
WannaCry 2017: The ransomware that made the world cry
1. WannaCry 2017: a world-famous attack
WannaCry 2017 is still one of the most notorious attacks in the history of computing and cybersecurity. More than six years have passed since it happened, but it should still be considered a very useful and instructive case study.
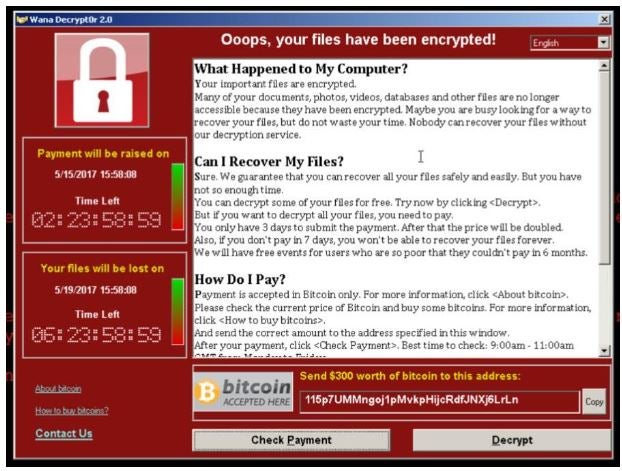
Fig.1 – The warning that appeared on computers affected by WannaCry
I still remember that on that Friday, May 12, 2017, the news of the WannaCry attack was the lead story on all the prime-time newscasts across Europe. So, WannaCry 2017 was not only an event for cybersecurity insiders, but it also affected the generalist media, in addition to organizations and businesses in every nation.
1.1 Why did all this happen?
WannaCry, aka “I want to cry,” is also called WanaCrypt0r 2.0. In May 2017, precisely on Friday the 12th, this ransomware crippled computers halfway around the world, thanks to a flaw found in the Windows SMB feature, a known “bug” and also already “blocked” by the Redmond company with a patch, number MS17-010. The ransom demand was $300, to be paid in Bitcoin to one of three accounts specified in the ransom demand (see Figure 1 – The WannaCry ransom demand message).
Many researchers in the field considered WannaCry “an attack of unprecedented proportions.” Kaspersky Lab has recorded more than 300,000 attacks in 150 nations, including Russia, China, Italy, India, Egypt, and Ukraine. Europol, an EU agency involved in fighting crime, spoke of “an unprecedented attack that requires international investigation.”
One of the countries most severely affected was the United Kingdom, where WannaCry crashed at least twenty-five hospitals and put the British health care system in crisis. The attack caused significant disruption to patient care, such as the cancellation of about 19,000 appointments, including operations, and the disruption of IT systems for at least one-third of all of the UK’s National Health Service (NHS) hospitals. Affected hospitals were forced to send emergency room visitors to other hospitals.
There is no firm evidence of people who died as a result of the WannaCry attack, but a study by the Owen Graduate School of Management at Vanderbilt University found an increased mortality rate related to the attack: up to thirty-six additional deaths for every 10,000 heart attacks that had occurred – statistically – every year in the hundreds of hospitals surveyed.
This was made possible because many thousands of computers in UK hospitals were still running Windows XP (a system declared “end-of-life” and no longer supported by Microsoft since April 2014). A survey conducted by Motherboard in 2016 had found at least forty-two National Health Service (NHS) facilities that were still using XP.
However, attacks have been reported throughout Europe and the rest of the world, among others, Nissan and Renault in France, the telecommunications company Telefonica, Iberdrola, and banks BBVA and Santander in Spain, FedEx in the U.S., and many others. In Germany, computers at Deutsche Bahn (the German railways) were affected. In Japan, it was Hitachi, Nissan, and East Japan Railway’s turn. In Russia, the attacks affected RZD (Russian Railroad), VTB bank, Megafon. Italy also joins the list, with Bicocca University in Milan (which was reportedly attacked through a usb stick containing the malware).
It is estimated to have cost, worldwide, between $4 billion and $8 billion and to have caused an estimated damage of more than $100 million to the British National Health Service .
Yet, despite spreading like wildfire, WannaCry was considered an economic flop: the amount of revenue collected by cyber criminals was around $100,000.
We detected this data two weeks after the attack by analyzing the movements of the three Bitcoin accounts used and identified in the ransom note and which are as follows:
» 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
» 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
» 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
This is a modest sum, especially given the fact that malware generally aims precisely for a ransom payment. This suggests that the attack was not done for money, but more likely for destabilizing or demonstrative purposes.
It now seems certain that the attack originated from North Korea, with its hacker group known as Lazarus (other group names: Hidden Cobra, Guardians of Peace, APT38). This is alleged by Symantec and Kaspersky Lab, which found some similarities in the malware’s code with previous attacks: the one on the Central Bank of Bangladesh in 2016 (the largest cyber heist ever, $82 million stolen), but especially the one on Sony Pictures Entertainment, the production company attacked for having produced “The Interview,” a satirical film targeting North Korean leader Kim Jong-un.
In 2018 WannaCry struck again: in March, Boeing, the world’s largest aircraft manufacturer, was attacked. The company confirmed the incident but specified that the problem affected only a limited number of systems in the commercial division, not those in the manufacturing plant.
2. WannaCry 2017: the attacking technique
The distinction of WannaCry, compared to other more classic types of ransomware, is that it is a malware consisting of two components that operate in succession:
Stage 1: An exploit was used (we discussed exploits in this article) that exploited a vulnerability in SMVB v.1 (a network file sharing protocol, Server Message Block, used by Microsoft Windows systems) to attack the target computer. The vulnerability is classified as CVE-2017-0144 and had already been closed by Microsoft on March 14, 2017, but not in WinXP and Windows Server 2003 systems, which had not been supported since 2014.
We stipulate that only version 1.0 (SMBv1) is vulnerable: it is a very old (and very insecure) protocol, born more than twenty years ago and already present in XP. The SMBv2 (introduced in 2006) and SMBv3 (born with Windows 8) versions do not suffer from this vulnerability.
In this way, WannaCry spread automatically to other computers, which explains the very high rate of its circulation.
One important and disturbing matter: WannaCry used the exploit called EternalBlue, which appears to have been created by NSA (the U.S. National Security Agency). However, NSA had the newly created exploit “stolen” by a hacker group called The Shadow Brokers (TSB) which made it available on the darkweb in April 2017 and which the attackers used.
Stage 2: An actual ransomware performs file encryption. Ransomware-type malware has been around for about ten years now (and is aimed at extorting money: charging a ransom to get back one’s files that have been encrypted). Never, however, had ransomware been propagated so quickly, thanks precisely to the EternalBlue exploit.
According to Microsoft, there are at least two alleged attack vectors, which Microsoft points to as “highly probable”:
» The first – and most trivial – are the usual phishing emails, or via USB flash drives. These are the most typical and frequent attack vectors, exploited by most ransomware attacks;
» The second scenario is the one already mentioned, using exploits that take advantage of the SMB protocol vulnerability on outdated systems.
It is important to note that if the system is affected by the aforementioned vulnerability (CVE-2017-0144, MS17-010 according to Microsoft’s classification), the phishing email is not necessarily needed to be attacked.
In other words: human error is not needed, because the exploit is already able to breach the system by exploiting its vulnerability. It does not have to be the victim who opens the door, because it is the hacker who already possesses the key (i.e., the exploit).
Once it enters a computer on a Windows system (it only takes one!), WannaCry 2017 automatically spreads to other computers (even if not connected to the internet) by exploiting SMB network shares, through communication ports 139 and 445. This explains the (unusual) speed with which it spread.
Then – the second step – it performs an encryption of the files, using 2048-bit RSA asymmetric encryption, based upon a public/private key pair for encrypting and decrypting the files (absolutely unhackable).
As many ransomwares do, with WannaCry the encrypted files are renamed by adding a typical extension, in this case.WNCRY.
For example, an invoice.pdf file will be changed to invoice.pdf.WNCRY.
WannaCry also takes care of deleting Windows “Shadows copies” (to prevent us from recovering data) and goes and writes in some typical system folders, such as:
» %SystemRoot%
» %SystemDrive%
» %ProgramData%
Another feature of WannaCry: because it exploits a vulnerability, the malware is able to install itself, even if the user does not have administrator rights but is merely a user.
3. How to protect oneself
Although WannaCry 2017 was a devastatingly large attack, the prevention and protection measures to be taken are quite basic. We can sum them up in one word: update.
According to Microsoft’s statement (12/05/2017), WannaCry can only affect systems up to Windows 8, if not updated, so those with Windows 10 are not at risk. Older unsupported versions of Windows (e.g., Windows XP and Windows Server 2003) are not protected anyway, because Microsoft no longer provides security patches for those versions of Windows.
4. What WannaCry 2017 has taught us
We have talked about the exploitation of a Windows vulnerability, but, in reality, once again, the real problem is human error.
Many businesses and organizations, in defiance of any cybersecurity norms, have chosen to maintain operating systems that are not only obsolete, but also lacking security updates.
Therefore, WannaCry 2017 was not a new threat that was brought about thanks to some unknown vulnerabilities. No, it was able to strike thanks to carelessness and incompetence on the part of those who should be protecting corporate computer systems.
So, this lesson has not yet been fully comprehended, since today, – six years later – we are still finding vulnerable systems exposed to WannaCry and EternalBlu on the internet. We could easily verify this by querying the Shodan portal (https://www.shodan.io/): over 15,000 computers are exposed running Windows Server 2003 and almost 13,000 running Windows XP, therefore vulnerable to WannaCry because they are visible in the network.
5. The author
Giorgio Sbaraglia, an engineer, provides consulting and training in information security and privacy.
He teaches courses on these topics for many leading Italian training companies, including ABIFormazione and 24Ore Business School.
He is the scientific coordinator of the master’s program “Cybersecurity and Data Protection” at 24Ore Business School.
He is a member of the CLUSIT Scientific Committee (Italian Association for Information Security) and an “Innovation Manager” certified by RINA.
He holds DPO (Data Protection Officer) positions at various companies and professional associations.
He is the author of the books:
» “GDPR kit di sopravvivenza” (Editore goWare),
» “Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” (2a edizione 2022, Editore goWare),
» “iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” (Editore goWare).
He is a contributor to CYBERSECURITY360 , Cybersecurity group’s specialist publication.
He also writes for ICT Security Magazine, for AGENDA DIGITALE, and for CLASS magazine.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







