How to Add FlashStart DNS Filter to Mikrotik
1. Security data
Cyber criminals exploit data stored in digital systems and other devices in order to gain access to sensitive information. Recent reports of serious breaches of corporate networks have highlighted the need for improved cyber security measures in order to protect users against harmful activities.
With more and more people working remotely due to the pandemic, cyber criminals have even more opportunities to exploit weaknesses in corporate systems and networks. Hackers can steal sensitive data, including financial and personal information, or introduce malware into a system, which could cause further damage. It has become increasingly important for companies to invest in appropriate security measures, such as firewalls, antivirus software, and detection and prevention systems.
MikroTik is equipped with a powerful firewall and, in combination with FlashStart, can protect the network infrastructure in order to prevent and respond to potential threats on the internet. The purpose of this guide is to show how we can design a UTM Firewall with FlashStart and Mikrotik.
2. Types of attacks on the internet and data networks
2.1 Passive attacks
Passive attacks in cyber security have been a growing concern for data security professionals. Using techniques such as traffic detection and analysis, hackers can gain access to data without actively attacking the system. These passive attacks are difficult to detect and, if undetected, can cause serious damage to the system.
Unlike active attacks, which involve direct interaction with the target system, passive attacks allow hackers to gather information without the knowledge of the end user or network administrator. Such attacks involve the interception of network communications or the scanning of open ports and services on a network. Attackers can use this collected information in order to gain access to sensitive information stored on a server or in databases. This type of attack is particularly dangerous because it can go undetected for long periods of time before IT or data security personnel detect signs of the intrusion.
2.2 Active attacks
An active attack is a type of cyber attack that searches for vulnerabilities or exploits existing weaknesses within an organization’s system or network. Examples of active attacks can range from denial of service (DoS) attacks, which flood a system with requests until it fails, to data breaches in which sensitive information can be compromised. Active attacks often involve malware or malicious code that is injected into the target’s systems, allowing attackers to gain control. By exploiting these weaknesses, attackers can gain access to sensitive data or disrupt large-scale operations.
3. MikroTik e FlashStart
FlashStart can help prevent these attacks through its granular control of and artificial intelligence for dangerous sites. We could design a firewall with thousands of effective rules, but if a user on our network connects through a phishing or spoofing technique and opens a harmful link, this can be an attack vector for a cyber criminal and can expose our network.
MikroTik has a powerful firewall that can help us detect these attacks and respond to a possible security breach in our network. The combination of both technologies allows us to design a UTM firewall at a very low cost by configuring FlashStart in MikroTik.
The design of a UTM Firewall thanks to FlashStart and Mikrotik technology guarantees that security is not left to chance.
4. Configuring FlashStart in Mikrotik
Integrating FlashStart with MikroTik is simple. You can follow our step-by-step guide.
4.1 Granular filters
FlashStart is distinguished not only by its protection through artificial intelligence, but also by the ability to add filters in a granular manner. This means that it is possible to filter out malicious contents, but not other contents.
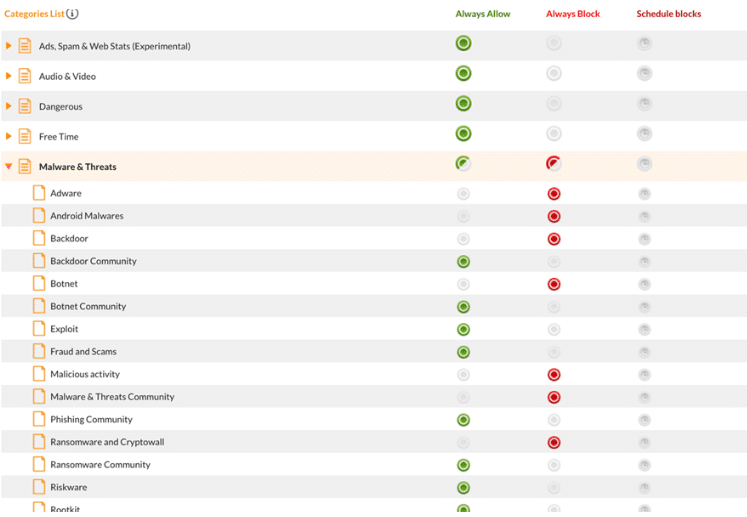
When FlashStart detects blocked contents, it will not be possible to access the resource; this action prevents attacks from harmful sites such as phishing, malware, and viruses.
5. Protect our network with MikroTik
We already have DNS protection through FlashStart, now we will use the powerful Mikrotik Firewall to add an additional layer of security to detect and respond to attacks. With technology from both brands, we can design a UTM firewall.
5.1 Network protection from scanners
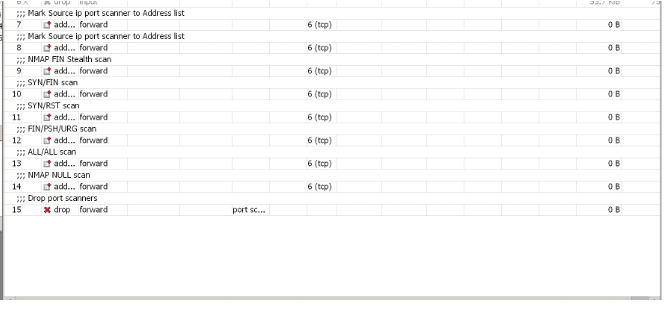
The port scanning technique is used by a potential attacker in order to determine what services and ports are open on our network. MikroTik will help us to detect this type of attack. We will apply the following rules through the CLI. If we use Winbox, we must go to the “New Terminal” section and copy and paste the following rules:
/ip firewall filter add chain=forward protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list=”port scanners” address-list-timeout=1d comment=”Mark Source ip port scanner to Address list ” disabled=no
/ip firewall filter add chain=forward protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=1d comment=”NMAP FIN Stealth scan”
/ip firewall filter add chain=forward protocol=tcp tcp-flags=fin,syn action=add-src-to-address-list address-list=”port scanners” address-list-timeout=1d comment=”SYN/FIN scan”
/ip firewall filter add chain=forward protocol=tcp tcp-flags=syn,rst action=add-src-to-address-list address-list=”port scanners” address-list-timeout=1d comment=”SYN/RST scan”
/ip firewall filter add chain=forward protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack action=add-src-to-address-list address-list=”port scanners” address-list-timeout=1d comment=”FIN/PSH/URG scan”
/ip firewall filter add chain=forward protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=1d comment=”ALL/ALL scan”
/ip firewall filter add chain=forward protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=1d comment=”NMAP NULL scan”
/ip firewall filter add chain=forward src-address-list=”port scanners” action=drop comment=”Drop port scanners” disabled=no
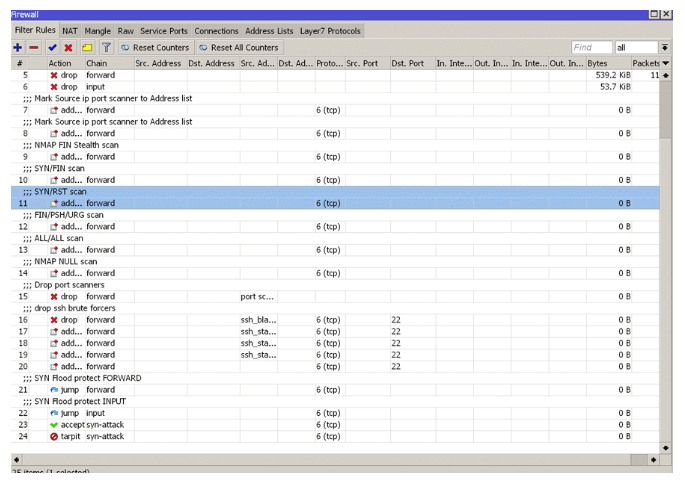
At the end of these rules, one should look at the following in the firewall section of the router:
>> FlashStart protects you from a vast array of threats and blocks access to malicious sites ? Request a quotation or try it now
6. Protection from brute force attacks
We will use the following rules to protect ourselves from brute force attacks on the network. We will paste the following rules into the console:
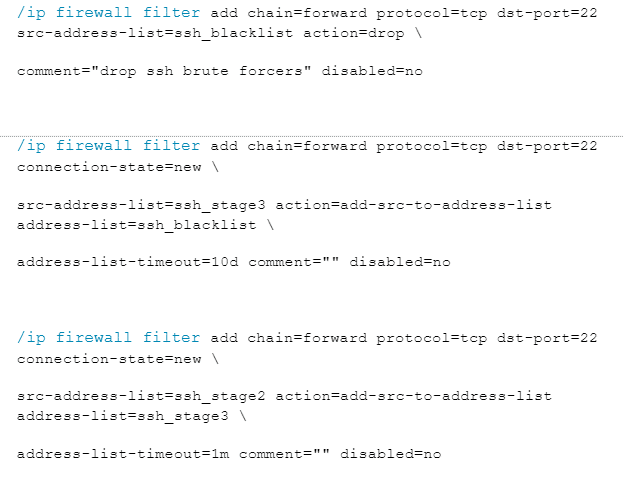
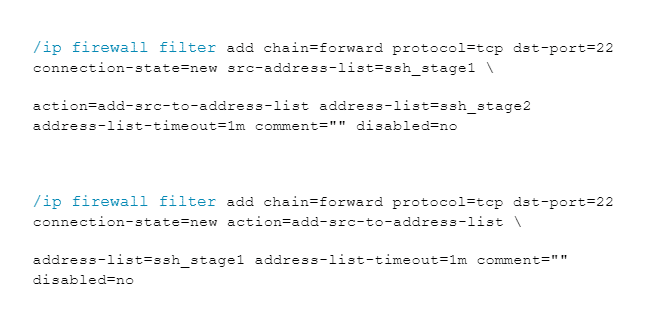
7. Protecting the network and the router from SYN-type attacks
TCP is a connection-oriented protocol, which means that, before sending any kind of data, a connection must be established. Connection initiation in the TCP protocol occurs with a three-way message exchange:
SYN: synchronization message, the first message sent to establish the connection
SYN/ACK: a SYN message is sent from the remote host, along with an ACK message (confirmation of the first SYN received)
ACK: confirmation of the SYN message received by the remote host
At the end of this exchange, the connection is established, and it is ready to send data.
8. SYN attacks
An attacker can exploit the operation of the protocol by sending thousands of SYN messages, with the goal of achieving denial of service by depleting the resources. Leaving thousands of SYN sessions open (to which the attacker will not respond) can produce high resource consumption, making the router or service inaccessible. We will apply the following protection rules to protect the network and our router as protection and design of the UTM firewall we are creating.
/ip firewall filter
add action=jump chain=forward comment=”SYN Flood protect FORWARD” connection-state=new \
jump-target=syn-attack protocol=tcp tcp-flags=syn
add action=jump chain=input comment=”SYN Flood protect INPUT” connection-state=new \
jump-target=syn-attack protocol=tcp tcp-flags=syn
add action=accept chain=syn-attack connection-state=new limit=400,5:packet \
protocol=tcp tcp-flags=syn
add action=tarpit chain=syn-attack connection-state=new protocol=tcp tcp-flags=syn
>> Ensuring the best protection from malware is necessary to live an increasingly connected life with peace of mind
9. General protection rules
The following rules will help us further protect the network; their use is recommended.
We will create a list of addresses with the name “not_in_internet” which we will use for the firewall filtering rules:
/ip firewall address-list
add address=0.0.0.0/8 comment=RFC6890 list=not_in_internet
add address=172.16.0.0/12 comment=RFC6890 list=not_in_internet
add address=192.168.0.0/16 comment=RFC6890 list=not_in_internet
add address=10.0.0.0/8 comment=RFC6890 list=not_in_internet
add address=169.254.0.0/16 comment=RFC6890 list=not_in_internet
add address=127.0.0.0/8 comment=RFC6890 list=not_in_internet
add address=224.0.0.0/4 comment=Multicast list=not_in_internet
add address=198.18.0.0/15 comment=RFC6890 list=not_in_internet
add address=192.0.0.0/24 comment=RFC6890 list=not_in_internet
add address=192.0.2.0/24 comment=RFC6890 list=not_in_internet
add address=198.51.100.0/24 comment=RFC6890 list=not_in_internet
add address=203.0.113.0/24 comment=RFC6890 list=not_in_internet
add address=100.64.0.0/10 comment=RFC6890 list=not_in_internet
add address=240.0.0.0/4 comment=RFC6890 list=not_in_internet
add address=192.88.99.0/24 comment=”6to4 relay Anycast [RFC 3068]” list=not_in_internet
10. Basic rules of MikroTik firewall
» Packets with connection status = established, related, added to FastTrack for higher data transmission speed; the firewall will work only with new connections.
» Remove the invalid connection and register with the “invalid” prefix;
» remove attempts to reach non-public addresses from the local network; first apply address-list=not_in_internet; “brdige” is the local network interface; log=yes with “!public_from_LAN” prefix.
» Discard incoming packets that are not “natted”; ether1 is the public interface; log attempts with the prefix “!NAT.”
» Switch to the ICMP chain to remove unwanted ICMP messages.
» Discard incoming packets from the internet which are not public IP addresses; ether1 is a public interface; log attempts with the prefix “!public.”
» Discard packets from the LAN that do not have a LAN IP; 192.168.88.0/24 is the subnet used in the local network.
/ip firewall filter
add action=fasttrack-connection chain=forward comment=FastTrack connection-state=established,related \
add action=accept chain=forward comment=”Established, Related” connection-state=established,related \
add action=drop chain=forward comment=”Drop invalid” connection-state=invalid log=yes log-prefix=invalid \
add action=drop chain=forward comment=”Drop tries to reach not public addresses from LAN” dst-address-list=not_in_internet in-interface=bridge log=yes log-prefix=!public_from_LAN out-interface=!bridge \
add action=drop chain=forward comment=”Drop incoming packets that are not NAT`ted” connection-nat-state=!dstnat connection-state=new in-interface=ether1 log=yes log-prefix=!NAT \
add action=jump chain=forward protocol=icmp jump-target=icmp comment=”jump to ICMP filters” \
add action=drop chain=forward comment=”Drop incoming from internet which is not public IP” in-interface=ether1 log=yes log-prefix=!public src-address-list=not_in_internet \
add action=drop chain=forward comment=”Drop packets from LAN that do not have LAN IP” in-interface=bridge log=yes log-prefix=LAN_!LAN src-address=!192.168.88.0/24
11. ICMP Protection
ICMP protocol restriction, which may also be combined with packet size, is recommended in order to prevent possible malicious tunneling. The following rules should be applied:
/ip firewall filter
add chain=icmp protocol=icmp icmp-options=0:0 action=accept \
comment=”echo reply”
add chain=icmp protocol=icmp icmp-options=3:0 action=accept \
comment=”net unreachable”
add chain=icmp protocol=icmp icmp-options=3:1 action=accept \
comment=”host unreachable”
add chain=icmp protocol=icmp icmp-options=3:4 action=accept \
comment=”host unreachable fragmentation required”
add chain=icmp protocol=icmp icmp-options=8:0 action=accept \
comment=”allow echo request”
add chain=icmp protocol=icmp icmp-options=11:0 action=accept \
comment=”allow time exceed”
add chain=icmp protocol=icmp icmp-options=12:0 action=accept \
comment=”allow parameter bad”
add chain=icmp action=drop comment=”deny all other types”
Eventually, we will have a firewall to protect us from attacks, along with FlashStart protection. We have designed a UTM firewall.
>> FlashStart is the DNS filter tool against malware and unwanted contents ? Request a quotation or try it now
12. What is a UTM firewall?
The term UTM stands for “Unified Threat Management.” A UTM firewall has the following features:
» Antivirus.
» Firewall protection on 3/ 4 levels.
» Intrusion detection and prevention systems “IDS/IPS.”
» Antiphishing
» Content filtering
The combination of Mikrotik and Flashstart is an excellent alternative for designing a cost-effective UTM firewall.
Flashstart gives us the opportunity to design together with Mikrotik a UTM firewall with high response capabilities.
>> FlashStart provides the best malware protection and satisfies all of the aforementioned points ? Request a quotation or try it now
13. General overview
We have seen the existing types of attacks and how to prevent, detect, and respond to various attacks. The combination of FlashStart and MikroTik can greatly increase a network’s protection.
It is not enough to create thousands of rules in a firewall if an unsuspecting user on our network happens to enter a harmful site or experience a type of attack such as malware. FlashStart is going to be the prevention solution for such attacks. Designing a UTM firewall using FlashStart gives us a greater ability to react and respond to an attack.
If our network is under attack or a malicious user is trying to take over our services or perform brute force attacks, MikroTik will help us in those situations.
I hope that this guide has helped you to protect your network with MikroTik and FlashStart.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.