What is an Advanced Persistent Threat (ATP) and how to prevent it
APT (advanced persistent threat) attacks are the most sophisticated and hence the most worrisome ones. They are targeted attacks, where the threat actor chooses the target and tries to hit him with complex and diversified attack techniques. Prevention of advanced persistent threats requires the knowledge of the TTPs (techniques, tactics and procedures) that the attacker will use to try and hit us.
1. Opportunistic attacks and targeted attacks
Cyber attacks can be basically divided in two macro categories:
» Opportunistic attacks: they are those where the attacker does not aim for a specific target, but proceeds with “trawl fishing” techniques. He launches attacks that are relatively simple but massive, knowing that some “fish” will end up in the net. Phishing is typically part of this category, realized especially through emails that are sent out automatically. Today, hackers use more and more often messages sent via smartphones, and in this case we talk about smishing (SMS phishing). They are unsophisticated attacks, which a user who pays even little attention and has a low cyberthreat awareness should be able to recognize.
» Targeted attacks: these are the most worrisome attacks, since they are properly perpetrated and realized by more expert cyber criminals. They require – as we will see – a preparation and especially a preliminary study of the target, but these efforts are paid off by the value of the target that they manage to hack. Among the targeted attack types we can list spear phishing, DDoS (Distributed Denial of Service), ransomware (that is actually used also in non-targeted attacks) and especially APTs, which are the focus of this article.
2. What are Advanced Persistent Threats (APT)
APTs (Advanced Persistent Threats) are sophisticated but also extremely targeted attacks, which start with the infiltration of cybercriminals within the network of the targeted company.
They are among the threats that today preoccupy companies the most, especially those dealing with confidential data or industrial secrets.
The APT definition stems from the fact that the attack is:
» Advanced: it uses advanced hacking techniques, with several attack vectors. They are not automatic attacks: APT actors conduct a continuous monitoring with a direct interaction to reach pre-set objectives. They combine human actions, tools and techniques in order to carry out the attacks.
» Persistent: an APT is an attack that continues over time, can last even months, with the attacker trying to remain invisible in the system as long as possible. An APT attack is hardly ever carried out by just one person, but rather by a well organized structure, with targets, skills and economic resources. Attackers adopt a slow approach in order to avoid being detected.
» Threat: an APT is a serious threat, because the attackers have precise targets, try to steal data and to spy for a long time.
Therefore, APT is not an attack where cyber criminals “shoot at random” with spam and phishing; on the contrary, targeted and diversified hacking techniques are used.
In particular, the level of sophistication that characterizes APT attacks makes them difficult to detect: several months can go by between the moment of the initial attack and its discovery and neutralization.
This characteristic of persistence is probably the most dangerous factor in these attacks: just think about what it can mean for a company to have the enemy inside its systems without knowing it. In this time span, the attacker will be able to carry out actions that are very dangerous for the victim: exfilter data, delete them or even manipulate them. Think about what could happen if the attacker, from within the system (with sideway moves, as we will see) was able to achieve the control of industrial plants in order to alter the production parameters. It is a possibility that should not be underestimated today with the evolution of Industry 4.0.
>> FlashStart protects you from a wide range of threats and blocks access to malicious websites ? Request a quotation or try it now
3. Persistence: the dwell time
The time used to discover the attack suffered is usually defined as “dwell time”. In this time span the APT attack remains undetected, leaving the attacker with wide room for maneuver and damage.
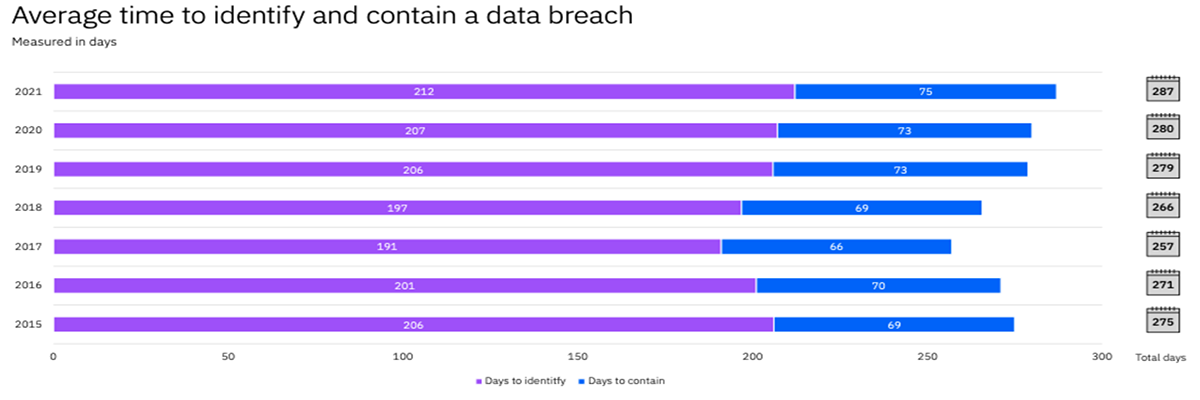
The most serious problem is that this dwell time usually lasts over 200 days, as reported by the picture below (source: IBM Cost of data breach report).
But this is not all: once the attack is discovered, an average of additional 75 days are normally needed for remediation, meaning to remedy the damages from the attack suffered.
These few but significant data must make us aware of how dangerous these kinds of attacks are. This is why also the defense must be targeted and operate in each of the attack phases.
>> FlashStart is the ideal cyber protection solution to satisfy all your needs ? Request a quotation or try it now
4. “Think like the attacker”
Those who attack enjoy the first mover advantage since they play first. Knowing the TTPs (techniques, tactics and procedures) that will be used during the attack is vital in order to be able to prevent it and – if prevention is not enough – to be able to mitigate it once it develops.
This means, in practice, trying to understand what the weak points in our system are and what are the ones that the attacker could exploit with the numerous tactics he can choose from. To sum it up: we must put ourselves in the attackers’ shoes and think like them.
We will see that an APT develops in several, subsequent and linked phases, and in each of them we should do some “threat intelligence”, hence try to detect the threats.
A useful source of threat intelligence is the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) project by MITRE, a non-profit research group that works with the United States government. ATT&CK is a knowledge database and a framework built from the study of
millions of cyberattacks in the real world.
Keeping in mind also these techniques and threats, FlashStart has created an advanced system that protects also from APT attacks, blocking, for example, the threats coming from websites and individual IP addresses that are deemed malicious and could be used as a “launch base” for the attacks.
5. The phases of an APT attack
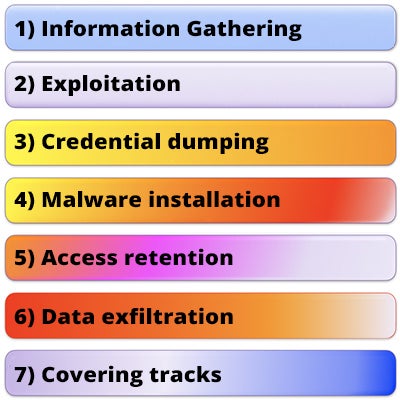
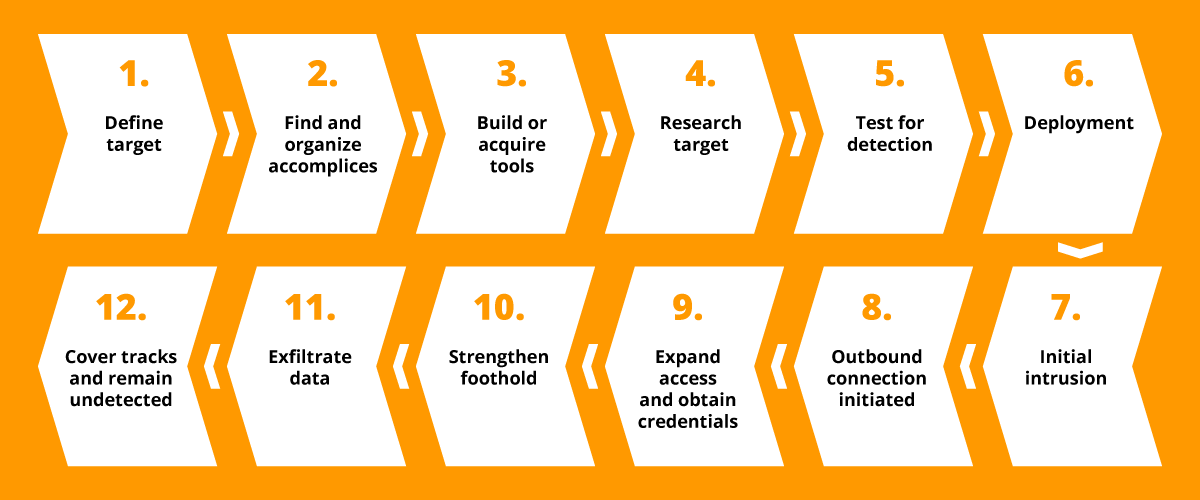
As we said, the APT is a sophisticated attack, which generally consists of seven subsequent phases.
By comparing the phases that we will describe with the MITRE ATT&CK, we can find the attack techniques used in each phase of the attack:
1. Information Gathering: information is collected about the target, its IT systems (to identify any vulnerabilities to exploit), but also on the people working in the company, who very often represent the weakest point on whom to focus the attack (Exploitation, see point 2). This is the stage in which the attacker will invest the most time and resources, because it is exactly this phase that will make a difference in the attack’s success or failure. In order to collect information about the target, OSINT (Open Source INTelligence) techniques are used, meaning investigations on open sources. These sources are especially the web and, more so, social media where people insert a lot, maybe too much information, with little knowledge about the risks that this behavior can generate.
OSINT is widely used and is not illegal, since it is the collection of public information available online. It’s a sophisticated discipline that can make use of dedicated tools available online (several are also open source) that execute in an automatic way targeted searches; to know what these tools are (a wide variety of them is available!) we suggest this useful website.
2. Exploitation: once the Information Gathering phase is over, the attacker is ready to launch the target in order to infiltrate the target. Usually, the human factor is exploited, because it is always the weakest point. The usual social engineering techniques are used: phishing, vishing, baiting, spear phishing, watering hole (compromised websites). Exploit kits can also be used in order to exploit vulnerabilities in the system, techniques of SQL injection or XSS. Sometimes, “brute force” attacks are used in olter to infiltrate the system and violate RDP or VPN access credentials (that all too often are protected with very weak and predictable passwords1);
3. Credential dumping: once the attacker gains access to the attacked system, he will try to penetrate the system more deeply. The so-called Privilege Escalation takes place: with sideway movements (east/west) the attacker tries to obtain more important administrative credentials. In order to do this, specific tools are used like: Mimikatz, RottenPotatoNG and many others, easy to find in the infinite web world;
4. Malware installation: by now the attacker is inside and he will connect to his C&C (Command&Control) servers to download the malware in order to take control of the system and finalize the attack. These softwares are called RAT (Remote Administration Tool) and they are indeed used to control the target system. Let’s remember that these attacks are not carried out automatically, but – on the contrary – they need the remote interaction of the attacker;
5. Access retention: creation of a backdoor, meaning a technical solution that makes it possible to keep open the access to the system, trespassing the normal protection controls. The RAT that has been installed in the targeted system is hence used to install a backdoor, that allows the attacker to access the system again, anytime he wants it. Backdoors can be written from scratch, or else they use softwares that already exists like Meterpreter, a component of the well-known exploit system Metasploit, among the most complete and used in the market;
6. Data exfiltration: data theft, the real target of the attack! The attacker tries to identify and collect CVD (Critical Value Data), using also automated research scripts. Once he identifies them, he needs to get them out in the most silent possible way, in order not to be caught by the victim’s detection systems. Different and sometimes creative techniques are used, such as: compression (rar, zip,…) and sending data outside through transmission protocols like WebDAV, FTP, DNS, tunnelling, etc. Open-source softwares can also be used, like Rclone and others;
7. Covering tracks: the attacker tries to remain inside the exfiltered system for as long as possible (also for months, as we saw above), without being detected by the defense systems. Therefore, he will use manipulation and/or log deleting techniques, and the cancellation of data and softwares used for the attack.
6. Who are the threat actors
As explained above, APTs are sophisticated attacks that can be carried out by cybercriminals with the aim of stealing confidential information and data.
But they are typically a weapon used also by the so-called state-sponsored hacker groups, hence linked – more or less directly – to states and governments. We discussed them in this article.
In this case, the aims can be to hit organizations and infrastructures of an enemy state.
>> FlashStart has grown over the years thanks to its competence and trustworthiness ? Request a quotation or try it now
7. The prevention of advanced persistent threats
Since APT attacks count various phases, also the defense measures will have to intervene in a granular way in each of them:
1. Information Gathering: avoid exposing sensitive information online, especially on social media. Monitor the dark web (there are dedicated tools to do it) with the aim of understanding if there is information (like passwords) related to our organization and that somebody could use;
2. Exploitation: since the first weak element to be attacked is the human factor, it is important to train the users. Implement advanced anti-spam programs in order to make emails secure and block spam and phishing attacks towards the employees. Always adopt system patching policies: update the network softwares and operating systems to eliminate vulnerabilities that the attacker will try to exploit;
3. Credential dumping: a careful access control is needed in order to prevent insiders with bad intentions and compromised users from taking advantage of their credentials to give access to the criminals;
4. Malware installation: the connection to C&C servers is an action that can be intercepted and blocked by the systems supplied by FlashStart, which is able to carry out the filtering of Internet DNSs, through the continuously updated Blacklists. In the same way, whitelisting policies can be used, for the applications and domains that the users can use/install in the company networks in order to reduce the success rate of APTs;
5. Access retention, creation of a backdoor: also in this case, the FlashStart filtering systems can block these actions;
6. Data exfiltration: encrypt data both during sleep mode and during active use. Encrypting remote connection prevents intruders from intercepting data that are transiting;
7. Covering tracks: every attack makes noise. Hence, the movements of the attacker within the system can be detected through a Deep Log Analysis, in order to analyze logs thoroughly and highlight any correlations among different sources. This can be realized also with detection systems like EDR (Endpoint Detection&Response) or also XDR (Extended Detection&Response) and SIEM (Security Information and Event Management)
8. The author
Giorgio Sbaraglia, engineer, is a consultant and trainer on the topics of cyber security and privacy.
He holds training courses on these topics for numerous important Italian companies, including ABIFormazione and the 24Ore Business School .
He is the scientific coordinator of the Master “Cybersecurity and Data Protection” of the 24Ore Business school.
He is a member of the Scientific Committee CLUSIT (Italian Association for Cyber Security) and an Innovation Manager certified by RINA.
He has DPO (Data Protection Officer) positions in companies and Professional Associations.
He is the author of the following books:
» “GDPR kit di sopravvivenza” – “GDPR survival kit” (Edited by goWare),
» “Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” – “Cybersecurity survival kit. The web is a dangerous place. We must defend ourselves!” (Edited by goWare),
» “iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” – “iPhone. How to use it to its full potential. Let’s discover together all the functions and best apps” (Edited by goWare).
He collaborates with CYBERSECURITY360 a specialized online magazine of the group Digital360 focusing on Cybersecurity.
He also writes for ICT Security Magazine, for Agenda Digitale and for the magazine CLASS.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.