Bot attacks and fraud
According to some estimates, internet traffic generated by bots affects up to 50% of the total internet traffic worldwide. But what are bots? Why is it important to safeguard one’s networks from bot attacks and fraud? In this article we discuss what bots are, when they can have positive effects, and how FlashStart helps us secure our networks against bot attacks and fraud.
1. Bots: what are they?
Bots and, in particular, internet bots, are programs that complete specific tasks automatically. They work through the internet and, nowadays, are so widespread that they have led to the creation of specific vocabulary. For example, “bot traffic” is used to refer to traffic generated by these automated programs to specific sites, platforms, or applications.
It is not known for sure what portion of worldwide internet traffic is related to bots, but various sites report estimates ranging from 30 to 50 percent, thus a very high percentage.
And, although today the word bot is often associated with negative mental images, the term bot refers to a neural tool that, in itself, is neither good nor bad but simply deals with performing relatively simple and highly repetitive tasks at an extremely high speed.
1.1 Googlebot: an example of bots useful to users
Platforms such as Google and Facebook use bots “for good,” that is, to provide better service for the benefit of the user. In the case of Google, there are two Googlebots, also called web crawlers, that the platform uses to perform repetitive actions whose outcome is aimed at improving the experience of users:
» Googlebot for desktop: a desktop crawler that simulates a user who uses a desktop computer
» Smartphone Googlebot: a mobile crawler that simulates a user who uses a mobile device.
These two tools, and particularly the second one, in line with the fact that we are continuing to move toward the use of mobile devices for access to the web, are concerned with regularly exploring the web and finding new pages to be “indexed,” that is, to be added to the indexes of Google search results. In this case, automating the program is useful because it makes new results available more certainly and quickly in users’ Google searches.
Facebook offers a similar service, called Somiibo, which handles the automatic management of Facebook pages with the aim of expanding the audience of users who are interested in the page and offering a whole range of services that lean toward automatic marketing.
> FlashStart protects you from a wide array of threats and blocks access to malicious sites ? Request a quotation or try it now
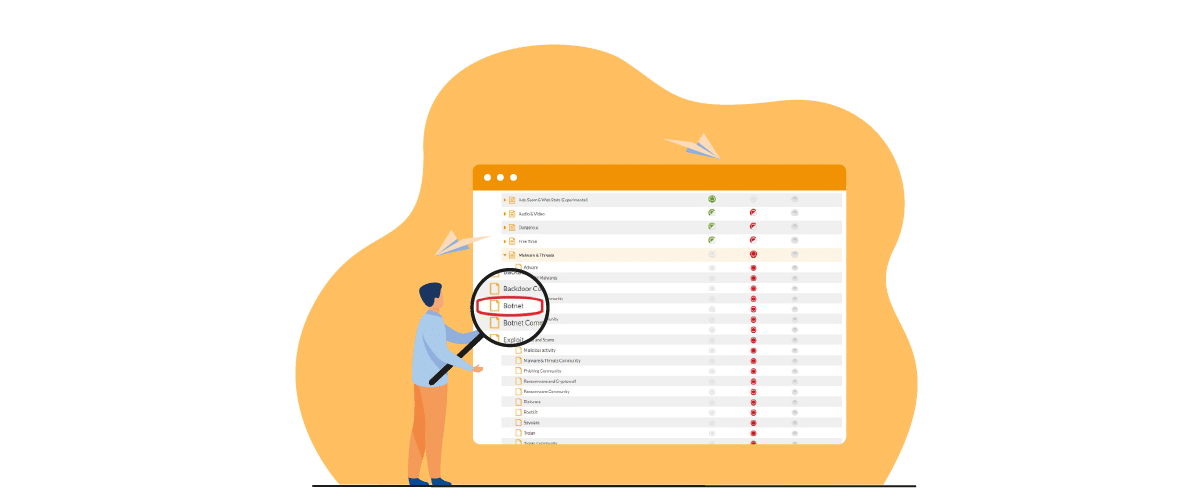
2. Bot attacks and fraud: how do they work?
“Bot attacks and fraud” refers to all types of online fraud performed with the help of or aided by malicious bots. We are really talking about “scam bots,” attacks that work at an extremely fast pace, much faster than a human can, and that prove to be profitable at various levels of the chain:
» During the preparatory phase of the attack, bots are useful for conducting ultra-fast exploratory analyses aimed at learning the vulnerability of a given website;
» During the actual attack, bots are used to automate the processes of the attack, for example, through automated phishing attempts;
» At the level of anti-attack infrastructures, bots help criminals evade controls by simulating human behavior to bypass anti-bot security measures.
Bot attacks and fraud are carried out with the help of technologies such as artificial intelligence and machine learning, which are the same ones employed by the systems used to prevent these attacks. In the case of an attack, the bot interacts with an online subject, such as an online shopping site, as a human would, and the effectiveness of the attack is due to the speed and volume of repeated attempts at very small intervals. Once the system is in motion, it only takes one successful attempt to have disruptive effects on the target company.
In some cases, the attacks are not intended to bring a quick economic benefit to the attacker but, rather, to make an attack possible at a later time. In these cases, the bot attack serves only to make the actual attack feasible, which occurs later on. An example is an attack that is used to create fake profiles on e-commerce platforms, from which the real fraud will then start at a later time.
>> FlashStart is the DNS filter tool for malware and undesirable contents ? Request a quotation or try it now
3. Types of bot attacks and fraud
Attacks and bot fraud can take on various forms and are of varying natures.
3.1 Account Takeover: profile takeover
In this type of attack, the hacker uses a bot attack in order to gain access to legitimate profiles. The attack can come in two forms:
» Credential resolution (credential cracking): in this case, there is a brute force attack aimed at obtaining a user’s credentials. In its simplest form, this attack tries all possible numerical combinations to arrive at the correct one. This attack can have disruptive effects, especially in the case of exclusively numeric pin codes.
» Credential manipulation (credential stuffing): in this case, the attacker already has valid credentials – which, for example, he purchased on the dark web – and uses the bot to test them on many other sites, hoping that the user has used the same username and password combination on multiple platforms.
Through these attacks, hackers can then take advantage of the user’s personal data and, especially in the case of platforms that rely on the user’s credit cards for their use, enjoy the use of others’ resources.
3.2 SQL injections
An SQL injection allows one to gain unauthorized access to a website’s control panel, going on to post unwanted contents or even infect site users with other malware. Access to the databases that sites rely on also involves, in some cases, direct access to confidential information of site users, such as credit information and identity documents.
3.3 Abuse of API
API abuse refers to the misuse of information that a hacker can perform when gaining access to an Application Programming Interface (API for short). APIs are used at the programming level to build bridges between two pieces of software or applications and define all the details of how communication and data exchange between the two applications should take place. Therefore, using a bot to attack an API means gaining access to information on multiple sides and also ensuring that information from multiple sources can be merged.
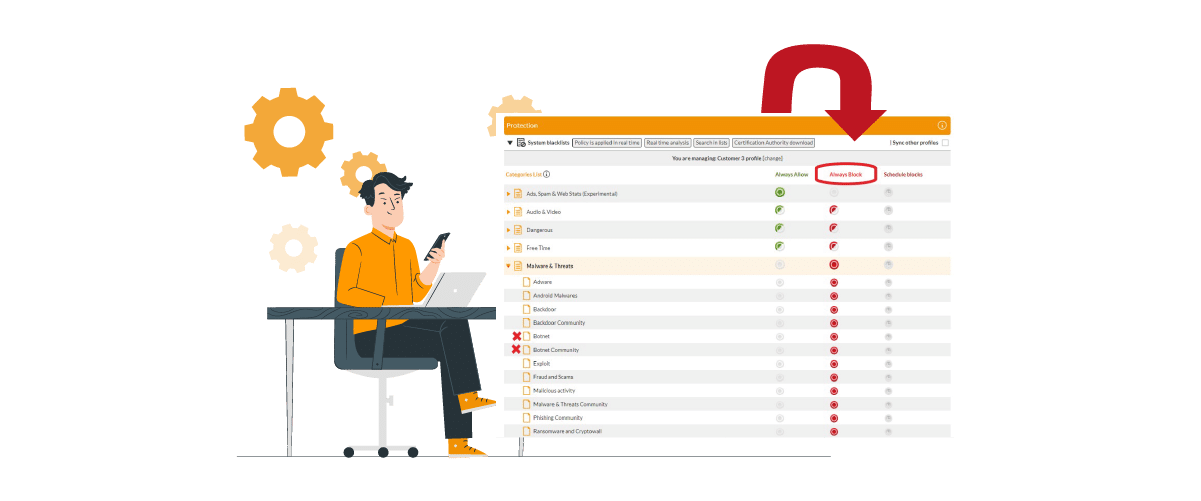
4. FlashStart: the successful ally against bot attacks and frauds
FlashStart proposes a DNS-based web filtering service that aims to block attacks at the source. DNS works at the resolution level of an internet site: when the user types the site he or she wants to reach in the search bar, the DNS protocol converts the text into numbers, therefore, into a “language” understandable to the web, and consequently “resolves” the domain, redirecting the user to the desired page.
FlashStart acts as a checkpoint at this stage: it verifies whether the site the user is looking for is trustworthy or not, and, if it is not, it blocks the domain resolution. In order to perform the verifications, FlashStart relies totally on its cloud in which there are lists of dangerous, unwanted, or distracting contents that, therefore, should be blocked. These are the FlashStart blacklists, more than eighty-five in number, which the system uses to ensure the best protection from bot attacks and fraud.
4.1 FlashStart: artificial intelligence always at your service
FlashStart uses artificial intelligence algorithms to continuously scan the web for new threats, including malware, attempted phishing attacks, and malicious bots. FlashStart’s artificial intelligence scans up to 200 thousand sites every day and supports twenty-four different languages.
Moreover, thanks to machine learning mechanisms, the tool is able to emulate the reasoning of the human mind, which enables it to learn from prior experience and become increasingly agile and accurate in its analysis.
>> FlashStart: malware protection entirely in the cloud and easily activated ? Request a quotation or try it now
4.2 FlashStart: the DNS web filter that guarantees complete protection
FlashStart protects you from a wide range of contents. In fact, the tool guarantees the blocking of three types of contents:
» Malicious contents: these are viruses, malware with the most varied forms, from the bots we have discussed in this article to attempted trawling attacks (phishing), to ransomware attacks that aim to monetize on acquired data, to DDoS attacks, which create service interruptions. Sites that lead to these types of attacks are always blocked, automatically, by the FlashStart web filter.
» Unwanted contents: these are contents related to porn, violence, drugs, etc., that you often want to block because of their very nature. The network administrator can independently choose what to do about these contents, and also as to whether to block them only for certain categories of users (e.g., minors) or for everyone.
» Distracting contents: online shopping sites, platforms for audio and video streaming contents, and social networks fall into this category.
>> FlashStart: your ally against bot attacks and fraud, anytime, anywhere ? Request a quotation or try it now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







