Web exploits: what they are and how to defend oneself (Part 1)
We wanted to devote ample space to the topic of “Web Exploit,” a topic that every IT manager should govern with domesticity; therefore, we will publish two complementary articles.
» Part 1: the present article
» Part 2: “Stay Tuned.”
1. Vulnerabilities, web exploits, patches
In order to understand what web exploits are and what they are used for, it is important to start with the concept of “vulnerability,” which, in a sense, is the enabling factor for the exploit and allows it to be used. Therefore, vulnerability and exploit are closely related: in order for a web exploit to act there must be one or more vulnerabilities.
Vulnerabilities (also called “bugs”) are the weaknesses found within software: each software is – by definition – imperfect, precisely because it is created by human beings. In order to give a sense of scale: the Microsoft Windows operating system contains more than 50 million lines of code, the set of all Google services, up to 40 times as much as Google (2 billion lines).
It is inevitable that within such complex software some flaws, some more or less serious, are hidden. These “flaws” in the security of a program are, in fact, called vulnerabilities and can be exploited to bring an attack to the computer system. Virtually every attack uses vulnerabilities (whether they be of the computer system or the human factor) to enter the system.
In order to understand the importance that a vulnerability may have – or may not have – we must assess how exploitable it actually is. In other words, a vulnerability poses a risk only if the threat is able to exploit it in order to execute an attack.
Actually, not all vulnerabilities can be exploited for malware distribution. Some may not be exploitable because security systems prevent someone from using them, or their exploitation may be too costly compared to the results that would be obtained.
A vulnerability not yet discovered or that is known only to a few, but unknown to software developers (who then had “zero days” to fix it), is called a “Zero-Day Vulnerability.” These are the most feared because if an attacker – and he alone – knows about it, he would have a weapon in his hand capable of doing serious damage. Zero-Day exploits take advantage of precisely these flaws.
When the vulnerability becomes known, it is c day, alled “n-day,” and, at this time, it is usually repaired by a software update. Such a security update is called a “patch“. When the patch is made available (by the software manufacturer), the vulnerability can be rendered harmless, but only if the patch is installed, and this – as we shall see – may not happen, still leaving the system vulnerable.
Known vulnerabilities are classified as Common Vulnerabilities and Exposures, abbreviated as CVE (“common vulnerabilities and exposures”). The Mitre Corporation, an agency funded by the U.S. Department of Homeland Security’s Federally Funded Research and Development Centers (FFRDCs), keeps this classification updated.
Each vulnerability is cataloged in the aforementioned MITRE site with the classification defined as: CVE – year – sequential number.
For example: CVE-2019-0708 is the famous vulnerability affecting the Windows Remote Desktop Protocol (RDP) which can be exploited by a Remote Code Execution (RCE) attack from the Bluekeep web exploit, which we will discuss later.
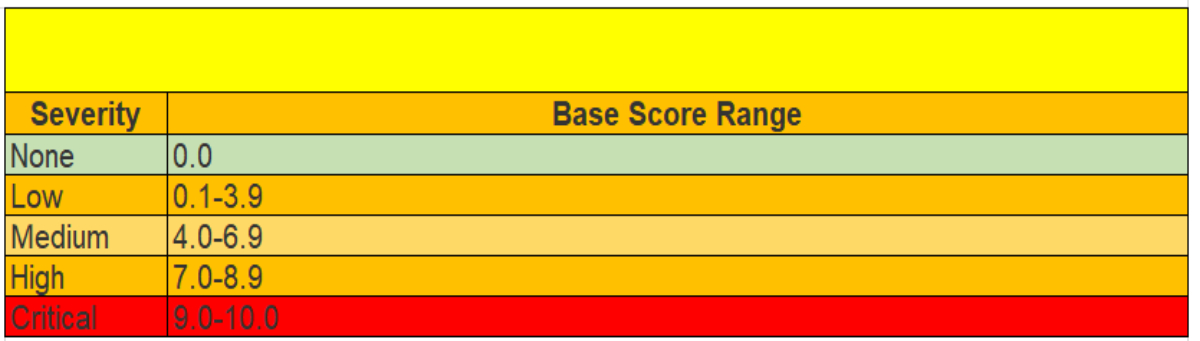
Vulnerabilities are classified according to the level (score) of severity.
One of the most widely used is the Common Vulnerability Scoring System (CVSS). This is a method of identifying the main characteristics of a vulnerability and producing a numerical score that reflects its severity. The numerical score can then be translated into a qualitative representation (such as low, medium, high, or critical) in order to help organizations properly assess and prioritize their vulnerability management processes.
CVSS is now a public standard used by organizations around the world. Its usage by U.S. agencies was recommended by the National Institute of Standards and Technology (NIST) in “NIST Special Publication (SP) 800-51, Use of the CVE Vulnerability Naming Scheme,” which was initially released in 2002.
Below, we have reproduced the CVSS v3.0 Ratings table, taken from the NIST’s NVD site, where it can be seen that the severity level of a vulnerability can range from a score of 0.0 up to 10.0 for the most critical ones.
A handy Common Vulnerability Scoring System Calculator for computing the score is also available on the same site.
An Exploit is a code (program) created to exploit a vulnerability in order to carry out an attack on a computer system: computer “exploitation” is precisely the exploitation of a vulnerability.
If the exploit is created for a zero-day vulnerability, we are speaking about zero-day exploits. These are obviously the most dreaded because there is still no patch that has closed that vulnerability.
Only the attacker has discovered that vulnerability, and only he knows how to exploit it. In order to respond to the attack, the software developer must create and release a patch, which will be able to protect only those who install it, obviously only after its release and after the vulnerability has become known.
This is precisely why zero-day vulnerabilities can have a huge commercial value: the most valuable ones are quoted as high as $2.5 to $3 million. We can see this on the website of the Zerodium company, founded by Chaouky Bekrar, who had previously created Vupen and who quotes a zero-click vulnerability for Android as high as $2.5 million.
There are many companies that-more or less transparently-trade these vulnerabilities.
These include Crowdfense, a Dubai-based company led by Italian Andrea Zapparoli Manzoni (a member of Clusit), which launched its first “Bug Bounty Program” in April 2018, allocating a budget of $10 million to purchase zero-days vulnerabilities. In 2019, the program was expanded with an additional $15 million.
The price recognized for each individual vulnerability submission ranges from US$100,000 to US$3 million. The program targets software researchers and has mainly police, intelligence, and government as clients. Crowdfense’s stated purpose is to make the market for buying and selling vulnerabilities and exploits transparent and legal.
>> FlashStart protects you from a vast gamma of threats and blocks the access to harmful sites ? Request a quotation or try it now
2. Exploit kits
The web exploit market has become industrialized and more and more articulated. Exploit kits have emerged: these are software tools that make it possible to automate the exploitation of a vulnerability and execute a malicious code.
Due to their highly automated nature, exploit kits have become one of the most popular methods of distributing mass malware or remote access tools (RATs) by criminal groups, lowering the barrier of entry for attackers.
The creators of exploit kits offer these programs on the Web and, especially, on the Darkweb, along with a management interface and a set of attackable vulnerabilities, together with a set of features that make cyber attacks simple and effective and, in most cases, automated, as well.
Therefore, today becoming a cybercriminal is easy, even if one does not have great technical skills: one can “rent” exploit kits from the platforms that manage them: this is the Cybercrime-as-a-service phenomenon.
Among the historical and most famous exploit kits we can mention: Angler, Neutrino, Nuclear. These are now outdated, but they had an important history in previous years and were often used to convey ransomware.
Many web exploit kits are built to exploit vulnerabilities in specific programs: the much targeted Adobe Flash Player, a browser plug-in, widely used up to a few years ago and known to be a “mine” of vulnerabilities, which were exploited, for example, by Neutrino (and more!). Fortunately, since late 2020, Adobe itself has abandoned it.
Now that Flash is no longer in use, and modern browsers support automatic updates (the most popular browser Chrome receives an average of one update per week!), exploit kits are less effective overall.
Despite the fact that security measures have improved, especially when it comes to Web browsing, some Web exploit kits continue to be tools used for cybercrime.
Let’s look at an example of an exploit in action in an attack dubbed “drive-by-download” (or “trough”):
» The exploit starts from a compromised website. The compromised page will divert web traffic to another page. Within the destination page is a code (injected by the attacker who compromised the site) that profiles the victim’s device for any vulnerable browser-based applications. If the device is fully patched and updated, the exploit stops. If, however, there are vulnerabilities, the compromised website silently redirects network traffic to the exploit.
» The exploit uses a vulnerable application to secretly execute malware on a host. The most targeted applications are Adobe Flash Player, Java Runtime Environment, Microsoft Silverlight. It can also use the web browser: the web exploit is sent as a code within the web traffic.
» If the exploit is successful, it sends a payload to infect the host. The payload can be a file downloader that retrieves other malware or the malware itself. In more sophisticated exploit kits, the payload is sent across the network as an encrypted binary that, once it arrives on the victim’s host, is decrypted and executed. The most common payload today is ransomware, but there are many others, including botnet malware, infostealers, and banking Trojans.
» In conclusion, the web exploit is the tool in charge of being the carrier for the actual attack (payload).
3. Web exploits: some famous cases–and where to find them
Let’s review the history of some famous web exploits. We will begin with some historical and now inactive cases.
Neutrino was one of the most popular exploit kits, starting in 2016. It exploited primarily Flash vulnerabilities known as CVE-2016-4117 and CVE-2016-1019. It was used as a vector to spread some popular types of ransomware such as Crypwall, Cerber, and Locky.
Angler, in addition to chronic Flash vulnerabilities, exploited those in Microsoft Silverlight, such as CVE-2016-1034. This was also used as a vector to spread certain types of ransomware.
Let us now look at some of the most recent and famous web exploits responsible for history-making attacks.
>> With FlashStart you can block undesired or inappropriate content: request a quotation or try it now
In a matter of only a few days, the WannaCry ransomware struck in 150 countries worldwide, with more than 300,000 attacks detected. One of the countries hardest hit was the United Kingdom, where WannaCry crashed at least twenty-five hospitals and put the National Health Service (NHS) in crisis.
The peculiarity of WannaCry, when compared to other ransomware, was precisely the use of the EternalBlue exploit, which exploited a vulnerability in SMBv1 (a network file sharing protocol, Server Message Block, used by Microsoft Windows systems).
The vulnerability classified as CVE-2017-0144 (MS17-010 by Microsoft) had already been closed by Microsoft on March 14, 2017.
However, Windows XP and Windows Server 2003 systems were no longer protected (end of support as of April 8, 2014) and thus, unpatched, were easily hacked by EternalBlue.
The WannaCry affair has an additional twist: it appears that EternalBlue was created by the NSA (the U.S. National Security Agency).
However, the NSA had the exploit stolen by a hacker group called The Shadow Brokers (TSB), who spread it on the Darkweb, making it available to attackers who used it. In this case, the attack was done by the state-sponsored hacker group from North Korea known by the name Lazarus.
WannaCry and EternalBlue should have made us realize the importance of security updates. Instead, – it seems unbelievable – today, six years later, there are systems that still have Windows XP and Windows Server 2003 installed and are, therefore, easily attacked by this exploit which is still active and in use.
Another popular web exploit is Bluekeep: it exploits a remote code execution (RCE) vulnerability identified as CVE-2019-0708 which affects Windows Remote Desktop Services and can allow criminal hackers to access a vulnerable machine even without authentication.
It allows a flaw to be opened in a LAN so that malware can be spread to all connected PCs.
The operating systems vulnerable to Bluekeep are: Windows Server 2003, Windows XP, Windows Vista, Windows 7, Windows Server 2008, and Windows Server 2008 R2, all systems already declared end-of-life by Microsoft and no longer upgradeable.
Web exploits and exploit kits today are readily available – for a fee and, sometimes, even for free – in dark web forums, but not only there.
Many of them are now in the public domain, and anyone can download them from well-known websites. One of the most popular is https://www.exploit-db.com/ where you can also find EternalBlue and Bluekeep ready for download… and many others!
Part 2 of the article coming out soon….
4. The author
Giorgio Sbaraglia, an engineer, provides consulting and training in information security and privacy.
He teaches courses on these topics for many leading Italian training companies, including ABIFormazione and 24Ore Business School.
He is the scientific coordinator of the master’s program “Cybersecurity and Data Protection” at 24Ore Business School.
He is a member of the CLUSIT Scientific Committee (Italian Association for Information Security) and an “Innovation Manager” certified by RINA.
He holds DPO (Data Protection Officer) positions at various companies and professional associations.
He is the author of the books:
» “GDPR kit di sopravvivenza” (Editore goWare),
» “Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” (2a edizione 2022, Editore goWare),
» “iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” (Editore goWare).
He is a contributor to CYBERSECURITY360 , Cybersecurity group’s specialist publication.
He also writes for ICT Security Magazine, for AGENDA DIGITALE, and for CLASS magazine.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.