
DNS Spoofing, what it is and why it is dangerous
What is DNS Spoofing? Let’s see what it is exactly and why it is dangerous for navigation, at home or even on a company network. It is not a risk that should be undervalued, that is because if you go headfirst into a DNS Spoofing you will become prime prey for some phishing, trojan or malware, all of which can be resolved by choosing a good URL filter system based on the DNS.
1. What is DNS Spoofing
For DNS Spoofing, also called ‘DNS cache poisoning’, we are talking about a particular type of attack that is aimed at modifying the DNS list to re-address the web traffic towards menacing sites. To understand this definition, it is important that we explain first what DNS are and how they are part of the game whilst we are navigating.
DNS (Domain Name System) is often defined as the internet telephone book. More precisely, it is a decentralised hierarchical naming system that is used for identifying computers and services that can be reached online. Generally there are two ways of accessing a website or web page. We can either type the domain name of the site (flashstart.com) directly into the navigation bar in the browser (Google Chrome) or else we can activate the automatic opening of the navigation program (browser) with a page link that we might have received previously by email or by chat.
At the moment when, in the navigation bar of the browser, you write flashstart.com and press enter the browser transforms (resolve) automatically the domain name into an IP address, this is because the computer recognises the IP – a succession of three groups of triplets and a couple of numbers – and not a string of letters. In fact, the browser asks the Internet Provider that we use to interrogate the DNS resolution service, of which we will speak about soon, and convert the domain names into a sequence of numbers.
In the case of flashstart.com, the IP address is 151.139.128.11. This means that the navigation program connects to the server that has that address and hosts the flashstart.com site. In particular, the first three parts of the IP, in the case of addresses such as lpv.4, corresponds to a network ID, the last to the host ID, the computer itself.
We should however underline that there is not a one-to-one correspondence between the IP and domain name. For example, with the IP 151.139.128.11 there corresponds 44 thousand sites that are hosted by the same server. So, the DNS is the way in which a domain name is associated to an IP. However, DNS is also the protocol that regulates the function of the service. The system was introduced in 1983 and its specific origins are described in the RFC 882 protocol. The RFC (Request For Comment) is the document in which there is a detailed explanation of how the DNS system should function.
Practically speaking, the DNS system is a universal register, a database distributed by DNS servers (nameservers) that are categorized firstly in domain extensions (.com, .it, .edu). For every domain there is a ‘container’ that archives the domain information and is capable also of tapping into information from other domains that are not archived. Amongst the information (database record), obviously, the most important is the IP address that corresponds to the domain name, the information that the browser receives for accessing the requested site.
The nameservers throughout the world that archive and look after the domain names, categorized according to their domain extensions (technically DNS root zone) are called root nameservers and there are 13 of them in the world. Also, on the journey between the computer and the site that needs to be reached, you meet various nameservers, therefore you just need to modify the intermediate register to change the direction of navigational travel.
In an attack such as DNS Spoofing, the cybercriminals commit an action that is very simple: they modify a DNS list in such a way that they change the IP address correspondence of a site and the domain name. This way, the browser thinks it is connecting to a site that corresponds to a certain address but, in reality, you end up in a menacing site.
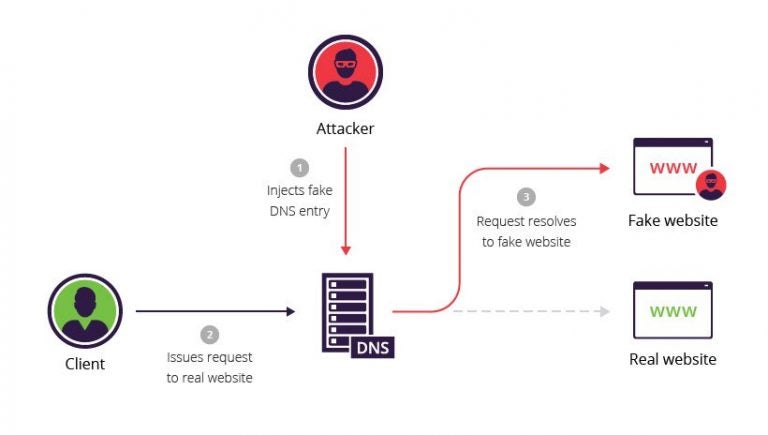
2. DNS Spoofing consequences
Usually, through DNS Spoofing, the user ends up on a site, or a page that effectively appears to be that which was requested but in fact is not. The most common consequence is then phishing. The user, for example, receives an Email message, or an SMS, that requests them to access, as quickly as possible, a certain web page. Once connected to that page you are asked for your credentials, for example your username and password for your home banking or credit card details.
If these are inserted, the cybercriminals enter into possession of your credentials and access your home banking, they may even sell this information on the Dark Web. They are also capable of shopping on a scam website or even offering your credentials for accessing software for company services, putting the entire company in trouble. It is important to underline that, to become a victim of having malware or trojan installed, all you have to do is visualise a certain page, you don’t even have to interact with it (by clicking a link or filling in certain fields).
We should also say that a DNS Spoofing attack is particularly refined and asks for a certain astuteness, therefore the attacker themselves carry them out if the game is worth it. In fact, DNS Spoofing is used for modifying, in a permanent way, the journey towards a certain domain, thus capturing the most victims possible. If the objective is to steal the access credentials of home banking, all that is needed is an SMS that contains a ‘short’ link – such as a bit.ly – in which you can’t clearly read the links journey. More than often this is all that is needed to capture the victims.
In the case of more organized attacks, in the ‘bait’ message they could insert a correct URL which is what is expected, this is then redirected to a different page that has been graphically reconstructed to resemble perfectly the correct one. The re-addressing comes about thanks to the alteration of the DNS listing.
The methods for carrying out attacks such as DNS Spoofing are two: the Man in the Middle (MITM) and the compromising of the DNS server. In the first case you intercept the communication between the user and the DNS server and then re-address towards a menace site. In the second you modify the DNS registers and configure them by altering the association between names and domains so therefore addressing them towards menacing sites.
>> FlashStart protects you from a vast gamma of threats and blocks the access to menacing sites ? Request a quotation or try it now
3. How to defend yourself against DNS Spoofing
It is clear that falling into a DNS Spoofing attack is no joke and can bring about some very dangerous consequences, let’s see how we can defend ourselves. In the case of DNS Spoofing you must first be very vigilant. This is because the alteration of a path is done in a totally transparent way to the user. You can’t know beforehand what is going to happen when asking to access a site, what path you will take and if the route will be safe.
For this reason, it is necessary to trust a navigational filter instrument on a DNS level. If valid, in a moment we will explain what we mean by this, the system will notice that something is not right during the course of the request. Or, in the biggest number of cases, the filter will block the access to fraudulent sites once it has noticed that it is taking a dangerous path. In this case, the user may not have an explanation of why they cannot access a certain site, or even imagine a ‘false negative’ of the filter. However, in 99% of cases you need to have trust: the filter is always right.
>> FlashStart is the leader in competitiveness ? Request a quotation or try it now
4. Why use a DNS filter
A good way to protect your company from DNS Spoofing is by using a DNS filter. What does that mean? The solution, available also in cloud, has been studied for blocking the access to any site that is a risk. Without getting wrapped up in too many technicalities, all you need to know is that a DNS filter is the most precise.
A DNS filter controls the ‘goodness’ of a server, the one that has that particular address, not falling into the trickery that the harmful villains can use for falsifying domain names and content of web pages. The DNS filter controls if an address from that server is included in a blacklist or not, if it is it will immediately block access.
FlashStart offers various DNS filtering solutions that are available for companies, schools and institutions, also for home use. It is a powerful and economic alternative. Also, the value of the FlashStart solution is measured above all for analysing all of the stops along the path of somebody who makes a request to access a site. The quality of service resides in the capability of using algorithms of machine learning for excluding up front dangerous paths. Not only, FlashStart is capable of monitoring and constantly verifying the DNS registers that will be met along the way.
Capable of filtering 2 billion website queries, FlashStart DNS protects the navigation of 25 million users every day, it is present in more than 150 countries throughout the world and in roughly 12 thousand companies, schools and public administrations and is dispensed, under the form of a service, by 700 certified partners.
Let us see the exclusive characteristics of the FlashStart DNS Filter
» Frequent blacklist updates: FlashStart verifies 200 thousand new sites every day
» Guaranteed low latency
» Ample possibilities of personalizing the solutions
» 90 categories of damaging sites as well as Geoblocking for isolating countries that are considered to be dangerous
» Use of Artificial Intelligence for improving the blacklist quality as well as the latency
» Easy to use concerning its configuration and management
» Native integration with Active Directory from Microsoft to speed up the system administration work of schools, institutes and small companies
» Worldwide LAN protection and end point roaming via the Anycast network
>> FlashStart is totally in cloud and easily activatable ? Request a quotation or try it now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







