
The Hidden Web Insidiousness: The DNS Spoofing Attack and How to Protect Yourself
The Domain Name System (DNS) is critical to the functioning of the Internet, converting website names into IP addresses understandable by computers. A DNS spoofing attack, also known as DNS cache poisoning, exploits vulnerabilities in DNS to divert Internet traffic to fraudulent websites, potentially leading to the theft of sensitive information.
1. What is DNS Spoofing attack
The Domain Name System (DNS) is a crucial element of the Internet infrastructure, acting as a digital phone book that associates domain names with the IP addresses of the servers that host Web sites. When a user types a Web address into their browser, the DNS system translates that domain name into an IP address, allowing the browser to connect to the right Web server. This seemingly simple process is fundamental to the user experience on the Internet.
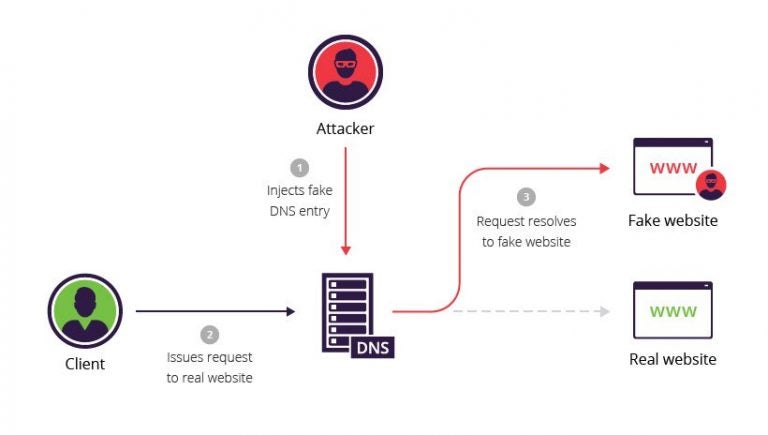
However, the decentralized and open structure of DNS makes it vulnerable to various types of attacks, including DNS spoofing. DNS spoofing attack, also known as DNS cache poisoning, is a cyber-attack technique in which an attacker introduces fake data into the cache of a DNS resolver. This attack is designed to divert users from a legitimate site to a malicious one, often created to replicate the original site with the intent of collecting sensitive information, such as login credentials or financial data.
Mechanism of the Attack.
A DNS spoofing attack begins when an attacker manages to insert a false response to a DNS query into a DNS resolver. This can be done through various techniques, such as intercepting communication between the DNS resolver and authoritative DNS servers, or exploiting vulnerabilities in the DNS resolver software to inject malicious DNS responses. Once the fake response has been accepted and cached by the DNS resolver, all future requests for that particular domain name will be redirected to the IP address specified by the attacker, as long as the malicious entry remains in the cache.
Goals and Motivations
The goals of a DNS spoofing attack can vary widely, from sending users to phishing websites that mimic banks or online services to steal login credentials, to injecting malware into the systems of users who visit the bogus site, to disrupting access to critical services by distributing fake network information. The motivation behind these attacks can be financial, political, or simply a desire to create disruption and disorder.
Security Implications.
The security implications of a DNS spoofing attack are significant. Users can become victims of identity theft, loss of financial data, or malware infection without even realizing they have been directed to a malicious site. In addition, trust in the DNS system and overall Internet security is eroded as users can no longer be certain that they are connected to authentic Web services.
In conclusion, the DNS spoofing attack represents a sophisticated and dangerous cyber threat that exploits vulnerabilities in the DNS system to compromise the security and privacy of online users. Understanding this attack and its dynamics is essential to develop effective strategies to mitigate the risk and protect network infrastructure and sensitive information.
How to prevent DNS spoofing attacks?
Prevention and detection of DNS spoofing attacks are critical to maintaining the integrity and security of computer networks. DNS spoofing attacks can be sophisticated and difficult to detect, but there are several strategies and tools that can help mitigate this risk. In this chapter, we will explore security measures that can be taken to protect networks from DNS spoofing attacks.
Implementation of DNSSEC
One of the most effective measures to prevent DNS spoofing attacks is the implementation of DNS Security Extensions (DNSSEC). DNSSEC is a set of extensions to DNS that provides authentication of DNS data sources, data integrity, and explicit denial of existence. Using a digital signature-based chain of trust, DNSSEC protects against the injection of false data into the DNS system. However, its effectiveness depends on widespread adoption along the entire DNS resolution chain, from root servers down to the resolvers used by end clients.
>> FlashStart protects you from a wide array of threats and blocks access to malicious sites. Try it now: working with the internet has never been so secure!
2. DNS Resolver Security
Network administrators should ensure that the DNS resolvers used by their networks are configured correctly and are updated with the latest security patches. This includes limiting DNS recursion to internal clients only and implementing rate limiting for incoming DNS requests, which can help mitigate Denial of Service (DoS) attacks that exploit the resolver as an amplifier.
DNS Traffic Monitoring and Analysis.
A proactive approach to security includes constant monitoring of DNS traffic to identify unusual patterns that might indicate an attempt at DNS spoofing. Advanced traffic analysis tools can help detect anomalies, such as a sudden increase in resolution requests for specific domains or unexpected changes in DNS traffic patterns, that may signal an attack in progress.
User Education.
Educating users about the risks associated with phishing and other forms of social engineering is crucial, as awareness can significantly reduce the risk of users unintentionally visiting malicious websites. Education should include the importance of verifying the authenticity of websites, especially those requesting sensitive information.
Use of VPN and Secure DNS Services.
Using virtual private networks (VPNs) and configuring devices to use secure and trusted DNS services can offer an additional layer of protection. DNS services such as those that offer end-to-end encryption (e.g., DNS over HTTPS or DNS over TLS) can prevent attackers from intercepting or manipulating DNS queries.
Regular Updates and Patches
Keeping operating systems and network software up-to-date with the latest security patches is essential to protect against vulnerabilities exploited by attackers to conduct DNS spoofing attacks. System administrators should follow best practices for patch management and actively monitor security alerts related to DNS system software.
>> FlashStart protects you from a wide range of threats and blocks access to malicious sites → Try it now
3. Conclusions
DNS spoofing attacks represent a significant threat in the cybersecurity landscape, exploiting inherent vulnerabilities in the Domain Name System to hijack users to malicious sites, with potentially devastating consequences in terms of theft of sensitive information, distribution of malware, and compromise of data integrity. However, through a thorough understanding of the attack mechanisms and the implementation of effective defense strategies, the risks associated with this form of attack can be mitigated.
Adopting DNSSEC, securing and regularly updating DNS resolvers, carefully monitoring DNS traffic, educating users about the dangers of phishing, and using secure VPNs and DNS services are cornerstones in building a robust defense against DNS spoofing attacks. These measures, complemented by diligent patch management and awareness of the latest security threats, can greatly strengthen the resilience of networks and the security of online users.
Cyber security is a constant battle, with attackers constantly refining their techniques and security professionals developing new defenses. Protection against DNS spoofing attacks requires ongoing efforts, continuous knowledge updates, and collaboration among organizations, Internet service providers, software developers, and end users. Only through this joint effort can DNS integrity and the security of the digital ecosystem be ensured.
In conclusion, as the threat landscape evolves, our defense strategies must adapt as well. Awareness is the first step toward security: understanding the nature and techniques of DNS spoofing attacks is critical to developing effective defense systems. By maintaining a focus on recommended security practices, regularly updating systems, and fostering a culture of security, we can hope to stay one step ahead of attackers, protecting our networks and data from DNS spoofing attacks and maintaining a secure and reliable online environment for all.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







