Internet in Cloud security
The rapid diffusion of Cloud computing in companies or organizations is not only interesting from the work aspect, for those who decide to step onto the Cloud, it is also an important thing for the Internet security aspect. In this article we will describe what is meant by Internet in cloud security and we will explain how FlashStart has become one of the fastest and most secure Internet in cloud security instruments.
1. Cloud computing: the ITC movement to online
NIST, the National American Institute for Standards and Technologies defines Cloud Computing as a model that allows the on-demand access to a bunch of online ICT services – including networks, servers, data warehouses, applications and services – from everywhere through the web network in a very convenient way. These services are delivered very quickly, with very little exertion on a management level and more than often absolutely no reason whatsoever to interact with the service providers at all.
With these characteristics, cloud computing has spread in a very rapid way during the last few years, and the epidemic definitely played a big part in its diffusion. In fact, cloud computing made remote working possible during the pandemic. Depending on the company choices, their staff have been able to:
» Connect remotely to the company network by using a VPN, virtual private networks that allow the direct access to the company network from anywhere thanks to some software that is installed on the user device. The identity of the user is protected thanks to the fact that all data is encrypted and the IP address and geographical position are hidden. In this way, the VPN network protects the user from cyber-attacks.
» Access documents and data through the cloud that we could define as a true and proper online information warehouse from which you can enter from your own PC or other device that is connected by using personal credentials. Google Drive is an example of this, it lets you create files directly online and then save them onto the Internet – on the Drive – and then share them with other individuals and organizations so you can work in a concerted way.
>> FlashStart protects you from a vast range of threats and blocks access to dangerous sites → Request a quotation or try it now
1.2 The advantages of cloud computing
Amongst the principal advantages of cloud computing are elements that have particularly contributed to its success, they are:
» Performance: the better known in cloud services work in a self-service way on request and permit lots of flexibility and elastic management of resources. This is true not only on a data quantity level of which a user needs to access but also in geographical terms as the service is based on a global network of new generation data centres that are constantly updated.
» Reduced costs: cloud computing allows you to avoid purchasing big quantities of hardware and software licenses that request, apart from the initial investment, set up skills, continuous upgrades, maintenance, acquisition and management of a local data centre with all the precautions that this entails.
» Trust: cloud computing lets the company drastically reduce its costs of data backup thanks to mirroring services that create data copies in various redundant sites, directly on the service providers network, guaranteeing the company continuity in a very simple way even if the site is compromised.
It is this final point that brings us to the next subject: the development of Internet in cloud security.
2. Internet Security: forerunner and new frontier in cloud-based services.
2.1 Firewall: the wall against online threats
Traditionally, Internet security has been managed by a Firewall, true and proper walls that block access to networks from unauthorised subjects. Firewalls can be under the form of software, therefore an app that can be installed on a PC, it could also request the purchase of hardware, giving the wall concept a more realistic meaning.
A firewall analyses the Internet traffic and blocks the navigation towards suspect sites. Traditionally, these sites were organized in lists that could be bought in packets, therefore according to the firewalls quality the user was protected against a list of threats. Amongst the disadvantages of these more traditional systems there was the need for continual updates, where available, to guarantee the protection of devices against new threats.
The network security therefore depended greatly on the owners of the devices to download and integrate new updates, purchase added packets and proceed with long device reboots that would allow the complete installation of the new items, then consequently they were able to work on devices that were more secure.
2.2 Internet Security: the new frontier
Maintaining the firewall concept, Internet Security has now migrated onto the cloud. This migration has been in act for about the last twenty years but the shift has become even stronger in the last period for the objective necessity of being able to rely on more protected and secure devices.
Internet in cloud Security moves a large part of the responsibility from the users and network administrators to the service providers themselves and this is one of its principal advantages. Being cloud based, in fact, doesn’t need the user approval for installation and updates, this is because there are absolutely no upgrades to instal or accept as the cloud receives the updates from the providers and is therefore always up to date and integrated with the most recent threats.
The other big advantage of in cloud Internet security is the flexibility that allows, in geographical terms, the resource location. Seeing as the cloud is not located in a local server inside the company but is elsewhere, the in cloud access has no particular geographical necessity but, if it is available on a network, it will also be available in cloud.
In this way the in cloud Internet security makes possible the maximum flexibility of the resources, that can work in total security wherever they may be, inside the company network or in a client’s café, even during a foreign transfer. Obviously not all in cloud Internet security systems are the same and, according to your choice, the end user will be more or less protected during their movements.
>> FlashStart is totally in cloud based and is easy to activate → Request a quotation or try it now
3. FlashStart: the Internet filter instrument that is totally in cloud based
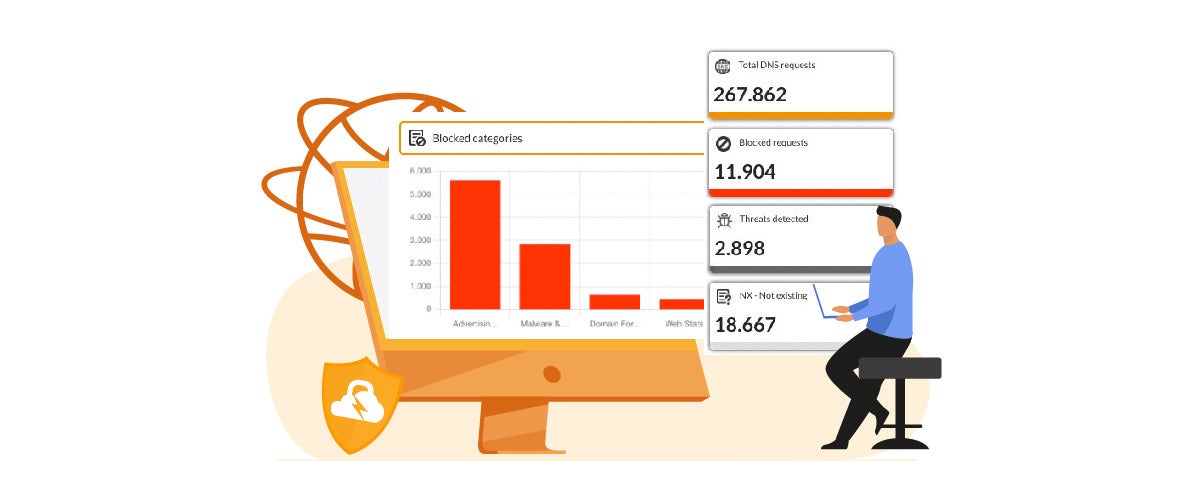
FlashStart is the in cloud Internet security instrument that is constantly updated that protects your network access wherever you may be. It functions like an Internet content filter that analyses all the Internet traffic and blocks access to sites that contain dangerous content that could compromise your devices or data security.
3.1 FlashStart: Artificial Intelligence for your protection
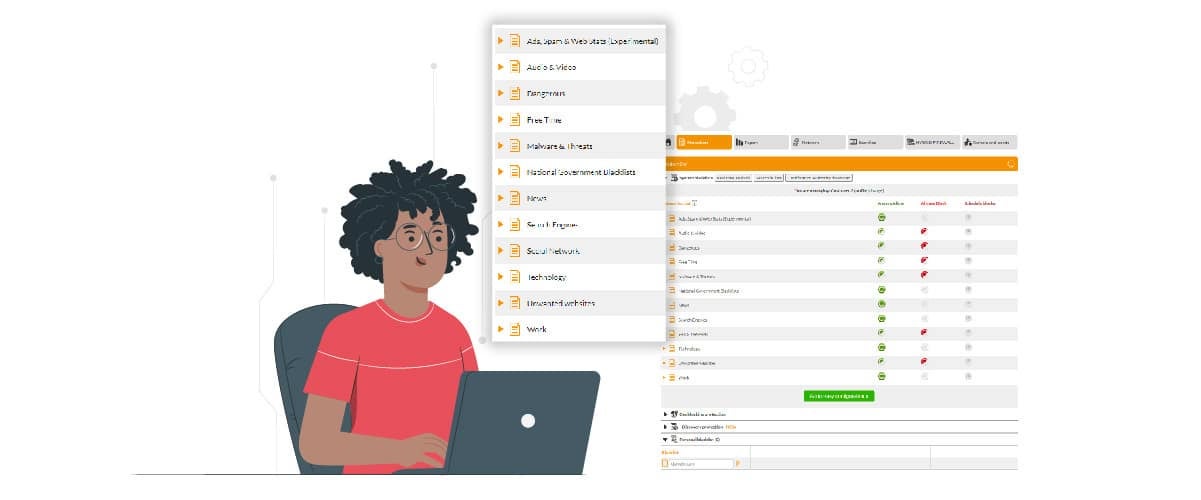
The Internet content filter from FlashStart acts like a control point for all Internet traffic travelling thought the device. In particular, when the user wishes to land on a site, the filter controls if this site is trustworthy by verifying the presence in a series of blacklists, sites that are considered to be unsure that can be found in cloud.
FlashStart guarantees the continuous updates of these lists through some Artificial Intelligence algorithms that scan the internet continuously searching for new threats. Also, thanks to Machine Learning mechanisms that imitate the functions of the human brain, the FlashStart systems learn from past experiences and store that information away so it can detect other patterns of similar behaviour, making it easier and more secure to identify dangerous content.
The Artificial Intelligence of FlashStart analyses up to 200 thousand sites a day, supporting 24 different languages. Once analysed, these sites are divided into group lists in more than 90 categories, this allows them to have what could be called an ever more complete Atlas of Internet content.
3.2 FlashStart: protection available anywhere
FlashStart guarantees the protection of devices wherever they may be. In fact the filter can be applied on two levels:
» On the company router level: applying the content filter from FlashStart on this level signifies guaranteeing all the devices that are connected to the network that is generated by that router, they are all protected from malware and other internet threats. This is also valid for any eventual other devices such as those of foreign clients or third parties that require access to the network.
» End point level: as we said before, in cloud internet security allows, on a theoretic level, the protection of devices wherever they may be. Not all service providers however are capable of guaranteeing this point. FlashStart does: it has developed the ClientShield application that represents a true and proper shield against threats for devices on which it is installed, thus guaranteeing the user protection wherever they may be.
3.3 FlashStart: not just malware protection
Finally, FlashStart guarantees complete protection in such that it protects your network and devices against malware and other dangerous content but the network administrator can decide the system rules in a way to block access also to:
» Undesired Content: FlashStart protects your network, it therefore also protects your company, whilst navigating towards illicit sites or ethically inappropriate ones. These include, but are not limited to, pornography, weapons or drugs trading, online gambling.
» Content that creates distraction: given the pervasiveness of Internet usage today, in many ways, from entertainment, purchasing, information, FlashStart has also considered company efficiency. Its filter can be set up in a way which diminishes or blocks the access to sites that create a distraction and therefore have a negative impact on worker efficiency, such as social networks, video and audio streaming platforms and online shopping sites.
The modes can be directly chosen by the network administrator in such that the system guarantees maximum flexibility in terms of sites to block, timeframes in which to activate these blocks and on which profiles to activate them.
>> FlashStart is the leader in cloud Internet Security and protects you against malware and undesired content → Request a quotation or try it now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







