
Network visibility and cyber security
DNS is the main entry point for cyber attacks. Good network visibility allows cyber threats to be detected and blocked. In this post, we explain FlashStart’s role in providing better network visibility and how, thanks to its DNS filtering, FlashStart is able to block cyber attacks for all of its customers, wherever they are.
1. DNS: the point of entry for malware and cyber attacks
Domain Name System (DNS) technology is what allows each website to be assigned a numeric IP address, which is the true “internet name” of the searched site, intelligible to computers, in order to then redirect the user to the requested destination. In technical terms, DNS technology is what enables “domain resolution,” and, so, we could think of it as the internet’s big phone book, where every name corresponds to a number.
Considering the strategic importance of DNS to the workings of the internet, it is not surprising that hackers have decided to use DNS itself as an entry point to perpetrate their attacks. And not only that. Since the internet has spread greatly in more recent years, the majority of cyber attacks occur precisely through the DNS, which, after having started out as a business tool, can thus become a carrier of cyber threats.
Given the prevalence of these attack techniques, the computer security industry has developed a number of tools aimed at countering this specific problem by proposing DNS filtering systems.
>> FlashStart protects you from a wide range of threats and blocks access to malicious sites ? Request a quotation or try it now

2. DNS filtering: the solution for a safe internet
2.1 The evolution of computer safety
Systems that filter internet contents directly at the DNS level represent an evolution in the cybersecurity landscape. Initially, threats were contained directly on the network. The process involved downloading malicious contents to a physical or virtual appliance, analyzing it, and then neutralizing it on the network so that it would no longer be allowed to create more victims.
Over time, however, internet threats have become increasingly dangerous. This increase in danger has arisen mainly from two trends, both made possible by the advancement of information technology:
» The types of malware that can be transmitted via the internet have increased by leaps and bounds. Today, attackers can choose, from a plethora of attacks, the type that best suits their target, and the target can be either an individual or a single organization (here, we are referring to targeted attacks), or the general public, with massive opportunistic attacks launched in the belief that someone will, sooner or later, fall into the net (here, we are referring to phishing attacks). To learn more about the types of attacks, read our dedicated article.
» The speed with which new attacks are continuously generated has also increased, allowing attackers to try new strategies and means whenever an attack does not achieve its desired results. This speed in the ability to generate attacks leads, in turn, to an increase in the amount of analysis time required to verify threats.
Therefore, there arose the need to work with faster and more flexible systems which are capable of learning from their own experiences and which ensure greater visibility of the network in order to understand any weaknesses and potential entry points into the network.
>> FlashStart is DNS filtering against malware and dangerous contents, continuously updated and available everywhere ? Request a quotation or try it now
2.2 DNS filtering systems
DNS filtering systems were created precisely to address this need for faster controls and constantly updated internet security. Traditionally hardware-based, they have now evolved to the cloud, with obvious gains in terms of time and updates.
These systems are based on two cardinal points:
» The constant scanning of the internet for new threats or evolutions in already known threats. In fact, as mentioned above, hackers are constantly launching new attacks, and so cyber security systems need to keep up with the times in order to ensure their basic function. Continuous updating is, therefore, an essential component of any DNS filtering system and one that any company looking for better protection needs to carefully consider.
» The analysis of threats and their aggregation into blacklists, i.e., lists of dangerous contents that must be blocked. Depending on the system chosen, these lists may be on physical servers and, therefore, require manual updating by the user, who will have to download the latest versions of the software used in order to enjoy up-to-date protection, or they may be in the cloud.
Cloud-based DNS filtering systems, such as FlashStart, allow their users to always enjoy up-to-date protection without the need to download anything or go through lengthy system reboots.
>> FlashStart is totally in the cloud; it is easy to activate and provides up-to-date protection against malware ? Request a quotation or try it now
3. FlashStart: the web content filter that increases your network visibility
3.1 Artificial intelligence and machine learning for up-to-date security
Among the DNS-based web filters available on the market, FlashStart has distinguished itself for its effectiveness. In fact, the product offered by FlashStart is based on artificial intelligence, that is, on a series of algorithms which constantly scan the internet in order to expose new threats. In particular, FlashStart’s artificial intelligence manages to analyze up to 200 thousand new sites every day in twenty-four different languages.
Machine learning mechanisms, then, allow the system to replicate the workings of the human brain and learn from past experience, highlight similar behavior, make connections with the contents of official alert sites and any human corrections. The result is that FlashStart’s artificial intelligence can correctly predict as many as 92.5 percent of domains, leaving out only sites in unfamiliar languages or with insignificant content.
All the contents that have been analyzed in this way are then divided into lists of blockable contents, or blacklists. And FlashStart blacklists make it possible to block not only dangerous contents, such as malware and phishing attempts, but also unwanted contents related to violence or porn, for example, and those that may create distractions. The latter category includes social networks, online shopping sites, and video and music streaming platforms. Read our article dedicated to contents that can be blocked by FlashStart.
>> FlashStart is multi-tenant and readily installed ? Request a quotation or try it now
3.2 FlashStart reporting: analytics thanks to improved network visibility
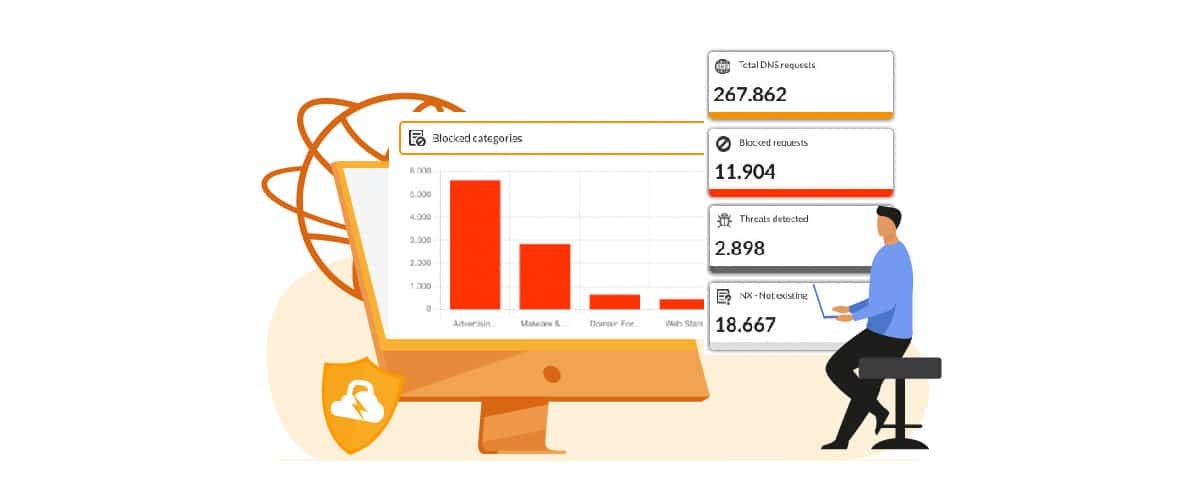
However, FlashStart is not just about making your network more secure. This tool also allows you to increase the visibility of your network, in order to fully understand what the potential entry points are for a malware attack. In fact, FlashStart believes in the usefulness of analytics, of historical data analysis as a basis for future choices, and offers more than a score of standard reports that are always available to its users.
These are reports on network usage based on a six-month history and sorted according to the contents analyzed. Therefore, there are reports on blocked contents based on content category and time slot, based on the country or geographic area to which a requested site can be traced, and specific reports on blocked malware, unwanted contents, and distracting contents.
This wide variety of reports increases the visibility of the network and makes it possible to understand, for example, which users are most prone to risky behavior, while still ensuring that privacy is respected. In fact, FlashStart is fully aligned with the GDPR, i.e., the European Privacy Regulation, and can be refined to ensure compliance with all applicable regulations within individual countries.
>> FlashStart is the web filter that protects over 20 million users ? Request a quotation or try it now
4. FlashStart: network visibility both inside and outside of the company
Finally, FlashStart provides visibility of the network both inside and outside the corporate network. In fact, FlashStart protection can be applied on two levels:
» At the router level: this will ensure DNS filtering of all contents that users want to access from within the corporate network. In fact, once installed at the router level, FlashStart protection automatically covers all devices connected to that network, allowing the network administrator to work with peace of mind.
» At the endpoint level: FlashStart has kept up with the times and developed the ClientShield application to ensure that devices are protected even when they are outside of the corporate network. ClientShield is the ideal tool for those who work remotely, connecting to public or private networks whose security level is unknown, and for those who are constantly on the move.
>> Want to find the right protection for you against malware and dangerous contents? Request a quotation or try it now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







