
Hiring a hacker: when cyber crime becomes a service
Lea was angry. But this time she wanted to make her boss pay for it. She had always thought about the most bizarre ways of taking revenge on that company, where she felt like a number and kept silent in spite of the continuous unjust treatment she received. But this time it was different: now she would move from theory to practice. And she knew how to do it, she had seen it in movies: everything was available on the Internet and she would definitely find somebody who, for a reasonable price, would spread some rumors about the company, maybe obtain some data and make them public, or why not some chats where directors and colleagues talked widely about everything and everybody?
Yes, this time she would hire a hacker.
Cybercrime-as-a-service: You can now hire a hacker
In the past, cybercriminals used to operate on the dark web, the dark part of the Internet, more difficult to access and navigate by the average user. Today, the average user, which includes people like Lea but also companies, political parties and public administrations, can gain access to cybercrime services directly on Google.
Indeed, in the age of services cyber crime has evolved as well and has adapted to the requests of the market. Therefore, malware attacks, once the prerogative of hackers who carried them out independently and for their own reasons, have become a new market where demand and supply can meet.
The world is now capable of offering cyber crime and ransomware services upon payment of a fee and today cyber criminals work at the service of whomever pays them. Unsatisfied employees, lovers who have been cheated on, companies that want to grow, parties aiming for victory: they all have in common the desire to prevail over the others, over their competitors or over those perceived as enemies.
In this panorama, you could well be the next target!
Protect yourself in a simple and fast way with FlashStart, the cloud-based webfilter that checks all the Internet traffic going through your device and blocks access to dangerous contents.
Start your free trial now!
ENISA: the 2021 report
At the end of October Enisa, the European Union Agency for Cybersecurity, published the 2021 update for its Threat Landscape report, the report on the state of cyber threats in Europe. The report, which is available in its full text here, highlights several evolutions in cybercrime over the last year and, more precisely, in the period going from April 2020 to July 2021.
Ransomware: the main threat
Enisa describes ransomware as a type of malicious attack where the attackers encrypt the data of an organization and ask for the payment of a ransom in order to normalise the situation. According to the collected data, ransomware has been the main threat between 2020 and 2021 and there are many examples of ransomware carried out also at a high level, which were widely covered by the media.
In terms of trend, Enisa underlines how, in the period of analysis, supply chain attacks bloomed. These are attacks that have as their target the entire supply chain for a specific service. They often have as their primary target Managed Service Providers (MSPs), who manage services for companies and, exactly because they follow and collaborate with several companies, represent a good entry point for a widespread attack. The impact of these attacks have become clear, for example, following the attack on Kaseya, which we analysed in depth here.
Cybercrime-as-a-service
The Enisa report describes cyber crime as an “ecosystem” with a global presence. As such, it evolves and adapts and cybercriminals specialize in different services. Enisa underlines that their main target has become monetising, hence making money from the attacks they carry out.
In this panorama, cybercrime-as-a-service and the idea of offering pay-for cyber criminal practices has become more and more relevant. There is a double effect:
» On the supply side, the level of cyber skills required to carry out an attack decreases: also “beginner” hackers can find connections on the dark web and, upon payment of a fee, can access for example prepackaged ransomware attacks that they can enable with a few steps.
» On the demand side, it becomes easier for those who want to purchase a hacking service to find an available supplier who can sell the service and carry out an attack on a specific target. So in the end, today it is much easier to hire a hacker. Offers for these services can now be found also navigating online on Google.
As underlined by Enisa, the services offered and that can be purchased range from insurance and credit services, to data encryption, to email and social network spamming, to actual attacks on specific targets.
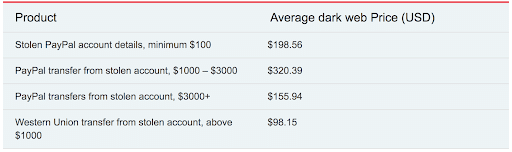
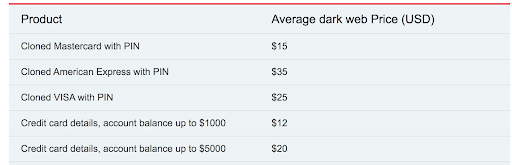
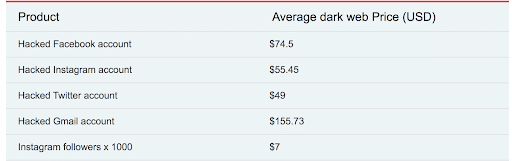
Fonte: https://www.privacyaffairs.com/dark-web-price-index-2020/
The new frontiers
The new frontiers in cybercrime-as-a-service include:
Phishing-as-a-service
Enisa describes phishing-as-a-service as a proper business model where attackers pay an operator (hence a cyber criminal) in order to develop and distribute phishing campaigns from fake log-in pages and fake hosting sites. On top of this, such “operators” also analyse the access credentials that the unlucky users input and redistribute them. In this way, attackers can outsource the skills they are missing.
Disinformation-as-a-service
According to Enisa, services of “pay-for disinformation” have spread especially in connection to the Covid-19 pandemic because of the growing need felt by users at all levels to obtain information about the pandemic itself.
A wide range of actors benefit from these pay-for services: States and political parties, criminal and terrorist groups, companies, and then down to the single users, like the Lea of our initial story.
On the one hand, we are witnessing an increase in the exploitation of disinformation-as-a-service by terrorist and extremist groups who want to create and distribute conspiracy theories. On the other, companies use these services more and more often in order to manipulate the market or attack the reputation of their competitors.
The most widespread methods are those of message “chains”, of the distribution of contents on social media and of phishing through audio files, messages and emails.

FlashStart is the could webfilter that protects you from cyber attacks, both general ones and those prepared for a specific target. Request a quote now and start navigating safely.
Prestigious customers: hacking and disinformation as a service to the State
According to the Enisa report, the main exploiters of disinformation-as-a-service, hence those who are most likely to hire a hacker, are States, political parties and companies that deal in public relations. But States do not only like disinformation. Enisa dedicates a long section to “State-sponsored actors”, groups of cybercriminals sponsored directly by the States.
Espionage among States has existed since the States themselves were still in the formation phase. Cybercrime has taken it to a whole new level. An example of this is the supply chain attack to SolarWinds, whose victims included also the Department of Energy and the National Nuclear Security Administration of the United States.
The analyses of the attack resulted in the US accusing Russian cybercriminals. Following the attack, the US imposed sanctions against Russia and in June of 2021, during a summit in Geneva, Biden gave Putina a list of 16 off-limits infrastructures, meaning infrastructures that cannot be the target of hackers. Biden then stressed again, following yet another attack that took place in July 2021, that in case of attacks on those infrastructures by groups acting from Russian territory he expects the Kremlin to intervene.
Are you also thinking, like Lea, to hire a hacker? Then you shall consider that somebody else may have the same intentions towards you: first of all, think about safety! ? FlashStart allows you to defend yourself from phishing and ransomware attacks you may fall prey to. Start your free trial now and enjoy a safe navigation!
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.
> For more information click here
> For a free trial click here
> To request a quote click here







