How to protect yourself from Hackers: what must our approach be for defending a cyber threat and for Cyber Security solution
To be able to fend off a cyber attack that today is ever more aggressive and sophisticated we must be capable – even before choosing technological solutions – of adopting the correct approach, to have the right defensive posture that takes into consideration how the attacker operates. The attacker, that should be correctly defined as a ‘cyber-criminal’ more than hacker, has the advantage of their first moves: surprise attacks.
We don’t know when they will attack and – above all – where and how they will attack. In my activity as a consultant, I like to represent this condition by using a simple example: for an attacker it would be sufficient that a user clicks on an email, for an IT manager it would be sufficient that no user clicks on an email.
From this very simple example it is evident that for defence purposes it is determining to ‘think how the attacker would think’.
This concept – fundamental for the correct approach in cyber security – is expressed in a very efficient way in the celebrated manual ‘The art of war’, written by the general and Chinese philosopher Sun Tzu 2500 years ago, with the phrase: ‘Those who know their enemy as well as knowing themselves should not be afraid of having a hundred battles’ which we have cited in a precedent article.
>> FlashStart protects you from a vast gamma of threats and blocks the access to harmful sites ? Request a quotation or try it now
1. The fundamental principles of cybersecurity
Let’s have a look at what the correct procedures are on which we have to base an efficient cybersecurity architecture and solution.
We have spoken of – not by chance – ‘architecture’ because cyber security cannot be constructed with isolated measures and technologies, instead with the adoption of action between them that is tightly coordinated and interdependent. The first concept to keep in mind is that of ‘layered security’, security done on multiple layers.
I will explain, in a simple but very efficient way the famous Kevin Mitnick with the image of the well known sweet M&M that are hard outside… but soft inside!
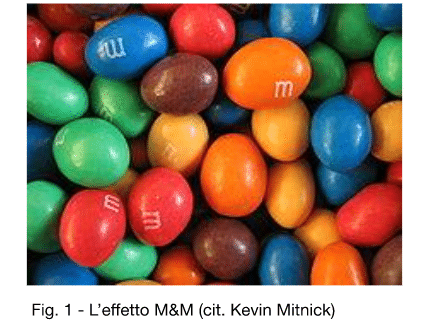
What does this image mean? Very simply, that once you have broken the shell that has been constructed outside, there are no other shells, all that is left is the soft part. In cyber security we must not commit this error but instead adopt a defence on multiple layers: the attacker could manage to break through one layer of defence but then they would find another, then another!
Another essential principal to apply is that of Zero Trust Architecture (ZTA) that we have covered in this article.
The traditional techniques of protection – adopted up until now by companies – are now out of date and not efficient enough to defend from new threats that are coming out of the net.
It is time to change the defence approach of company cyber systems, with a radical change in paradigm and a defence model that is in fact a complete architecture, not leaving out any area from protection.
Over the last years – and sadly even today for many companies! – the attention has been mainly concentrated on PREVENTION, on protective measures.
Trying to stop the attacker of entering and violating the cyber system.
However, today’s scenario of threats and TTP (techniques, tactics and procedure) asks that you consider aggressive attacks that could knock down our defences and should be identified and dealt with as soon as possible: this is the concept of DETECTION, something we should put into action by using very strong instruments.
To represent this situation, we will cite the phrase of John T. Chambers, ex CEO of Cisco System: ‘There are two types of companies: those that have been hacked and those that don’t know they have been hacked’.

The attention must be put also on picking up incidents, to be able to deal with them as soon as possible, reducing damage to the minimum. Today the most terrible attacks are known as APT (Advanced Persistent Threat): they are sophisticated attacks that are also extremely targeted, they start with the intrusion of cyber criminals into the company network that has been put into the sights.
They are advanced because they use techniques of very advanced hacking with multiple attack carriers.
They are persistent because their elevated sophistication level makes them difficult to detect, months could pass between the initial attack and detection with eventual neutralization.
This temporary interval is defined as ‘window of compromise’ or ‘dwell time’ and is usually superior to 220 days. Once the attack has been detected, it takes roughly 75 days for the ‘remedy’, to sort out the damages caused by the attack.
The APT attacks are typically developed in seven phases:
» Reconnaissance (Information Gathering): this is the phase in which the attacker invests the most time and resources, that is because it is exactly that which will determine the success or failure of the attack. There are also used OSINT (Open-Source INTelligence) techniques for collecting information on the target;
» Intrusion onto the network (Exploitation): generally, the human factor comes into play, by using social engineering techniques such as phishing, baiting, spear phishing, watering hole (these are the very same techniques that are also used on smaller targets, also relying on the human factor, something that cannot be mentioned enough!). They can also use exploit kits, SQL Injection techniques, XSS or ‘brutal force’ attacks;
» Identity theft (credential dumping): once the attackers have gained access to the system under attack they will try and penetrate as deep as they can. They run the c.d. Privilege Escalation: with lateral movements they try and obtain the most important administrative credentials. To do this they use specific tools such as: Mimikatz (https://github.com/ParrotSec/mimikatz) and many others, easily obtained on the infinite world of the web;
» Malware installation: once the attackers have entered, they connect to their server C&C (Command&Control) to download the malware with which they will gain control of the system and finalise the attack. This kind of software is defined as RAT (Remote Administration Tool, see Glossary) and is used for taking control of targeted systems;
» Access maintenance: creation of a back door: this is a solution technique that keeps open the access of a system by avoiding the usual protection mechanisms. RAT is therefore used for installing a back door, this allows the attackers to be able to gain access to the system whenever they like;
» Data exfiltration: data theft is the true objective of the attack, therefore the attacker will try to identify and steal the CVD (Critical Value Data), using also scripts for an automatic search. Once identified they need to extract this data which must be done in the most ‘silent’ way possible, thus not being noticed by the ‘detection’ system of the victim;
» Persistence (Covering Tracks): finally, the attacker will try and remain inside the system for as long as possible (even for months, as we have seen), without being spotted by the defence systems. They will therefore use techniques of manipulation and cancellation in the system log, cancelling data and software that was used in the attack.
The TTP (technique, tactics and procedure) utilised during the various phases of the attack are generally noted and repeated: every attacker has their own modus operandi. Therefore, when protecting yourself against hackers you must know these TTP (‘Know your enemy’ cit. Sun Tzu).
A useful font of attack knowledge is the Adversarial Tactics, Techniques and Common Knowledge (ATT&CK) project from MITRE, a group of non-profit researchers that work with the American government. ATT&CK is a knowledge base that has been built upon the study of millions of cyber-attacks in the real world.
Mitre ATT&CK categorize cyber threats based around various factors, like the tactics used for infiltrating the IT system, the type of vulnerability of the system exploited, the malware instruments used and the criminal group associated with the attack. By consulting this we can see and know the different tactics used for every phase of the attack, from Reconnaissance (phase one) right up to Privilege Escalation and Persistence and many others.
On the same site we will also find the connections between the TTP (classified with the letter T and a numeric code) and the threat actors that are utilised (classified with the letter G and a numeric code): just as we mentioned, every attacker has their own typical modus operandi that is often recognisable.
Mitre ATT&CK also offers other information: for every TTP there is a list of ‘Mitigations’ (classified with the letter M and a numeric code) as well as the Detection instruments (classified with the letters DS and a numeric code).
2. The protection and detection measures
Thanks to this knowledge, we can choose to adopt the cyber security solution of protection, detection and mitigation of the attacks.
The first indispensable phase is that of the cyber risk assessment: we must analyse the risks that we are running when our cyber system is exposed, evaluating every aspect of the architecture adopted.
In other words, taking examples from the measurements that we adopt when looking after our health: there is no sense in taking medication if first we have not undergone analyses and medical diagnosis.
Analysing and identifying the risks, we then have to define the measurements of mitigation by using the priority criteria (firstly the risks that are classified as most important).
It is also good to know that the traditional ‘signature based’ antivirus software is no longer enough, that is because today’s attackers adopt the so called ‘polymorphism’ technique: to manage in tricking the antimalware all that they need to do is create a code that is unknown to it. All this can be done in a decisively simple way: you don’t need to construct a completely new malware, all you have to do is modify the signature of an existing one and the antivirus will no longer be capable in detecting it.
Therefore, we have to adopt advanced detection systems such as EDR (Endpoint Detection and Response) or – even better – XDR (Extended Detection and Response): the difference is that whilst the EDR operates on the endpoint, the XDR instruments control the security of the entire company infrastructure.
The utility of these EDR/XDR systems derive from one fact: any attack creates noise.
To know how to recognise this noise, which is a symptom of the attack in act, enables you to intervene quickly with a reaction from the defence system of the company infrastructure.
The key to heighten your defence security level is to understand what is hiding behind the noise that, sooner or later, every hacker will produce with their actions.
This can be done by using the EDR/XDR systems but it is still not sufficient. Once the attack noise has been detected, we must filter it and clean it of any insignificant noise (background noise for example) so we can concentrate on that which could present a real attack.
The information that EDR/XDR detects must be correlated and analysed. Today this is possible by using Machine Learning (ML) along with Artificial Intelligence (AI) from the intelligence threat motor that has been realised by the makers of EDR that is capable of cataloguing and clustering millions of events along with their typical behaviours, thanks also to ‘User Behaviour Analytics’.
The correlation and analysis of the events detected by EDR/XDR can be done by a SIEM (Security Information and Event Management) system that – apart from events coming from the EDR – collects and correlates also the events coming from other fonts such as a firewall, DNS server, IDS (Intrusion Detection System), IPS (Intrusion Prevention System), WAF (Web Application Firewall).
But who analyses the large amount of data that SIEM collects and correlates?
Who decides how to intervene in the case of a suspected attack?
There is no point in having lots of information – generated by the instruments that we have mentioned – if we are not capable of managing it.
To complete this company architecture we can use our internal IT resources, or even get external help, such as an SOC (Security Operations Centre).
SOC is a security analyst unit that manages and evaluates all of the data that is collected by instruments such as EDR, XDR, SIEM etc.
A company can even get their own internal SOC, however this is very costly so it is usually only done by very large organizations.
More frequently companies go to external SOC’s that are connected to MSSP (Managed Security Service Provider).
This solution offers the advantages of having resources and advanced competence, control instruments that are always up to date and a 24/7 service. We should never forget that attackers often try to hit their targets at the very moment that a company have staff shortages or are even closed, for example of a night or during the weekend.
Therefore, the protection should be active always!
The architecture that has been described represents the cyber security solutions that nowadays every company should adopt, going further than the usual and very simple antivirus programs that have now been overcome.
3. Other important measures
We will note – in conclusion – the other measurements necessary for constructing an architecture of complete security that is up to date.
Disaster Recovery Plan (DRP), the plan that every company should have in readiness to affront any type of cyber incident. At the base of everything there should be an analyses, starting with these questions:
» How important is my data?
» How much data can I potentially lose without creating a damage to my company?
» How much time can I lose replacing my data before I sustain damages?
From these evaluations (Risk Assessment) we will be capable of understanding:
» Which data should be backed up?
» How frequently should we perform back-ups (every hour, day, week…)
» What type of back up should we choose (NAS, cloud, tapes etc)
» Obviously based around cost/benefit evaluations
Adoption of advanced Antispam systems: it is noted that emails represent, even today, the principal vehicles of attack.
Thus an efficient antispam represents an indispensable protection measure. However, an antispam could result in being quite inefficient if it is not correctly set up. We should set up correctly the parameters and relative settings of the control protocols that the antispam uses in particular:
» Sender Policy Framework (SPF): this enables you to verify if an email that has been sent to you from a domain is effectively from the hosts of the domain in question. As defined by the RFC 7208 standard.
» DomainKeys IdentifiedMail (DKIM): permits the owners of a domain to add a digital signature through a private key to electronic post. This has been standardised in 2011 with the RFC 6376.
» Domain-based Message Authentication, Reporting and Conformance (DMARC): this is a message validating system for electronic post. It has principally been developed for controlling spoofing emails. The DMARC characteristics have been defined as RFC 7489 in March 2015.
4. What have we forgotten?
‘The human factor is truly the weakest link in security’ (cit. ‘The Art of Deception’ Kevin Mitnick – 2022).
We know that over 90% of cyber-attacks are caused by HUMAN ERROR, therefore it is indispensable FORMATTING the users that will utilise the cyber devices.
The formation is also required by GDPR Art. 39 – Task of the Data Protection Officer (DPO):
The data protection officer is answerable to the following tasks:
b) … the awareness and formation of staff that will participate in the treatment connected to control activities;
Therefore, any company – large or small – should provide periodic formation programs on cyber security, for transforming the user from being ‘the weakest link in the security chain to being the first line of defence’.
5. The author
Giorgio Sbaraglia, an engineer, provides consulting and training in information security and privacy.
He teaches courses on these topics for many leading Italian training companies, including ABIFormazione and 24Ore Business School.
He is the scientific coordinator of the master’s program “Cybersecurity and Data Protection” at 24Ore Business School.
He is a member of the CLUSIT Scientific Committee (Italian Association for Information Security) and an “Innovation Manager” certified by RINA.
He holds DPO (Data Protection Officer) positions at various companies and professional associations.
He is the author of the books:
» “GDPR kit di sopravvivenza” (Editore goWare),
» “Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” (2a edizione 2022, Editore goWare),
» “iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” (Editore goWare).
He is a contributor to CYBERSECURITY360 , Cybersecurity group’s specialist publication.
He also writes for ICT Security Magazine, for AGENDA DIGITALE, and for CLASS magazine.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







