How to activate two-factor authentication
1. How safe can a password be?
Imagine a password like this one:
$BjG46ebD3@GfJ86u/y%C3)i
How safe is it?
It is surely very strong, practically impossible to crack with a brute force attack, which would require several billion years to decipher it.
As we explained in our previous article: such a password, 24 characters long, has an S entropy of 157 bit, so even more than the maximum advised entropy of 128 bit.
But still, it could be not enough…if it were discovered, for example because of negligence or because of a mistake by the user, who may have communicated it by taking the bait of a phishing email.
Or he might have written it on a post-it left in view…something that happens way too often!
Therefore, we cannot exclude that a password – as safe as it may be – is stolen or discovered.
Authentication based uniquely on the password is intrinsically weak, whichever the password is, since the account security depends on a sole factor, that is, the password itself.
In Cybersecurity, defense must be realized in layers: this is why we talk about “layered security”, to avoid what the famous Kevin Mitnick called the “M&M effect”.
M&Ms are those popular candies with a sugar coating: hard on the outside…but soft inside! Once the shell is broken, we are inside the M&M.
If we carry this image to the realm of cybersecurity: it is important to have a second defensive layer, in case the first one fails. This concept – which is fundamental – shall be applied also to passwords and, more widely, to the entire authentication process.
To access all types of digital systems (laptops, credit cards, websites, etc.) we are first asked to introduce ourselves by declaring our username.
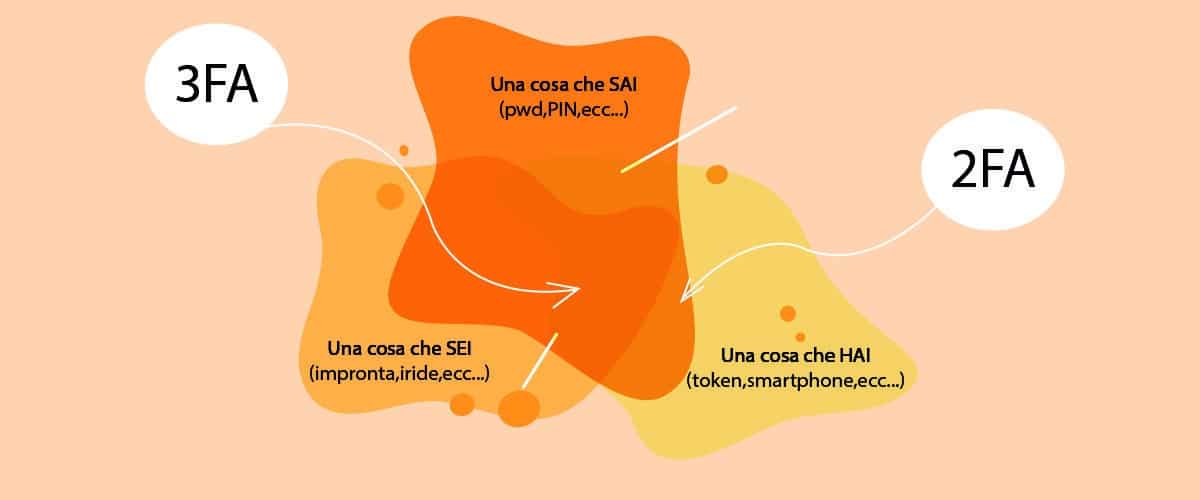
Then, we will have to show that it’s really us: this is the “authentication” phase and it can happen in one of three ways:
» Knowledge: “something you know”, for example a password or PIN;
» Ownership: “something you have”, like a smartphone or a security token (those small “keys” that banks used to distribute and that generated a 6-character code, or a Fido token);
» Inherence: “something you are”, like your fingerprint, face or eye recognition, or other biometric features.
In general, a sole factor is required (usually a password). In order to increase the security level, “strong authentication” techniques have been introduced, or two – or more – factor authentication.
Also called 2FA or MFA (“Multi Factor Authentication”), today this is the safest protection system we can use. Or better, we must use.
We talk about 2FA when two factors are used and 3FA when three factors are required (a lot less common, it is for example used in 3rd level SPID).
The condition that allows it to be defined as “two-factor authentication” is verified only when the two factors used are of different origin: in other words, if for example you use “one thing you know” + “one thing you have”.
While an authentication based on two passwords cannot – consequently – be deemed 2FA (since they are two factors of the same nature).
2. How does MFA work?
MFA requires at least two of the three factors listed above: after typing your account’s password (that usually represents the first factor), you will be asked to input a second factor, which in most of the cases is a PIN or a code obtained through a smartphone (as a text message or via a dedicated app) or through a physical token.
Differently from the password, this second code cannot de facto be cracked since it is casually generated by an algorithm and lasts for a very little time (usually 30 seconds). For this reason it is also called OTP: “one time password”.
The second factor can also be biometrical: “something you are”. An example is found in several bank apps for smartphones: to open the app, and also to carry out some operations (like a bank transfer), we are required to identify ourselves a second time using our fingerprint or face recognition.
3. How can you obtain the second authentication factor?
There are technically four ways:
» Through a text message we receive: this is a very widespread solution, but also the least secure one, because by now the vulnerabilities of the Signalling System No. 7 Protocol (SS7) are well known. SS7 is a very old protocol (born in the 70s) and that is not safe.
Moreover, there is an even worse risk: you could end up in a fraud known as “SIM swap fraud”, hence the cloning of our SIM by an ill-intentioned individual who – in this way – will receive the text message with the numerical code for the second authentication instead of us.
The NIST in SP 800-63B “Digital Identity Guidelines” in chapter 5.1.3 – Out of Band Devices – deprecates the use of text messages to receive the second OTP factor, exactly for the risk of SIM swapping.
And finally, something that should not be overlooked: this system obliges us to supply our mobile phone number to a social network or a website: this might not be appreciated in terms of privacy.
» Using dedicated apps that generate a 6-number code to be inserted in the browser: when a website makes this option available, I suggest choosing it, since it is the most practical method, it does not require phone coverage and is very safe. The most common apps that can be used – which are all free – are Authy, Google Authenticator, Microsoft Authenticator. Some Password Managers, for example LastPass and 1Password, but not only them, implement this service. Authentication through apps is very popular now and, over the last few years, there are more and more websites that list it among the possible options.
» With a hardware token: a very safe option but that is still not that common. Every account that supports this function is connected to a physical access device similar to a USB key, realized according to the U2F Security Key Standard. This is a 2FA open authentication protocol developed by Google and Yubico in 2013 and that today is managed and regulated by FIDO Alliance (founded in 2012).
U2F Security Keys are produced by Google as Titan Security Keys, by Feitian and especially by Yubico, with prices starting from 25€ for the basic models and up to 80-90€ (picture 3 shows the Yubico range).
It’s a very safe system that can be used also by companies for authentication into laptops and company services, with a notable improvement in security. It is definitely not the most practical and neither the cheapest: on top of having a cost, not all services support it. Moreover, it requires a direct connection to the laptop for authentication: in the case of a PC this happens through the USB port. But in the case of a smartphone U2F Security Keys must be equipped with an NFC (Near Field Communication) or Bluetooth or, in the case of iPhones, they must have aLightning port, with a much higher cost. And, last but not least, we must always have the Security Key on ourselves in order to carry out the authentication, paying attention not to lose it. This is why producers advise to create an extra copy of it…..
» With a Push notification: in this case, two-factor authentication is carried out through a notification from an app linked to the service in use, but installed on another device. This system is used mainly in Internet banking, through proprietary apps provided by every bank and installed on the smartphone. It’s a very safe mode and it’s also easy: after typing in your username and password, the individual will receive a push notification on the smartphone, which will ask him to authorize the access through the application of the bank itself. Often, this authorization is given through a fast and practical biometric authentication: fingerprint, face recognition or other.
4. How do you activate two-factor authentication?
The activation mode is more or less always the same: after registering to the website, you access “Settings” (the name can vary a bit, but it is always the page where, for example, we go to change the password).
You choose to activate 2FA and then the website will guide us through the guided procedure and will ask us how we wish to receive the code: the most widespread method on all websites (but not advised!) is through a text message, and in this case we have to indicate a “trustworthy” smartphone to which the code can be sent.
If we choose this option (which, as mentioned, is not the best one), we suggest you to always record two or more phone numbers, for a higher security. Later, with each text we will be asked to choose on what device we want to receive the code.
Almost all websites allow you to choose, as an alternative to the text message, to use the above-mentioned apps able to generate a temporary code (OTP). As we said, if this option is available, it’s the one we should prefer and it’s also very easy and totally free: the joining takes place through a QRcode that appears on the computer screen and which we have to scan with our smartphone’s camera.
Such an option is called “Enrollment” and it carries out the exchange of the encrypted, unique key between the website and the app, which in this way will be synchronized.
Each of these apps allows you to save the OTPs for all the websites where we enable 2FA.
At every following login, besides the username and password, we will have to input the 6-figure OTP code shown by the app and that is newly generated every 30 seconds.
There exists – on almost all websites – a convenient option that makes it possible for us to not have to input the OTP code during the next logins: this option usually appears as “this website is trustworthy” (or something similar) and has to be activated one-off.
In practice, since two-factor authentication aims to avoid accesses from laptops or devices different from ours, we could tell the website to recognize that we are logging in from our “usual” device and do not need to add the second authentication factor anymore.
5. What services does two-factor authentication offer?
With the exception of Internet banking services, where 2FA is compulsory given the European Directive 2015/2366 (known as PSD2 and that in Italy became effective on 14 September 2019), and of some other services like the Italian SPID which require it, in all other websites we are not obliged to use two-factor authentication.
It is a discretionary option, but that we strongly advise, at least for the most important services like, for example, Amazon, Apple ID (iCloud), Dropbox, Evernote, Facebook, Google, LinkedIn, Microsoft, PayPal, Twitter, Yahoo!, WordPress. And of course for all business accounts!
There are also many other websites that offer it, you can see the complete list (with the options available for each website) at this link.
6. What is the future of two-factor authentication?
According to a Juniper Research report, the number of smartphone users who will use biometric authentication systems (fingerprint, face – voice – eye recognition, etc.) will grow by over 250% in the coming 5 years.
According to the author of the report, James Moar
Secondo l’autore del report James Moar:
“The key battle now will be to convince users, particularly those in Europe and North America, that these methods are just as secure as traditional hardware-based security.”
In 2018, Google communicated that only 10% of the active accounts made use of this security measure.
Maybe also for this reason Google itself announced in October 2021 that it will activate two-factor authentication as a default setting. Initially, it will be only for the creators enrolled in the Partner Program (hence those who monetize through the YouTube platform), but we expect them to extend this setting also to the other users.
>> Request a quotationor try it now
7. The author
Giorgio Sbaraglia, engineer, is a consultant and trainer on the topics of cyber security and privacy.
He holds training courses on these topics for numerous important Italian companies, including ABIFormazione and the 24Ore Business School.
He is the scientific coordinator of the Master “Cybersecurity and Data Protection” of the 24Ore Business school.
He is a member of the Scientific Committee CLUSIT (Italian Association for Cyber Security) and an Innovation Manager certified by RINA
He has DPO (Data Protection Officer) positions in companies and Professional Associations.
He is the author of the following books:
» “GDPR kit di sopravvivenza” – “GDPR survival kit” (Edited by goWare),
» “Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” – “Cybersecurity survival kit. The web is a dangerous place. We must defend ourselves!” (Edited by goWare),
» “iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” – “iPhone. How to use it to its full potential. Let’s discover together all the functions and best apps” (Edited by goWare).
He collaborates with CYBERSECURITY360 a specialized online magazine of the group Digital360 focusing on Cybersecurity.
He also writes for ICT Security Magazine, for Agenda Digitale and for the magazine CLASS.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.