
Brand spoofing, what it is and how to protect oneself
1. What brand spoofing is
Brand spoofing is an online scamming technique that exploits identity spoofing. This means that the attacker uses a brand identity to encourage actions that lead to the next scam. An example? A text message on behalf of the Internal Revenue Service asking you to click on a link and enter sensitive data on a web page.
There are several tools that are exploited for brand spoofing. Spoofing can take place at the IP level (IP spoofing), or at the domain level (domain spoofing), through an email message (email spoofing), a chat message, or a text message.
The technique involves the cybercriminal’s impersonation of a well-known and recognizable brand in an attempt to steal credentials or other potentially sensitive information. Brand spoofing is a highly successful attack technique used by hackers to steal data for use in future scams. Posing as a brand that is familiar to the recipient, attackers trick victims into clicking on a link or an attachment in the email.
2. The risks of brand spoofing
The consequences of brand spoofing can be disastrous for the entire organization to which the trapped employee belongs. One can, in fact, take a personal risk, for example, by introducing home banking access data as a result of clicking on a link to a web page, apparently from one’s own bank, or by providing access data for paid services – where perhaps the method has been set up – or, again, personal, health, or credit card data, etc.
This information may be used right away, for example, to change the services to which one subscribes, or to make purchases with the unfortunate person’s credit card. Additionally, it is also easy for the personal information collected to be bundled into packages of thousands of data to be offered for sale to the highest bidder on the Dark Web.
However, a brand spoofing activity directed at one employee can also have disastrous consequences for the entire corporate network. If, in fact, the extorted data involve access to corporate applications (the Office 365 account for example), then it is easy for the attack to continue within the network. This could mean theft of corporate or user and consumer data, network and application configuration changes, blocking of activities, and, perhaps, ransom demands (ransomware).
There is also a reputational risk for the brand to consider. The user who finds himself at the center of brand spoofing naturally tends to think that the brand itself is somehow responsible. Even if this is not true, the user may think that the brand did not anticipate the malicious use. On the other hand, if an employee runs into brand spoofing, the company may be blamed for incompetence, with obvious consequences for its reputation.
3. How to fight it
As mentioned, brand spoofing uses several tools. The most common are email, chat messages, and text messages. We will see, depending upon the tool, how to protect against nasty surprises.
Today, it is very easy to reproduce a page or an entire website, to the point where it is difficult to detect the scam. Brand spoofing via email, the most common, involves using a sender’s email address that is slightly different from what the official address might be, or, perhaps, with the sender’s name visible (e.g., Apple Support), which corresponds to a very strange email address that is not immediately visible. Only through careful checking can one avoid falling into the trap.
Additionally, messages can be written in flawless English, although this is often not the case. Finally, links that appear in the email message or sms can be masked (click here) or shortened (bit.ly) so that the actual path is not immediately visible.
In short, brand spoofers have become particularly skilled and play upon the recipient’s inattention, haste, and superficiality. Often, messages demand immediate action and come from institutions, creating anxiety, which is the natural enemy of attention.
In addition to brand spoofing via email or messaging, there are more elaborate ones (IP and domain spoofing) in which one acts directly on the brand’s IP address or domain name, creating cybersquatting attacks (domain grabbing, domain squatting, typesquatting, etc.). No matter what they are called, the goals are always the same: fraud or theft of personal and sensitive data.
How does one combat a brand spoofing attack? By means of prior knowledge and a web browsing filter. First of all, it is good to know that a bank or institution would never send email or text messages that ask users to click on a link. At most, the institution will send an email alert, requesting a follow-up contact.
When faced with a suspicious text message, therefore, the advice is to ignore it. Also, possibly, contact the call center of the named brand or entity to ask for confirmation that the message was sent. In the case of an email message, on the other hand, before taking any action, it is a good idea to check the recipient’s email address, not the name displayed but the address. If it looks strange, discard the message.
Next, we take a careful look at the text of the message. If you discover any errors in English and are asked to click on a link immediately, it is most likely a spoofing message. Finally, it is important to check the link without clicking on it. Hovering over it with the mouse, we see, usually at the bottom left of the screen, the actual full address to which one would link.
Again, it is immediately apparent whether or not the page one is being asked to access is the page of an official brand site.
>> FlashStart protects you from a wide array of threats and blocks access to malicious sites ? Request a quotation or try it now
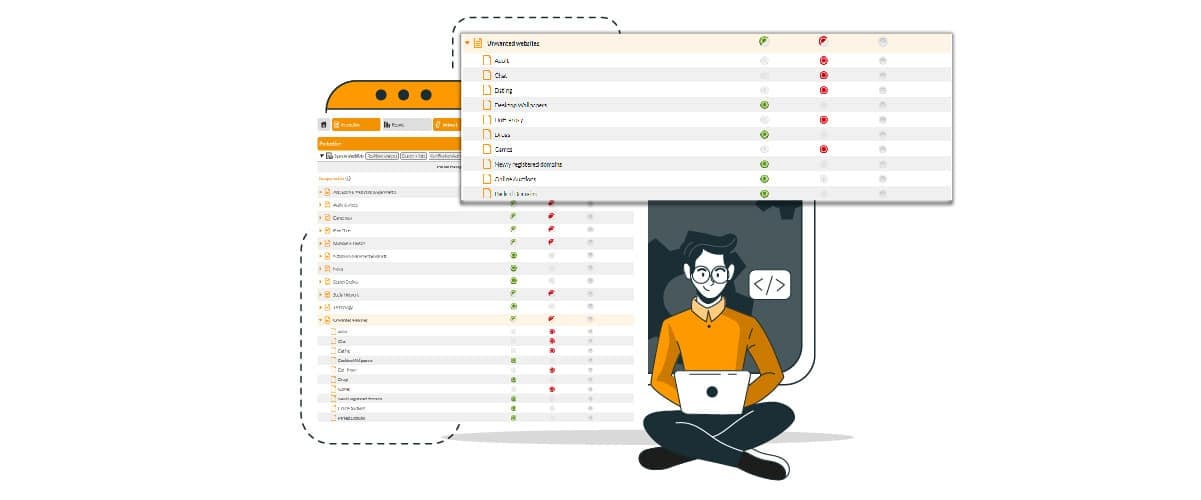
4. Using a DNS filter
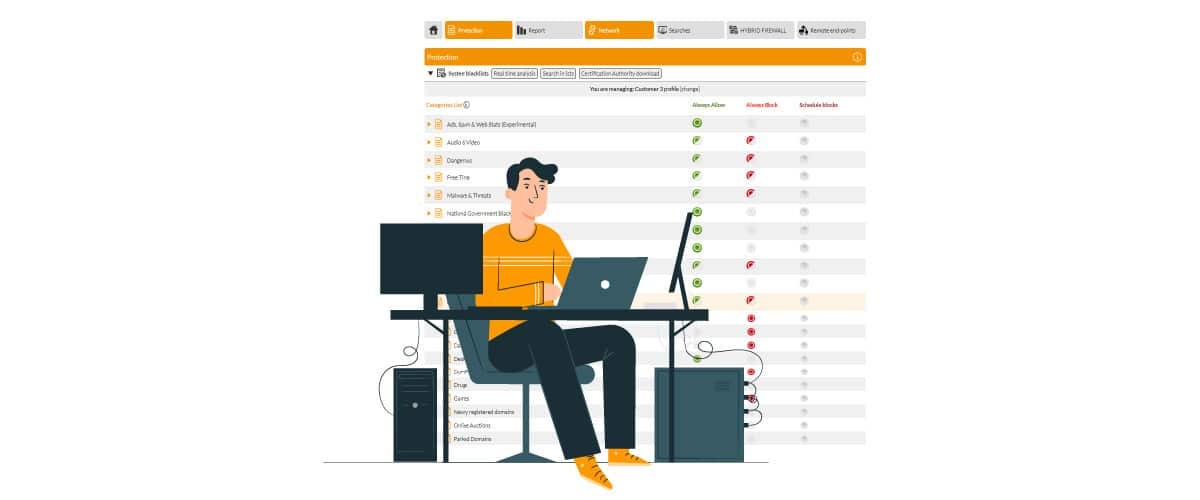
A good way to protect the company (also) from brand spoofing is to use a DNS filter. What does this mean? The solution, which is also available in the cloud, is designed to block access to any risky site. Without getting into too many technicalities, we need only know that DNS filtering is more accurate. DNS is the protocol that translates a domain name into the address of the server that hosts it (the IP of that computer). This is necessary because the computer does not understand the instruction “connect to flashstart.com,” but “connect to IP 151.139.128.11.”
A DNS filter checks the quality of the server which has that address, not falling for the tricks that malicious people can use in masking domain names and web page contents. The DNS filter checks whether or not that server’s address is blacklisted; if so, it prevents access to it.
FlashStart provides several DNS filtering solutions available for businesses, schools, and institutions, as well as for home browsing.
It is also a powerful and cost-effective alternative. Capable of filtering about 2 billion website queries, FlashStart DNS protects the browsing of 25 million users every day, is present in more than 150 countries around the world and in about twelve thousand businesses, schools, and public administrations, and is delivered, also as a service, by 700 certified partners. In conclusion, let’s look at the unique features of FlashStart DNS Filter at a glance.
» Frequent updating of blacklists: FlashStart checks 200 thousand new sites per day.
» Guaranteed low latency
» Broad possibility of customizing the solution
» Ninety categories of malicious sites and geoblocking to screen out countries considered to be dangerous
» Use of artificial intelligence to improve the quality of blacklists and for latency
» Ease of configuration and management
» Native integration with Microsoft’s Active Directory to speed up the work of system administrators in schools, institutions, and small businesses
» Worldwide LAN protection and roaming on end points via Anycast network
>> FlashStart is totally in the cloud and easily activated ? Request a quotation or try it now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







