
Prevent a Zero Day Attack to protect yourself from a Zero Day Vulnerability
The 0-day or Zero Day protection is a rather hot subject for the providers of computer services, this is because it regards the vulnerability from something just uncovered for which there are still no software remedies available to treat it. There does however exist the possibility of preventing them, lets understand in more detail what we are talking about.
1. What exactly is a Zero Day Vulnerability?
It is called Zero Day Vulnerability (also written 0-day), a fragility that has just been spotted inside a computer system, one that can be exploited by third parties allowing them to execute different actions from those that the system has been projected for. It is called Zero Day Vulnerability to indicate to the programmers that they have had zero days of time to fix the security breach of the system. The fragility could be a coding error or even a simple unforeseen possibility of making abnormal uses with undesired consequences.
Such a system bug will keep the name Zero Day Vulnerability until the programmers have produced a necessary patch to sanitise the problem, resolving in a permanent way for the successive versions of the software.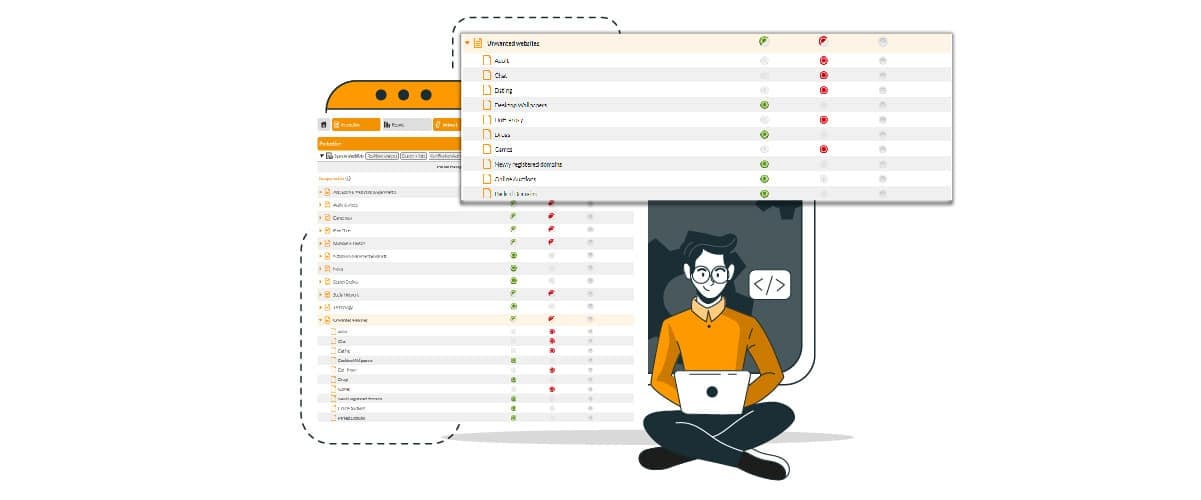
2. What dangers come from a Zero Day Attack?
A Zero Day Attack (or 0-day Attack) is the attempt to make profits or create problems by using the Zero Day Vulnerability, before the programmers realise a remedy to stop the violation or malfunction of the computer system that has been hit.
A cyber-criminal who intends to exploit a Zero Day Vulnerability has the advantage of time that cannot be filled. There in fact exists a first phase in which the hacker creates an attack code (Zero Day Exploit) without the producers even realising that there is a breach in their system software. There is also a timeframe necessary for learning that the system is under attack, working on an unknown vulnerability. Finally, the producers need their own timeframe so they can program a remedy, one that will contrast the malware and manage to sanitise the breach that has just been discovered.
All of this has enormous cost in economic terms for the company, as well as for all the internal users that are under attack.
Apart from everything the software producers don’t tend to divulge that their systems have a defect, in fact they tend to hide the Zero Day Vulnerability and realise the needed patch without spreading any alarms of eventual dangers.
A first step therefore for security against a Zero Day Attack is that of maintaining the systems in continual automatic updates, this way the patch that has been created by the programmers can remedy program breaches as soon as possible, it does however remain palliative, not a prevention, because before the release of new versions without the bug the cyber-criminals could have already created huge damages.
>> FlashStart protects you from a wide array of threats and blocks access to malicious sites ? Request a quotation or try it now
3. How do we confront a Zero Day Exploit?
The only possibility of stemming a Zero Day Attack, as it is unknown as a vulnerability and remedy, is that of preventing the moment in which the attacker spreads the Zero Day Exploit. Usually, such action takes place through phishing systems. The malevolent code, being new, is very difficult to intercept so the attacker will probably be more worried about avoiding any eventual access blocks to malevolent pages. To combat this they will most probably create a new domain that will not be blocked by security systems that are based around existing blacklists. There exists a concrete possibility of stopping the malevolent code being able to hit a Zero Day Vulnerability but to use this you need to have the right kind of protection whilst navigating, this will minimise the risks of malware and in particular Zero Day Exploits. Let’s take a closer look.
4. The advanced systems for recognising the threat
The global DNS platforms with Artificial Intelligence and a form of anti-malware prevention that are ever more efficient. The common objective of such protective systems is that of cloud filtering internet access, using a preventive investigation of domains determining which ones are dangerous on a computer threat level or even ones with undesirable content. The navigation blockage works at a DNS resolution level, the user finds themselves completely unable to visit domain pages that are on a blacklist, at the same time being safe from unwanted malware downloads or annoying content.
To know the various dangers of the DNS in a preventive way, modern platforms make a continuous scan and categorize the web through Artificial Intelligence.
In the case of an advanced system like that of FlashStart, the Machine Learning doesn’t limit itself to just a simple scan of the domains contents but looks at the behaviour of similar sites on the governing blacklist and reaches a predictive capacity of over 90%. The other 10% regards pages that are incomprehensible through language or content, or even newly registered domains that have still not had any activity that can be picked up and noted. If a page is incomprehensible, it cannot however invite to actions, therefore it is almost always not damaging, whilst it is ever more probable that new domains are those with the risk of malware or even Zero Day Exploits.
5. The newly registered domains and the FlashStart prevention
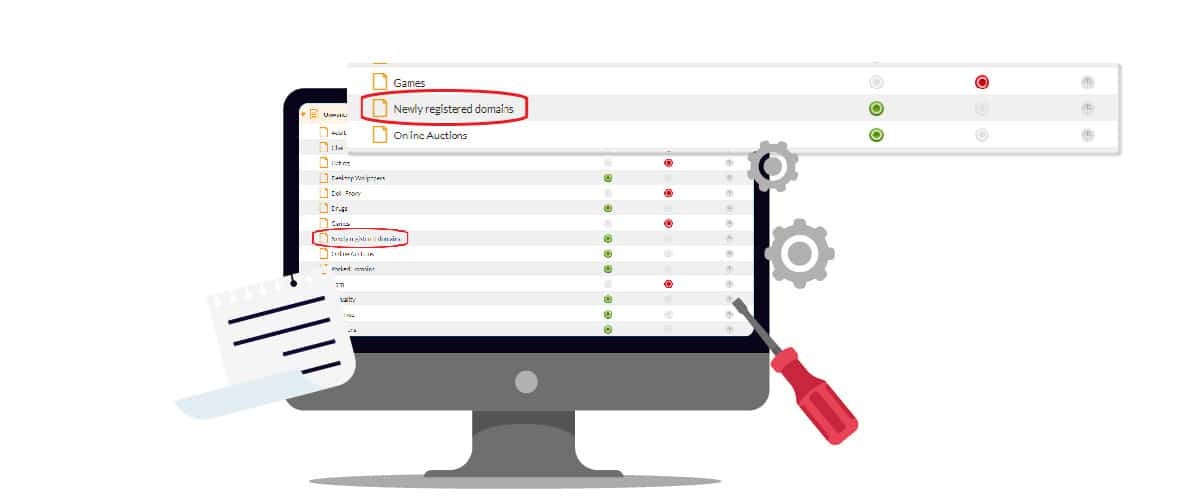
To cancel completely the risk coming from new DNS sites with their activity still unclassified, FlashStart has implemented a preventative blocking function of newly registered domains until they have been scanned and categorized appropriately. In this way the prevention of new malware and in particular Zero Day Exploits is at maximum levels.
The activation of this filter can be done by simply turning it on in the cloud through your dashboard by ticking the relative category that is automatically updated thanks to our Artificial Intelligence.
The category includes all of the new domains up to 30 days of the registration, after which they automatically re-enter in one of the 85 available as blacklists of filter systems of malware and content.
In reality the Artificial Intelligence of FlashStart instantly begins to investigate the activity of the domain but the 30 days are needed for major accuracy. In fact a cyber-criminal could intentionally delay their bad activities on the new domain and wait for it to be categorized as a secure platform as far as DNS Security is concerned. A month’s time is the default amount for an accurate analysis in computer terms and a brilliant compromise, even if it is a very long time in the case of Zero Day Vulnerability.
In fact, often hackers who uncover a new bug don’t exploit it personally but sell it to third parties as Zero Day Exploits, then it is from here that the cyber-criminals intend to make a quick profit, before the programmers spot the Zero Day Attack and update their software versions.
Blocking new domains for 30 days can be a very efficient solution for companies or organizations of every dimension, it is therefore right to evidence the FlashStart solution of which the in-cloud protection has always demonstrated as being excellent under various points of view.
World class performances in velocity and stability, configuration ease and differential filter set up, extremely convenient in price with unique functions such as the protection that is geographically based, easily installed anywhere with just a few clicks, even without the need for any technical or commercial assistance that is however constantly available, thanks to experts and multi-lingual chats.
>> FlashStart protects you from a wide array of threats and blocks access to malicious sites ? Request a quotation or try it now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







