
Wannacry Ransomware, what it is
The Wannacry ransomeware is a malware that has made history, not only for its diffusion throughout the world but also for its particular type of attack. The Wannacry experience has been very useful for all the producers of cyber-security solutions because if you study carefully and in depth this ransomware you can work out how it has been constructed, the distribution strategy and the effect that it had in a way that will help you guard against any such similar future attacks. You could say that, after Wannacry, cyber protection has never been the same, you cannot however say the same for the sensibility to the theme by private and company users. For this reason it is still very important to ‘create a culture’ from the experience left by the Wannacry ransomware.
>> FlashStart protects you from a wide array of threats and blocks access to malicious sites. Request a quotation or try it now
1. Wannacry ransomware, the story
The Wannacry ransomware, known also as Wannacrypt0r 2.0 is a (crypto) worm type of ransomware. Spread in May 2017, it was responsible for a worldwide epidemic spread over computers with Microsoft Windows. Once in execution mode the virus encrypted the files on the computer and asked for a ransom of hundreds of dollars to decipher them.
Between the 12th and 15th May 2017, this malware infected the computer systems of numerous companies and organizations all over the world. Amongst which Portugal Telecom, Deutsche Bahn, FedEx, Telefónica, Renault, the English National Health Service, the Russian Internal Ministry and the University Bicocca in Milan, just to cite a few of the more important companies and institutions. Also, Wannacry blocked the activities of various hospitals in the U.K. in which the Microsoft Windows system XP was still very present.
At the end of May 2017, the count of infected computers was calculated to roughly 230 thousand throughout 150 different countries, earning it the trophy of one of the most important cyber viruses for damage inflicted. Technically, Wannacry exploited an SMB (Server Message Block) vulnerability through an exploit called EternalBlue. This means that the virus exploited an ‘imperfection’ in the SMB protocol that defines the sharing of files, printers, serial ports and communications by Windows through the networks. The strange thing is that Wannacry seems to have been developed by the NSA (National Security Agency) by the Americans, to attack cyber systems based around the Microsoft Windows operations.
>> FlashStart protects you from a wide range of threats and blocks access to malicious sites → Request a quotation or try it now
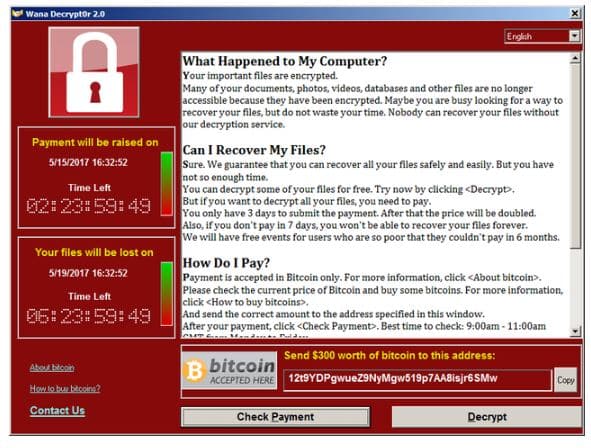
2. How it was propagated
At the beginning it was thought that the Wannacry ransomware was spread through false emails and, after it was installed on the computer, it began infesting other systems that were connected to the same network, without any kind of intervention by other users and also without realising it was happening. In the case of the Biccoca University attack, it seems that the worm spread through the use of a USB stick. This made us understand that Wannacry didn’t in fact propagate through the actions of an unaware worker.
The attack came in succession: first through an exploitation called EternalBlue and after through the ransomware that executed in encrypting the files. EternalBlue activated the encryption of the files blocking their access, adding the extension .WCRY and stopped the re-starting of the system. At that point, in the files named @Please_Read_Me@ there was a request of a ransom, initially of 300 dollars that then doubled to 600, to be paid in bitcoin so the files could be unblocked.
Microsoft, who participated actively in the investigation, declared that Wannacry propagated in two ways:
» Through a phishing email (containing false invoices, credit notes, bills etc) or through USB sticks (just like at the Bicocca University).
» Through direct EternalBlue attacks with an SMB protocol in not updated machines.
EternalBlue exploits a Windows vulnerability that was already corrected by Microsoft on the 14th of March 2017, with a patch called ‘Security Update for Microsoft Windows SMB Server (40133898)’. Sadly, many computers, private and company ones, were not updated, nullifying the security patch distribution that had been realised by the software producers at Microsoft.
Another element that made us understand just how sophisticated Wannacry was, its capability of eliminating backup copies (shadow copies) of Windows and re-write some of the files present in the system folders. Finally, the malware also managed to instal and propagate itself through one simple user account, without any administration privileges.
>> FlashStart’s artificial intelligence guarantees continuously updated protection for your browsing → Request a quotation or try it now
3. Who unleashed the Wannacry ransomware.
Before we get to who was responsible for the attack, we shall point out that the EternalBlue exploit was in fact stolen before by a group of hackers who called themselves The Shadow Brokers and it was published online on the 14th of April 2017.
Even with the number of devices involved it was the media resonance that the Wannacry ransomware wasn’t such a big success in economic terms. Through analysis of the three bitcoin accounts in which the ransom had to be paid, it was calculated that the cyber-criminals accumulated only about 100 thousand dollars against the 300 thousand paid ransoms. It seemed to be more of a demonstration move rather than something to make a big economic gain.
In the beginning it was thought that it was a group of hackers, maybe Chinese or Russian, even if one of the violated sites was in fact Russian. More recently attention has been placed more on a group called Lazarus from North Korea. Two leading security sellers declared that they had recognised a malware code with similarities to past attacks. In particular, that of the Bangladesh Central Bank in 2016 (the biggest ever cyber-attack where 82 million dollars was stolen) as well as that of Sony Pictures Entertainment, attacked because they produced ‘The Interview’ which had been written against the leader of North Korea Kim Jong-un.
4. How to defend yourself from ransomware
Recommended actions after an attack have been:
» Install and run the Wannacry free software to try and decrypt the blocked files.
» Update to the latest versions any present anti-virus software
» Install the bMS17-010 Microsoft update.
Finally, it is highly recommended disactivating the SMBv1, blocking the SMB traffic coming in through the 445 port. After that, isolate the vulnerable and not updated systems and define a process of punctual backups.
Wannacry confronted us with a realisation of facts: too many systems are not up to date or are still using obsolete operating systems or, even, those that no longer have any kind of manutention and therefore the distribution of the patch. Therefore, in this case, the responsibility of the propagation cannot solely be laid on some ‘distracted’ workers who had simply clicked on an infected link or installed an .exe file without knowing what they were doing, instead, more blame can be put on the company IT responsible who hadn’t worried too much about keeping everything up to date.
5. How to protect yourself from cyber-attacks
A DNS Filter for navigating is a web service that, for a small monthly fee, protects the navigation of all devices connected to the same network, at home or in the company. Simply speaking, a DNS filter for navigating controls the links that are clicked before they are reached by the user, if they are inserted into the so-called blacklist the page will not be loaded. This is the most suitable solution for protecting the device from an attack that is coming from an infected link or suspect attachment.
Filters for the navigation through the DNS constantly update and improve. For example, by using artificial intelligence for spotting online threats as well as personalising and setting up automatic blocks.
Other characteristics of the best DNS filters for navigating are dynamic updates of their blacklists and the introduction of functions such as Geoblocking that allows you to block the navigations towards domains and IP addresses that bring about attacks from cyber-criminals.
When choosing a DNS filter for navigating, it is important to consider a supplier who guarantees constant added functions and updates of the database of sites to avoid.
6. How DNS filters work
Well, the best way to protect yourself is to obtain a filter service based around DNS. Many DNS filters are too sophisticated, complex in installation and costly to run. There are however perfect ones for family or company use, in Public Administrations or Scholastic Institutions, the FlashStart DNS filter is the right choice for those who want a monitored service in their navigation that is very easy to set up, personalise and is always up to date.
The FlashStart DNS filter carefully analyses all of the stops along the way of a journey that starts with the request of accessing a site. The filter uses algorithms as well as machine learning for excluding from the offset dangerous routes, thus speeding up the control. Also, FlashStart uses up to date and trustworthy DNS registers for analysing the user routes towards requested sites.
Capable of filtering roughly 2 billion web site queries, FlashStart DNS protects every day the navigation of 25 million user’s, it is present in over 140 countries throughout the world and in roughly 10 thousand companies, schools and Public Administrations and is supplied, also, as a service, by 700 certified partners
In conclusion, let’s go over again the seven distinctive points of FlashStart DNS:
» Frequent updates of the blacklists: FlashStart verifies 200 thousand new sites every day.
»Low latency guaranteed (the time spent between the access request and the access itself)
» 200 categories of damaging sites and Geoblocking dangerous countries.
» Use of Artificial Intelligence for improving the quality of the blacklists and latency.
» Easy set up procedures and personalisation.
» Native integration with Active Directory from Microsoft for speeding up administration work of Schools, Institutes and PMI systems.
» Worldwide LAN protection and end point roaming on the Anycast network.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







