
How to protect yourself from ransomware
1. The explosion of Ransomware
Over these last years, ransomware attacks have become more numerous, targeting companies all over the world.
It is estimated that during 2021 in the world a ransomware attack took place every 11 seconds! Two years earlier, in 2019, there had been an attack every 14 seconds.
According to CyberEdge (see pic. 1), the percentage of organizations that were victim of ransomware has increased from 55,1% in 2018 to 68,5% in 2021.
In our previous articles we have already highlighted how ransomware attacks have evolved a lot over these last years, compared to the first years from their appearance (around 2013-2017)
Today, there are organized cybercriminal companies, equipped with many resources, who produce malware. Their business model can be compared to that of the best “traditional” corporations and they can carry out R&D to create ever-more sophisticated and aggressive ransomware.
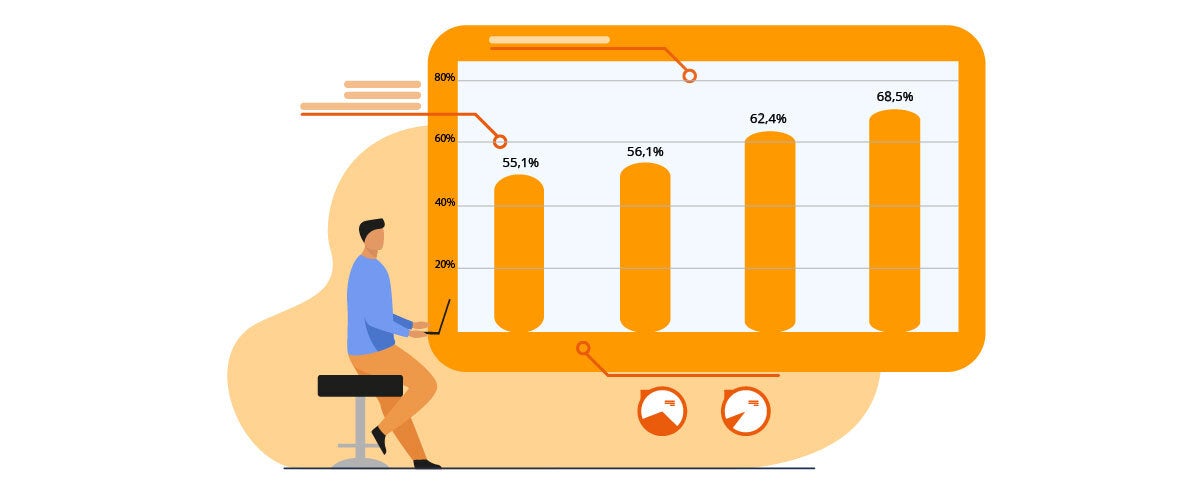
Picture 1 – Growth in ransomware attacks over the last four years
Attack techniques have changed (TTP: tactics, techniques and procedures), ever more sophisticated and similar to those of APT attacks (Advanced Persistent Threat).
We must therefore consider the possibility that ransomware might hit our company. Hence, the doubt is not “if” the attack will take place, but only “when” it will.
For every company, prevention is hence not the only vital thing.
2. How to protect from ransomware: post-attack remediation measures
If on our computer screen a picture like this appears, it means a ransomware has hit us and is now presenting us – like a final verdict – with a ransom request. Therefore, how can you protect yourself from ransomware? What can we do now, without panicking and despairing?
When this message appears (it is usually a picture file or a .txt format), it means the ransomware has already ended the encryption of our files. Data has been seized and now you need to decide what to do. In this unlucky case, you have essentially four options:
» Restore the files from a backup: this is the best solution, and actually the only one that should be considered by a well-organized company.
» Look for a decryptor online in order to decrypt the files.
» Do nothing and lose your data.
» Pay the ransom.
Let’s dig deeper into them.
>> You can activate the FlashStart® Cloud protection on all Routers and Firewalls to grant the safety of your desktop and mobile devices and of your IoT devices on local networks
2.1 Restoring the files from a backup
It’s the best solution and it is available if we have worked carefully and managed a correct recurring data saving. Indeed, in order to be able to restore data, it is necessary to have a backup copy that is:
» Available,
» Recent,
» Functioning,
» Protected (hence, that cannot be attacked by ransom itself).
I wanted to highlight these four prerequisites since we find ourselves way too often in companies that – in full ransomware emergency, with blocked computers – have no certainty about the state of the backup until they start examining it. And then they discover that: it is incomplete (some folders have not been copied), it is nor up-to-date (for some time it hasn’t been done…) and other cases like these, which unluckily have really happened.
But today the biggest risk is that a malware attack might also encrypt the backup.
Indeed, attacks have become much more targeted and sophisticated: cyber criminals are aware that most likely, victims have created a backup that will make their attack ineffective. This is why last generation ransomware, before uncovering their data encryption, analyzes the system whose data has been violated. The aim is exactly to find the backup and encrypt it as well, so as to deprive the victim of the most important countermeasure and understand how to protect from ransomware.
If this point is reached, the attacked company will be defenseless before the ransomware, with no more defense instruments.
How can you protect yourself from ransomware that tries to also encrypt the backup?
Obviously, with the fundamental 3-2-1-Backup rule: 3 copies of everything you want to preserve.
Of these: 2 on-site copies on different storage locations (HD, NAS, Cloud,…) and always one copy in a remote site so that it is off-site and offline (for example on tape units disconnected from the network).
And also, always set up the backup procedure so that the backup copies are not accessible online, except for the software that takes care of the backup itself. No other user shall have access to the backup!
If we own a usable backup, you nevertheless need to first clean the infected engine (or engines), before recovering the data. The recovery can take place through antivirus scanning to ensure that the damaging software has been removed, but this is not a safe enough system, so we do not suggest it.
To be 100% sure that there are no traces left of any type of malware, we suggest a complete formatting of the attacked computers. Only then can you proceed with the data recovery from the backup on a clean installation. Obviously, this requires time and it’s the reason why every ransomware causes downtime within a company.
>> FlashStart protects you from a wide range of threats and prevents access to malicious websites ? Request a quotation or try it now
2.2 Looking for an online “decryptor” to decrypt files
The great proliferation of ransomware varieties over the last years has meant that the major global vendors of security have tried to look for “antidotes” effective against these malware. And in some cases they have succeeded: for some less recent versions of ransomware – or the most rudimental ones – programs and tools (decryptors) have become available online that are able to recover the encrypted files.
However, these are not elementary procedures and they are often complex and rarely succeed with the most modern and best built ransomware. After all, also the hackers read the same security blogs and forums and update their products to make them unattackable by the decryptors.
Let’s mention some popular cases: the first versions of Petya had weak points in their encryption and this allowed victims to recover the decryption key. In subsequent versions, hackers have remedied this flaw. Also the TeslaCrypt ransomware (one of the most widespread in 2016) had vulnerabilities that allowed victims to recover the private key using some dedicated tools (TeslaDecoder, TeslaCrack, etc.). From version 3.0 of TeslaCrypt onwards, this flaw was eliminated and AES256 encryption has made all types of recovery of the decryption key impossible.
So, this option has low chances of success (practically zero if the encryption used some strong algorithms like AES256, Salsa20 or others), but it can nevertheless be worth it to look online.
To this end, let me point here to the extremely useful “No More Ransom!” website.
It was created in 2016 by the National High Tech Crime Unit of the Dutch police (the famous Politie), by the European Cybercrime Centre of Europol and by two cybersecurity companies, Kaspersky Lab and McAfee, with the aim of helping ransomware victims to recover their encrypted data without having to pay the criminals. Today, it counts several other qualified partners.
Through a search on the website, or by uploading two of the encrypted files on the dedicated Crypto Sherif page, we will be able to obtain the decryptor for free (if it exists!) in order to decrypt the file.
It is also possible – and we recommend it – to indicate the URL of the web page or the bitcoin or onion address that appears in the ransom request.
We absolutely do not suggest looking for the decryptor on the web through other channels: you may end up having bad surprises! Online, there are websites that claim they can recover documents that have been encrypted by ransomware, but actually they encrypt them a second time.
And then they ask for a ransom in order to supply the “decrypt tool”. They exploit the need of the people to hit, confirming that there is no ethics in cybercriminal attacks.
A famous case is ZORAB, which promises to supply the solution for the STOP Djvu ransomware, but actually re-encrypts the files and changes their extension to .ZRB.

2.3 Doing nothing and losing your data
It is definitely not a preferred solution and can almost never be the way to go, especially in a company, unless the encrypted data has really low importance. Even if we may opt for this solution, we however advice to:
» take out of the machine the disk with the compromised files and put it aside: somebody in the future may be able to find the decryptor for our files, which might therefore be recovered. Months could go by, but it could happen…
» Or also (for the same reason) create a backup of the encrypted files, keep them somewhere and then recover the machine.
2.4 Pay the ransom…
From an ethical point of view, it is by far the worst solution, one which should never be reached: by paying we feed the crime and make it even richer and stronger. There is a further aspect to consider: if we pay, we will send the criminals the message that we are vulnerable and available to pay, so…we should expect other attacks! We know that who pays once has at least an 80% chance of being attacked a second time.
Does paying give you your data back?
There is no guarantee that you’ll have your data back: always remember that on the other side there are some criminals.
However, for a “brand reputation” policy, it is preferable for these criminals to give us our files back, otherwise their “reputation” would be damaged and the companies would not pay anymore.
This is what happens in most of the cases, but there is at least a 20% chance that, even after paying, your data will not be available any longer. According to the recent Sophos “The State Of Ransomware 2022” report, this percentage increased to 40% over the last year.
The lack of data recovery can happen not only because of dishonesty on the part of the criminals but also for other reasons, such as:
» an error in the payment;
» a lower than requested payment (a mistake that is easy to make: the victim didn’t consider the commission on the transaction while purchasing the Bitcoins);
» the Dark web site for the payment cannot be reached anymore (it has been closed by the police);
» the decryptor does not work: it is what happened to Colonial Pipeline with DarkSide in May 2021.
If, despite all, you decide to pay the ransom, these are usually the steps to take (with some variations depending on the type of ransomware that has hit us):
» Read the instructions that have been sent to us together with the ransom request: you need this to understand how to contact the criminals, what is the amount they are asking for, almost always in Bitcoins, and – especially – how much time we have to pay before our files are definitely deleted (generally cybercriminals set a deadline of around 72 hours, or anyway not a very long one).
» Purchase the bitcoins (or other cryptocurrency) for the payment: identify a website where it is possible to “exchange” this currency. Use only exchange websites whose reputation has been proven. There are a lot of them online and they are absolutely legal, but there are also fraudulent websites and it is important to avoid them attentively.
» Open an account on the chosen website: this means an electronic wallet where the purchased Bitcoins will be deposited.
» Since the contact with the cybercriminal usually takes place via dark web, through the Tor net so as to grant anonymity, you will have to install a Tor browser: you can download it directly from this website.
» Only through the Tor browser (and not via Chrome, Firefox or Safari) can we access the website identified by the hackers: websites in the Tor network are located in the Dark web, they are not indexed on Google, and can be reached only if you know the exact address, which is usually very complex. Here is an example of a Tor address: 7yulv7filqlrycpqrkrl.onion.
» Pay the ransom: this means transfering the money from your own Bitcoin wallet to the hacker’s one. To reach it, it is usually sufficient to follow the instructions provided by the cyber criminal. The wallet to which you have to transfer the money is identified by a “wallet ID”, which consists of a long string of numbers and letters like this one: 19eXu88pqN30ejLxfei4S1alqbr23pP4bd (it’s like a bank IBAN). This code traces the payment using only numbers, thus making it almost impossible to trace back the wallet owner’s name. After transferring the bitcoins on the hacker’s account, we will receive another code (again, a long string of numbers and letters), which represents the transaction confirmation.
» Wait and hope…: within some hours (the time necessary for the transaction to be processed by the systems) we should receive a file with the decryption key, or else an executable file (the decryptor), which will decrypt the files. In order to permit the decrypting of the files, you will have to keep connected all the devices and disks that were connected when the infection happened, otherwise some files might not be decrypted.
Usually, a “decryptor” file is sent, meaning a file that will execute the reverse of the path that the ransomware encrypted. The decryptor includes a decryption key (in some cases it is sent separately). It does not always work well: it’s a program and it could have been set up the wrong way…something that has already happened, like in the Colonial Pipeline case mentioned above!
Be careful: the decryptor does not remove the trojan, it only decrypts the data. Therefore, you must eliminate the malware using other antimalware tools, or even better by completely formatting all the infected machines.
There are some risks that should not be overlooked:
The decryptor could include other trojans (it is not a frequent case, but we cannot be sure that it won’t happen).
For extortions carried out following “manual” attacks (meaning not opportunistic ones) there is the additional risk that the amount will increase, hence that the cybercriminals will raise their requests: it can happen if they realize they have hit important targets like big corporations or hospitals. It happened, for example, to the Kansas Heart Hospital in Wichita (Kansas): after receiving the ransom, hackers provided only partial access to the encrypted data and asked for an additional payment in order to decrypt the remaining data. The hospital refused to pay a second ransom (May 2016).

3. Ransomware and GDPR
In the moments that follow a ransomware attack, it is easy to lose your clarity of mind.
However, we must not forget that such an attack has most likely resulted in a data breach (a loss of and/or compromising of the data) and you need to understand how to protect yourself from ransomware. If the compromised data include personal data (which is highly probable), the company must notify the supervisory authority of the data breach that hit it.
This is what article 33 of the GDPR requires, which also obliges companies to notify of the attack “without undue delay and, where feasible, not later than 72 hours after having become aware of it […] unless the personal data breach is unlikely to result in a risk to the rights and freedoms of natural persons”.
This is an obligation of law that we shall not forget, in order to avoid the sanctions envisaged by the GDPR.
>> FlashStart is totally cloud-based and easy to activate? Request a quotation or try it now
4. How to protect yourself from ransomware with the FlashStart solution
The FlashStart DNS filter is fast, trustworthy and always updated. It protects from all Malware, Botnet, Ransomware and Phishing attacks.
Defining a strategic plan to understand how to protect yourself from ransomware is fundamental.
By applying Artificial Intelligence to Cyber Security, you will first of all adopt an automatic system to update the blacklists used by the DNS filtering. With over 1.7 billion active websites and more than 200 thousand new domains added on average every day, a categorization that uses advanced systems is fundamental in order to grant a high protection level.
With over 190 million websites that have already been reviewed, to which every day we add the new analyses that follow users’ visits all over the world, FlashStart offers an innovative and effective intelligence on cyber threats (malware, ransomware, botnet, phishing, etc.) and helps you understand how to protect yourself from ransomware, allowing you to easily customize the contents that the final users can access, based on the needs of companies, educational institutions and households.
By introducing the concept of DNS Intelligence, the artificial intelligence algorithm permits a speed-up of the data collection about DNS, domains and contents, “learning” from the website analyses and foreseeing which others are at risk of being blocked. In this way, the filter quality is improved and so-called false negatives are avoided, hence websites that are considered dangerous by mistake.
To define well the right strategy to understand how to protect yourself from ransomware, the choice of the type of DNS filtering is important and you must consider three aspects: distribution, latency, and the continuous update of the control tables.
For example, FlashStart is distributed globally through an Anycast network of datacenters located in various continents that permit instantaneous connections.
Web threats are added in real time to the lists available in the cloud and the clients are granted a protection service that is constantly updated. Last but not least, FlashStart grants 24/7 assistance in English, Italian and Spanish.
5. The author
Giorgio Sbaraglia, engineer, is a consultant and trainer on the topics of cyber security and privacy.
He holds training courses on these topics for numerous important Italian companies, including ABIFormazione and the 24Ore Business School.
He is the scientific coordinator of the Master “Cybersecurity and Data Protection” of the 24Ore Business School.
He is a member of the Scientific Committee CLUSIT (Italian Association for Cyber Security) and an Innovation Manager certified by RINA
He has DPO (Data Protection Officer) positions in companies and Professional Associations.
He is the author of the following books:
» “GDPR kit di sopravvivenza” – “GDPR survival kit” (Edited by goWare),
» “Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” – “Cybersecurity survival kit. The web is a dangerous place. We must defend ourselves!” (Edited by goWare),
» “iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” – “iPhone. How to use it to its full potential. Let’s discover together all the functions and best apps” (Edited by goWare).
He collaborates with CYBERSECURITY360 a specialized online magazine of the group Digital360 focusing on Cybersecurity.
He also writes for ICT Security Magazine, for Agenda Digitale and for the magazine CLASS.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







