The Zero Trust Architecture (ZTA) model
Today the Zero Trust Architecture (ZTA) model is the new defense paradigm, which companies must aim for in order to grant the security of their IT infrastructures. The concept of “perimeter to defend” has been surpassed.
1. Why Zero Trust Architecture (ZTA)
The IT infrastructure of companies has become more and more complex.
A single firm can manage several internal networks and remote offices with their local infrastructure, remote and/or mobile connections and cloud services.
Traditional protection techniques – that have been adopted until now by companies – result obsolete and not efficient anymore in contrasting threats coming from the web.
There is therefore a need for a change in the defense approach to company IT systems, with a radical change in the paradigm.
This is why today we talk more and more about the Zero Trust Architecture (ZTA) model, a term that has become current. It is not a “fashion”, as somebody may think, but a necessity.
2. The “Theorem of the Fort” is not valid anymore
Until just a while ago the company – with its IT systems – was perceived and represented as a “fort” surrounded by protection walls: the good guys were inside while the bad guys remained out.
This is why we could talk about “perimeter to defend”: the walls of the fort were the perimeter that represented a separation barrier between the company and the attackers. The concept of “perimetral security” (the logic of the fort) closely reminds the “front” doctrine of the First World War: continuous lines that limit what is inside and is protected, from what is outside and is insecure and threatening.
The epigone of this strategy (although it is not the only example) is the sadly known Maginot line.
Today this model has been overcome and, indeed, we talk about “Deperimeterization”.
The growing complexity of company nets and systems has gone beyond the traditional methods of network security based on the perimeter, since a sole perimeter, easily identifiable, does not exist for the company anymore. Network security based on the perimeter has also proven to be insufficient, since once the attackers break the perimeter, lateral movement within the network has no more obstacles.
In other words: perimetral protection systems, although more and more sophisticated and efficient, are nevertheless exposed to being bypassed by adversaries that are sufficiently advanced, financed and determined.
This radical change in the defense model has become even more necessary given the “everywhere workplace” practice that has literally nullified the traditional defense perimeters, which are not static and closed inside the company walls anymore, but can be everywhere.
This is even more notable in an era of remote work, with the employees accessing applications and company data using different devices, wherever they are. We can add to this also the more and more widespread use of cloud resources and of resources located in remote data centers.
The perimeter that needs to be defended – if we wanted to try and delineate it – would be the entire world.
3. Better safe than sorry
This simple sentence contains the essence of the Zero Trust Architecture.
There is a need to shift from the fort model to that of the immune system, which uses antibodies to contrast the aggressor.
The defense should shift from the perimeter (that does not exist anymore!) to the devices and users that connect to the web.
The source network for the connection is not important, but rather WHO connects and how trustworthy he is.
“Inside” and “Outside” have no meaning in terms of security anymore.
The choice of the Zero Trust Architecture model is important also because today we have to be aware that the danger can stem also from within, from the users themselves.
Deeming all the inside users trustworthy is a de-facto mistake that we cannot afford anymore.
Cyber attacks and accidents can also be caused – and much more often so than what you could think – by intentional actions carried out by malicious users (the so-called “malicious insiders”), who act with the aim of damaging the company or stealing data.
But they could also be caused by simple mistakes made by the employees themselves ( the “unaware” ones), who because of lack of attention or of knowledge carry out actions that open a door for the attacker (social engineering, phishing, etc.). From that moment onwards, that user becomes a threat to the company.
A first step towards company security is to train the employees on the dangers connected to the Internet and to adopt a system of intelligence based on the cloud like the one offered by FlashStart, which filters at the DNS level access to malicious and dangerous websites and is able to protect also the remote connections of their employees. We will later see what more the Zero Trust Architecture model implies at the structural level.
>> You can activate the FlashStart® Cloud protection on all sorts of Routers and Firewalls to grant the safety of your desktop and mobile devices and of the IoT devices on local networks
The zero trust security model implies that there is no implicit trust towards resources or user accounts based exclusively on their physical or network position (meaning, local networks compared to the Internet) or based on the property of resources (company or personal). Authentication and authorization (both of the subject and of the device) are distinct functions executed before a session with an employee is established.
Zero trust is an answer to the trend of including remote workers, the use of personal devices (BYOD, Bring Your Own Device) and cloud-based resources that are not inside a company network.
Zero Trust Architecture is focused on resource protection (resources, services, work flows, network accounts, etc.), not on network segments, since the network’s position is not seen as the main requisite for resource protection any longer.
For these reasons, no user or device can have unlimited access to company resources: even after the authentication stage, his access privileges are provided in a granular way and continuously verified.
Hence, a zero trust architecture that is correctly implemented moves the burden of data protection from inside the company towards each user, device and application that tries to access the company network.

4. Zero Trust Architecture: the NIST guidelines
Speaking about ZTA, we cannot disregard the guidelines provided by the NIST on this topic.
NIST (National Institute of Standards and Technology) is an agency of the government of the United States of America that deals with the management of technology. It is part of the DoC, Department of Commerce. It was born in 1901 as “National Bureau of Standards” (NBS) and became the “National Institute of Standards and Technology” in 1988.
It is institutionally tasked with developing standards and is the first institute in the world for the production of standards in the realms of technology, IT and cybersecurity.
NIST’s publications are not cogent in Europe, but given how authoritative the institute is, they very often become de-facto standards.
The NIST document dealing with Zero Trust Architecture is the Special Publication SP 800-207 “Zero Trust Architecture”, published in August 2020 and that can be downloaded for free in English at this link.
This publication examines and describes the ZTA, its logic components, the possible implementation scenarios and the threats.
Furthermore, it presents a general roadmap for organizations that wish to move towards a zero trust design approach.
It is highlighted that the ZTA is not a single architecture but a set of guiding principles for the design of the company IT system and for the projects that can be implemented to improve the security posture of all types of organizations.
>> FlashStart is Multi-tenant and fast to install ? Request a quotation or try it now
The shift to the ZTA is therefore a path that needs to be designed as a whole, since it is about how an organization perceives and faces risks.
It cannot be realized simply as a mere substitution in technologies, it’s a process.
This is why NIST suggests to try and implement in an incremental way the principles of ZTA, the changes in the process and the technological solutions that protect data resources in the activities of a company.
Section 2 of the SP 800-207 lists the basic principles of ZTA:
» The whole private company network is not implicitly considered a trustworthy area. Resources should always behave as if an aggressor was present in the company network, and communication should take place in the safest way possible. This implies actions such as the authentication of all connections and encryption of all traffic.
» Devices in the network may not be owned or configurable by the company. External visitors and/or collaborators can consider resources that are not owned by the company and that will need to access the network in order to carry out their role. This includes BYOD (bring-your-own-device) policies, which allow a company’s employees to use personal devices to access the company resources.
» No resource is intrinsically trusted. All resources must be evaluated through a PEP (Policy Enforcement Point) before it is allowed to access the company resources. This evaluation should go on for as long as the session lasts. The subject’s credentials themselves are not sufficient to authenticate the device as belonging to a company employee.
» Not all company resources are on infrastructures that belong to the company. Resources include remote company subjects as well as cloud services.
» Remote subjects and company assets cannot completely trust their local network connection. Resources should consider that all the traffic is monitored and potentially modified. All requests for connection should be authenticated and authorized, and all communications should be carried out in the safest possible way.
» Resources and work flows that move in and out of the company infrastructure should respect a policy and an adequate security posture. Resources and work loads should retain their security posture when they move towards or away from company properties. This includes the devices that move from company to non-company networks (for example, remote users) and also work flows that shift from on-premise data centers to the cloud or to other services located outside the company.
The following picture, taken from the SP 800-207, represents the access model that should be applied in a ZTA.
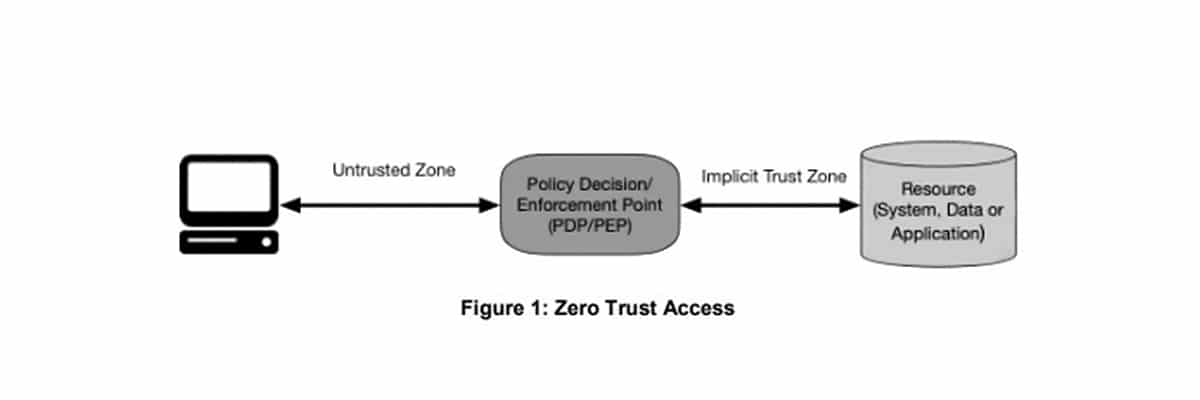
Access is permitted to the resource through a policy decision point (PDP) and a corresponding policy enforcement point (PEP).
The system must grant the authenticity of the subject and the validity of the request. PDP and PEP provide an appropriate judgment to allow the subject access to the resource.
This implies a fundamental concept: zero trust is applied to two distinct areas: authentication and authorization:
» authentication: what gives you the right to access company resources;
» authorization: what resources are you allowed to access.
In general, companies must develop and maintain dynamic policies based on risk for access to resources and set up a system to grant that these policies are correctly and coherently applied for the single requests for access to the resources.
This means that a company should not trust the implicit reliability, whereby if a subject satisfies a basic authentication level (such as access to one resource), all the subsequent requests for resources are considered equally valid.
Within this ZTA architecture, an important role is played by what the NIST defines as a “policy enforcement point” (PEP), hence the application point for policies.
This system is responsible for enabling, monitoring and in case terminating connections between a subject and the company resources.
The PEP communicates with the PA (Policy Administrator, who defines the company security policies) to forward the requests and/or receive the policy updates from the PA.
On top of the PEP, there is the “trust zone”, which hosts the company resource.
Other fundamental factors contribute to the application of the Zero Trust Architecture:
» Enterprise public key infrastructure (PKI): this system is responsible for the generation and recording of the certificates released by the company to resources, subjects, services and applications. It includes also the global ecosystem for the certification authorities, which can be integrated or not with the company PKI;
» ID management system: it is responsible for the creation, management and dismissal of the accounts of the company users and of the identity records (for example, an LDAP server – Light Directory Access Protocol).
This system includes the necessary information on the subject (for example, name, email address, certificates) and other company details like the role, access attributes and assigned resources. It often uses other systems (like a PKI) for artifacts associated with the user accounts and can be part of a bigger federal community and can also include employees outside the company or connection with outside resources for collaboration purposes.
In conclusion, the Zero Trust Architecture is a complex process that implies coordinated activities.
The aim is that company resources should not be reachable without accessing a PEP. Company resources cannot accept random connections coming from the Internet. Resources accept personalized connections only after a client has been authenticated and authorized. These communication paths are set up by the PEP.
This prevents aggressors from identifying their targets by scanning and/or launching DoS attacks against resources that are located behind the PEPs.
>> FlashStart is a leader in competitiveness ? Request a quotation or try it now
5. The author
Giorgio Sbaraglia, engineer, is a consultant and trainer on the topics of cyber security and privacy.
He holds training courses on these topics for numerous important Italian companies, including ABIFormazione and the 24Ore Business School.
He is the scientific coordinator of the Master “Cybersecurity and Data Protection” of the 24Ore Business school.
He is a member of the Scientific Committee CLUSIT (Italian Association for Cyber Security) and an Innovation Manager certified by RINA
He has DPO (Data Protection Officer) positions in companies and Professional Associations.
He is the author of the following books:
» “GDPR kit di sopravvivenza” – “GDPR survival kit” (Edited by goWare),
» “Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” – “Cybersecurity survival kit. The web is a dangerous place. We must defend ourselves!” (Edited by goWare),
» “iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” – “iPhone. How to use it to its full potential. Let’s discover together all the functions and best apps” (Edited by goWare).
He collaborates with CYBERSECURITY360 a specialized online magazine of the group Digital360 focusing on Cybersecurity.
He also writes for ICT Security Magazine, for Agenda Digitale and for the magazine CLASS.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







