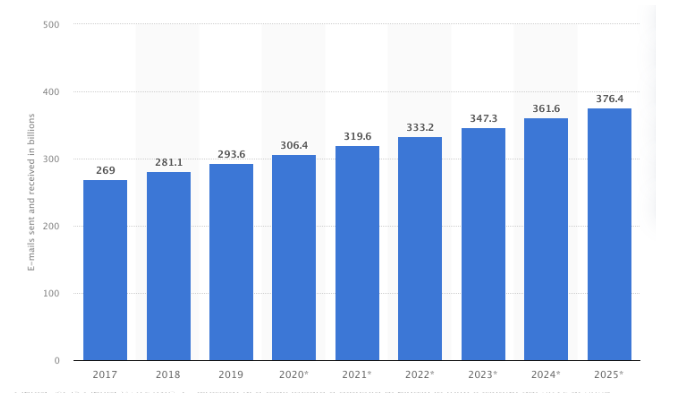
As we can see from the graph shown in fig.1 (source statista.com), as many as 333 billion emails were sent every day in 2022, and this number continues to grow year after year.
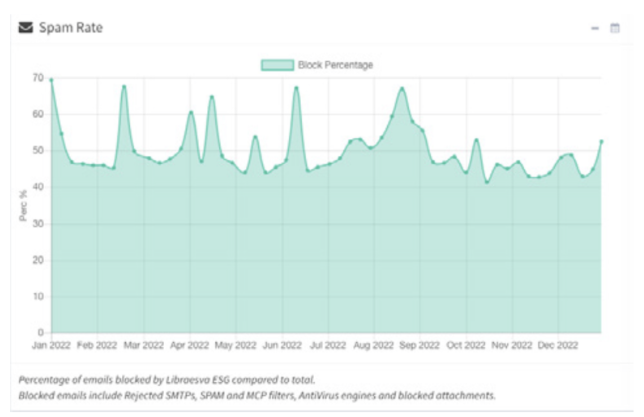
According to Libraesva, an Italian company that makes well-known anti-spam software, of all these emails, a percentage of close to fifty percent consists of spam (fig.2) and, therefore, is blocked by Libraesva anti-spam.
Therefore, all of us are forced to live with the phenomenon of spam in our digital lives, which is showing itself to be increasingly bothersome.
Moreover, significant numbers of spam emails are not only bothersome but even result in aggressive and malicious purposes: in this case we are talking about phishing. It is, therefore, crucial – for both companies and users – to take effective prevention and protection measures (spam prevention solutions).
2. Spam: where this word originated
Everyone knows – and very well! – what spam is, but few know the etymology of this term, which, when it came into vogue, was in no way associated with either the world of the internet or with a particular type of email message.
The word “spam“ is derived from the merging of two words in the English language, “spiced” and “ham,” and originally denoted a brand of canned meat seasoned with spices, using mainly minced pork and produced by the American company “Hormel Foods,” dating back to the 1930s.
It was an inexpensive product of mediocre quality and not particularly appetizing.
Perhaps, partly because of this low cost, the manufacturing company obtained a contract to supply this canned meat to the U.S. Army and the U.S. Navy.
During World War II, and then in Britain during the economic crisis of the immediate postwar period, these cans of “spam” became the staple food for many British citizens. The word “spam” acquired the meaning of something disgusting, but inevitable.
However, in order to reach the current meaning, we have to wait until 1970 and the Monty Python group, which performed a comedy sketch, set in a restaurant whose menu consisted entirely of dishes made of “spam,” the aforementioned canned meat.
The diner’s waitress explained the menu, which consisted entirely of “spam” meat, while a group of patrons obsessively repeated the word, “Spam, spam, spam!” basically preventing any conversation from other diners.
Thanks to this skit, which became famous, the term “spam” became synonymous with unwanted and annoying information.
However, email had not yet been born: we may recall that the first email in history was written in 1971 by Raymond “Ray” Tomlinson who used ARPANET (the network that was founded in 1969 and later became the internet) to send an email message between the first universities connected through this network. We owe the idea of using the @ symbol to separate the name from the domain in an email address to Ray Tomlinson.
The step from the birth of email to spam was a relatively short one. By the 1990s, the use of email was spreading, and the first cases of mass emailing occurred. In some cases, these were messages sent by mistake due to program malfunctions in newsgroups. In other cases, they were advertising messages sent out in great quantities.
The recipients of such annoying and inappropriate messages used the very word “spam” to effectively define such messages.
In conclusion, despite the fact that “spam” has taken on the meaning we now know, canned meat products from “Hormel Foods”- bearing that name to this day – are still being sold in the United States.
3. What Spam is and why it presents a danger
Spam can be defined as “sending email, typically in a bulk and anonymous manner, so that it results in being unwanted and bothersome.”
However, while most spam emails are merely annoying, a significant number have malicious purposes in order to convey cyber attacks or scams. In these cases, spam takes on the form of phishing, which needs to be counteracted.

We must be aware that email is still the main vehicle of attacks today, a full 78% according to the YOROY 2022 Report.
In the majority of cases, these phishing emails are used to:
» convey malware to enter the victim’s computer systems and take control of them;
» stealing credentials to access accounts (corporate, banking, social, etc.);
» carry out computer fraud (typical BEC model)
In order to accomplish this, the email will be “armed” with a link or an attachment. If the user clicks on these, the phishing will have achieved its purpose.
The majority of spam and phishing emails will be blocked by our computers’ antispam systems (as we will see later), but some, perhaps because they are more carefully crafted, may pass this filter.
At this point, everything is in the hands (and heads) of the users, who – as I like to explain in my training courses – represent the last antispam, the last line of defense.
Of particular note among the forms of phishing is the type defined as spear phishing.
This is the most sophisticated and devious variant of phishing, and it is a targeted attack. The fisherman uses a “spear” to catch precisely “that” particular fish. The object of the attack is carefully selected and studied (today it is very easy to gather information about a person, through social media and the web).
In this case, the emails sent are prepared ad hoc to appear credible and mislead victims by mentioning real details or names. Sometimes the sender’s email address may have been spoofed using a technique known as “spoofing” (which we will discuss later). The email will appear to come from someone we know and trust (a colleague, superior, family member, or friend) and, therefore, will be much more devious. In addition, it will have a greater chance of success; it may not be blocked by the antispam, precisely because it is more carefully constructed.
4. Spam prevention solutions: how to protect oneself
Prevention measures against spam, and especially phishing, should be taken on two levels, which are different but, nevertheless, interrelated:
» user training, in order to create awareness;
» technical solutions, such as firewalls, anti-spam software, DNS filtering (note: you can add some links to FlashStart solutions here).
4.1 Creating awareness
It is well known that more than ninety percent of cyber attacks are caused by human error, basically by a user — distracted or unaware — who clicks on the wrong spot.
Thus, any technological measures, however necessary, are likely to be insufficient without user training.
A large part of malicious spam is created with techniques that are not particularly sophisticated, often using automatic translators which produce texts with errors.
Why do attackers not care about crafting perfect emails? Because it is not necessary. There are a number of users who bite on even rudimentary emails.
This happens especially with non-targeted phishing, conducted with the logic of trawling. They send thousands of identical emails to different addresses, knowing that, within the vast quantity, someone will take the bait anyway and click on the link or attachment in the email, while this does not occur with spear phishing because it is a targeted attack which requires a carefully constructed email about the chosen victim.
One technique frequently used in phishing is typosquatting (“typo” is an English word that means typographical error), or also cybersquatting, or domain squatting.
In practice, the visual similarity of different characters is exploited in the registration of deceptive domains whose names vary by one letter (or at most two) from the name of a known website.
Then one sends the email containing the forged link with typosquatting, making the recipient believe that it is his bank or a known sender.
Typosquatting is also used to forge the sender of an email.
In the example shown in the figure (one of many cases – real ones – that I see in my business), employees of the company receive an email from the sender “Office 365 Support” with a request to update the password of the company mailbox through a prominent link in the body of the email.
A trivial trick that can be easily discovered if only the user is not fooled by rushing.
Let us never forget: our haste is cyber criminals’ best friend!
However, if the user is careful and does not get caught up in “compulsive clicking,” instead of clicking on the link, he will try to figure out if the sender is really what he appears to be.
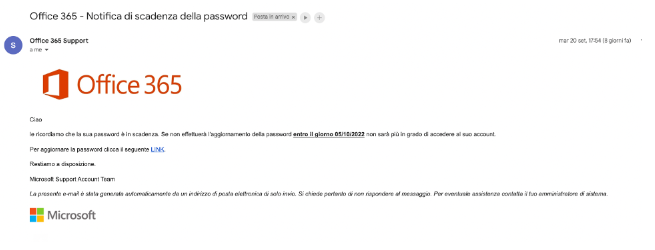
It is very simple: just click on the sender’s address (in this example: “Office 365 Support”). Another window will open in which we can see the real sender, which is not “Office 365 Support” (that is just a text field, where anything could be written).
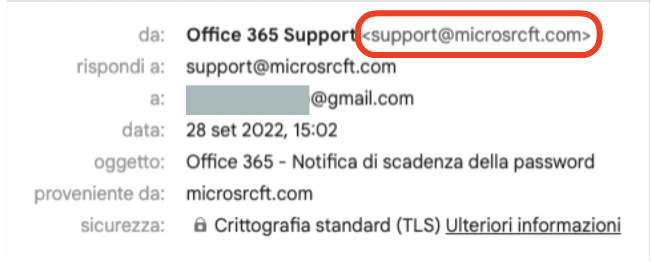
Figure 5 – Read the sender of the email
The real sender is what appears in the window we opened: and evidently support@microsrcft.com is NOT the real microsoft.com domain address.
This simple and immediate check is enough to unmask spam!
So, the rule that every user should always put into practice is to be careful and not trust the emails he or she receives, especially if they require clicking on a link or attachment.
4.2 Spam prevention solutions: technological measures
The services which FlashStart technology provides are extremely useful – even indispensable.
It is also essential to install an advanced anti-spam, which is able to preemptively analyze every incoming email message.
This must be done compulsorily by any company, while private users, who use free email providers (Gmail or others), will have to choose providers with sufficiently secure anti-spam, because, in these cases, it is not possible to install professional antispam which requires a server-client architecture (which is usually not present in private email users).
Among these free email services, I would recommend Gmail, which has – even in the free version – a sufficiently effective antispam, while I advise against almost all other providers, which do not offer adequate protection on email.
One of the most frequent and insidious threats which advanced anti-spam agents are able to detect is spoofing. This term is used to define the misidentification of the sender of an email.
In other words, one can send an email by having the address which corresponds to another account appear as the sender. This is even without having access to the forged account, that is, without knowing the credentials of the mailbox being used.
This technique is extremely dangerous because it can be carried out even without great computer skills.
Spoofing exploits the weakness of the Simple Mail Transfer Protocol (SMTP).
It is a protocol defined in 1982 by John Postel, with the standard RFC 821, later updated by RFC 2821 (https://datatracker.ietf.org/doc/html/rfc2821) and is still used today to send mail over the internet.
Therefore, the SMTP protocol is one of the oldest on the internet, and among its weaknesses is that it cannot handle sender authentication. This is a serious vulnerability because it can be exploited by those who use email as an attack tool to engage in phishing.
Although spam and spoofing are still a serious vulnerability in email today, a radical overhaul of the SMTP protocol is not considered feasible because of the large number of implementations of this protocol and especially because of the complexity of such a change and the backward compatibility problems which would be created.
The spoofing technique is, therefore, very effective for carrying out phishing, especially spear phishing attacks, which have become the most popular attack tools for conveying malware, both at the private and corporate levels.
The less attentive (or less risk-aware) user could easily be misled by a spoofing email, so it is critical to equip companies with anti-spam systems which can recognize and block spoofing and other threats from an email message.
Such anti-spam software can process each incoming email and deliver it to the recipient only if it is assessed as safe.
In order to accomplish this, they use some checking protocols which were created afterward, when it was realized that the SMTP protocol was extremely weak.
Basically, they perform those checks automatically, which the average user would not be able to do on his own, and are used in the most advanced anti-spam software.
These are three types of checks which should not be used alternatively but together, in order to increase their effectiveness:
» Sender Policy Framework (SPF): this allows verification that an email sent from a given domain actually comes from one of the hosts enabled by the domain managers. This list is made public through a DNS record. It is an anti-spoofing technique which determines whether or not an incoming email from a domain was sent from a host that was authorized to send email from that domain. It was proposed in 2000, then standardized in 2014 with RFC 7208.
» DomainKeys Identified Mail (DKIM): this allows domain managers to add a digital signature via a private key to email messages. DKIM, therefore, adds an additional tool for verification of the correspondence between the sender and the relevant domain to which it belongs. DKIM and SPF are not two alternative techniques but, rather, complementary. It was standardized in 2011 with RFC 6376.
» Domain-based Message Authentication, Reporting, and Conformance (DMARC): this is an email message validation system. It confirms the identity of the sender and was developed, primarily, to counter email spoofing. The characteristics of DMARC were defined in RFC 7489 of March 2015.
These technologies perform a series of validation checks on the header of the mail message and are able to discover any anomalies. They do, however, require proper setup when installing anti-spam in order to avoid overly restrictive (too many blocked emails) or too lenient effects.
So, in conclusion, it is important to implement an evolved anti-spam which can handle these checks, but it is not enough.
Action should also be taken on the antispam setup panel (this should be done by corporate IT or the external vendor who supplied and installed the anti-spam software) in order to set the correct SPF, DKIM, and DMARC parameters.
Particularly important for blocking spoofing is DMARC, since the SMTP protocol does not natively provide a verification system on the “From:” field.
With DMARC, it is possible to tell a domain owner explicitly what to do with email messages that have the same domain as the sender but do not meet certain IP provenance (defined via SPF) and authentication (DKIM signature) criteria.
In this way, it is not the receiving server that has to decide what to do with the message but rather follows to the letter what is specified in the DMARC DNS record.
The advantage of DMARC is that it makes it possible to define – directly by the sender (i.e., the domain owner) – how receiving servers should treat messages coming from his or her domain, whereas previously it was the recipient’s anti-spam to decide for itself whether that message was really who it said it was or not.
5. The author
Giorgio Sbaraglia, an engineer, provides consulting and training in information security and privacy.
He teaches courses on these topics for many leading Italian training companies, including ABIFormazione and 24Ore Business School.
He is the scientific coordinator of the master’s program “Cybersecurity and Data Protection” at 24Ore Business School.
He is a member of the CLUSIT Scientific Committee (Italian Association for Information Security) and an “Innovation Manager” certified by RINA.
He holds DPO (Data Protection Officer) positions at various companies and professional associations.
He is the author of the books:
» “GDPR kit di sopravvivenza” (Editore goWare),
» “Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” (2a edizione 2022, Editore goWare),
» “iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” (Editore goWare).
He is a contributor to CYBERSECURITY360 , Cybersecurity group’s specialist publication.
He also writes for ICT Security Magazine, for AGENDA DIGITALE, and for CLASS magazine.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







