
How to filter HTTP traffic with Wireshark compared to FlashStart
1. Presentation of Wireshark: limits and potential
Wireshark is an open-source instrument that is utilised for analysing network traffic. With this instrument the network administrators can collect information and study the network traffic in real time. Wireshark is an application that can be downloaded free of charge.
It is used for analysing the traffic that runs through our networks. There are of course many router models that already allow you to do such. Wireshark goes a bit deeper though, it allows us to use filters that are very more detailed on our network and the protocols involved. Apart from capturing and filtering the network traffic, Wireshark also offers various analysing instruments in their packets. This enables us to uncover important information, such as the original address, addresses and destinations and ports. It can also graphically represent a frame of level 2 or an IP packet and individualise the data with precision. To have the possibility of inspecting the packets will allow you to uncover network problems as well as security vulnerabilities.
To get the most out of Wireshark it is important to understand the functions and characteristics that are offered by this instrument and how to use them for analysing network traffic. With a solid knowledge of Wireshark and its capabilities it is possible to resolve problems as well as anticipate potential network attacks.
2. How to filter HTTP traffic with Wireshark
One of the most useful functions of Wireshark is the capability of filtering the network traffic for concentrating on specific relevant packets for analysing. We can use the following options for filtering HTTP traffic with Wireshark:
» IP Address: Wireshark allows you to filter your network traffic based around the IP address from origin and destination. This will be helpful for detecting the direction of traffic, for filtering by HTTP, we can use the destination address for filtering some HTTP servers.
» Port: Wireshark allows you to filter the network traffic based around the origin and destination ports. If we are talking about HTTP filtering, the destination port to select would be 80.
» Protocol: Wireshark lets you filter network traffic based around the protocol, such as TCP, UDP or ICMP. HTTP functions above the TCP protocol.
» Text strings: we may also filter based around the contents of an HTTP package; it is a good option to use for filtering HTTP traffic. We can find important information about the HTTP traffic, remember that this type of traffic is not encrypted like HTTPS.
Learning to use the internal filters of Wireshark will be an advantage for any administrator, this is because we can see, with much precision, our network data and the type of traffic that is being consumed.
>> FlashStart protects you from a wide range of threats and blocks access to malicious sites ? Request a quotation or try it now
3. How to use the Wireshark filters for just capturing HTTP traffic.
The Wireshark filters can be used for analysing and acquiring specific packets based around a series of criteria. To only receive pertinent HTTP traffic, it is possible to apply some filters. Wireshark also lets you save these filters. Here are some passages for applying filters for HTTP traffic:
» Select the network card: before starting to receive traffic you must select the interface, it can be a wireless or ethernet interface, this can be verified by your computer.
» Start receiving traffic: once you have selected the network card, double click on it to start the reception.
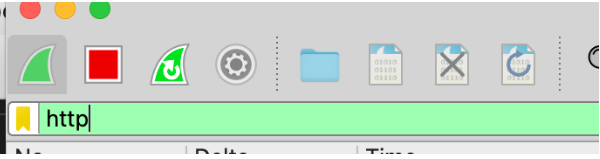
» Create a filter: to acquire just the HTTP traffic, let’s create a filter for the HTTP protocol. We can do this by writing “http” in the Wireshark filters bar and then press send.
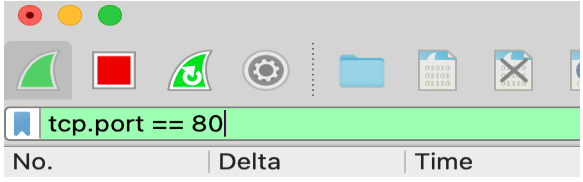
» Apply a port filter: we may also apply a TCP protocol on its port. We can do this by writing “tcp.port==80” in the Wireshark filters bar then press send. This will then only capture the HTTP traffic on port 80.
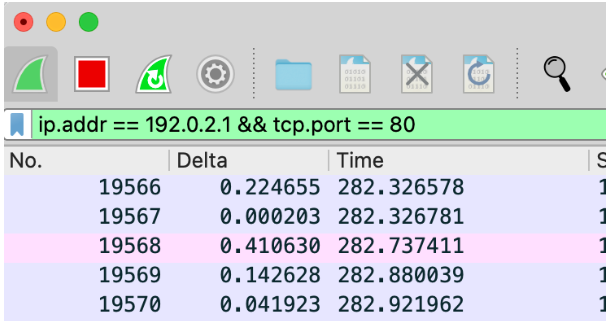
» Combine the data in the filter: not only are we capable of acquiring the HTTP traffic for the port, but we can also combine them adding an IP address. To do this, we must write “ip.addr==[address IP]” in the Wireshark filters bar along with the “&&” command for nesting the data.
» Perfect even more the filters: to perfect these even more it is possible to use added criteria such as the length of the packet or specific information about the packet. In the picture below we are filtering by ip packet dimension of 150 bytes.
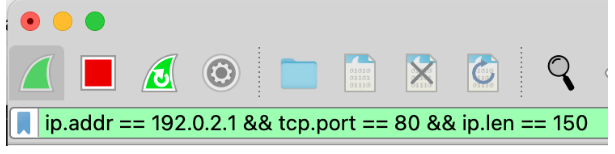
Wireshark allows us to save the HTTP filters. For example, we can save the filters for different addresses and assign a name which is much easier to remember. With this option we don’t need to use the filters bar every time that we want to see a particular type of HTTP traffic. To do this we have to click on “+” in the search bar and add a name to our HTTP traffic filter.

4. Is it important to filter HTTP traffic on a network?
At the moment, the HTTP traffic is not being used as much as it was in years gone by, now it is quite common to see HTTPS type traffic on our network. The HTTP traffic is used for accessing websites that still don’t have HTTPS support. To exchange information, for online transactions or sensitive traffic, we use HTTPS. Saying that, an excessive quantity of HTTP traffic on our network could be a symptom of some kind of attack, either coming from inside or outside of our network. For this reason it is very important to filter HTTP traffic on a network.
One of the principal reasons for filtering HTTP traffic is to improve your network security. Filtering HTTP traffic, it is possible to uncover and block intrusion attempts and mitigate the risks that are associated.
Another motive for filtering HTTP traffic is to improve the network performance. With too much HTTP traffic, the network could become congested and reduce the overall performance. Filtering HTTP traffic it is possible to reduce the quantity of data that is flowing through the network, this will improve the network speed as well as the broadband efficiency.
The HTTP traffic packets can contain useful information such as the IP address and used port for sending and receiving data. Filtering the HTTP traffic this data can be examined closely for identifying the models and resolve network problems.
If there are HTTP traffic regulations Wireshark can help us to detect the destinations and origins of this type of traffic, we are then able to block them with our firewall.
In brief, filtering HTTP traffic on a network is an important activity that can improve security, performance and efficiency for the network. An administrator cannot have the task of just detecting HTTP traffic, they should also be capable of identifying other types. Using the Wireshark filters the activity of identification becomes much simpler.
5. FlashStart plus Wireshark for filtering HTTP traffic
FlashStart is a solution that integrates in a very simple way into our network. Wireshark allows us to detect HTTP type traffic through its filters.
Blocking, if the volume is very high, is a hard task for an administrator. FlashStart doesn’t just help the administrator in blocking. Thanks to its Artificial Intelligence you will be able to detect damaging domains and be able to block them before somebody on your network can access them and receive harmful consequences.
The granular filters of FlashStart are a perfect solution for controlling the network and accesses. They can in fact allow certain contents and block other ones.
We hope that this guide on network HTTP traffic has been useful for understanding the importance of such!
>> FlashStart is totally cloud-based and easily activated ? Request a quotation or try it now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







