
The main cyber attacks of the first semester of 2021 targeting companies and organisations
The growth in cyber attacks over recent years
The CLUSIT report by the Italian Association for IT Security has represented over the last decade the most efficient and most complete picture of the current state of cybersecurity in Italy.
The last Clusit report, presented during the month of March, confirmed the growing trend in cyber attacks: it opens with an overview over the most significant cyber crimes that took place in the world in 2020, comparing them to the data collected during the 4 previous years.
2020 was the year of the pandemic and this contributed to the negative record in cyber attacks: at the global level, 1,871 serious attacks of public domain were recorded, with an impact on every realm of society, politics and economics. In percentage, 2020 saw an increase in cyber attacks at the global level by 12% compared to the previous year; over the last four years the growth trend has been almost constant, showing an increase in serious attacks by 66% compared to 2017 and more than twice as many attacks compared to 2014 (from 873 to 1,871 – see picture 1)
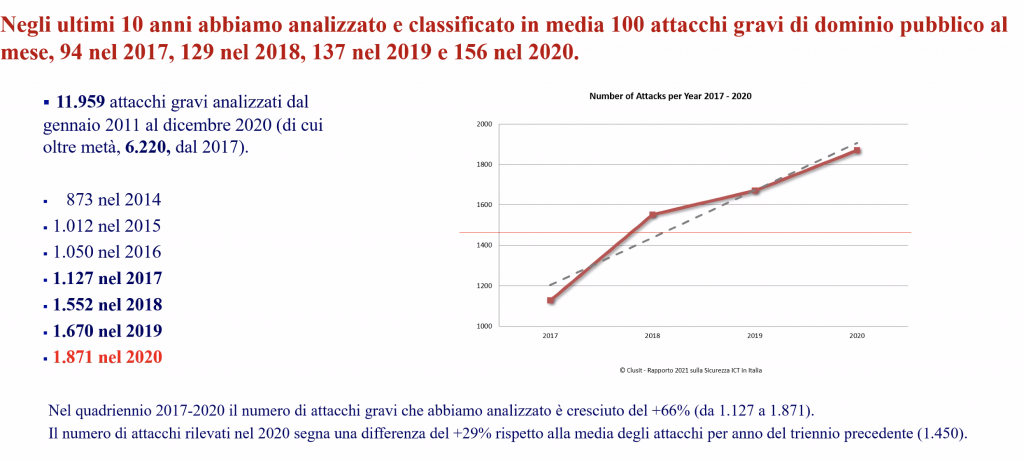
No sector was saved: from the industrial one to public administration, from the healthcare system to services and IT companies. These last ones should be the most equipped and protected ones but – as we will see – they have been especially targeted in supply chain attacks.
Clusit launched an alarm, which was confirmed also by the trend in attacks recorded over the first months of 2021. In the vast majority of cases, there have been Ransomware attacks, which by now represent 67% of all malware attacks (source: Clusit report 2021). We discussed this topic in this article: Read Here.
But in 2021 we also witnessed some unbelievable data leaks, with the online publication of millions of users’ data.
The most serious and sensational case is probably what happened to Facebook, which was shortly afterwards followed by LinkedIn.
The Facebook data breach
The mobile phone numbers and other personal information of about 533 million Facebook users all over the world were shared freely on a popular hacker forum, a forum which is not on the Dark Web – as we might believe – but inside a normal website on the Surface Web, researchable with a normal search engine.
Published data are hence accessible to everyone, exactly those of 533,313,128 Facebook users.
Since it is estimated that in 2021 this social media platform reached a number of over 2,74 billion active users in the world (source: “Digital2021” report by WeAreSocial), the amount of published accounts represents nearly 20% of users all around the world.
In Italy this is even worse: in the “list by country” it occupies the fourth place for the number of users part of the data breach, with 35,677,323 published records, meaning around 90% of all of the Italian facebook accounts.
For each user the following information was made public:
» Mobile phone number
» Name and Surname
» Sex
» City and province of birth
» Birth date (in date + time format, even if not visible on the FB profile)
» Job and relationship status
» email (available only in a few cases)
» Facebook UID (numerical code of the Facebook profile).
» The data do not include the users’ passwords, but this data leak is nevertheless dangerous for users who had their data exposed.
Everyone could use them to engage in targeted phishing activities, what is known as “spear phishing”. Today, over 90% of all of the cyber attacks exploit the human factor and especially the email address as a vector for the attack.
And if the attacker knows a lot of and detailed information about the victim s/he wants to target, s/he will be able to produce a specific attack, credible and much more efficient.
The most exploitable information for an attack therefore is:
» Name and surname
» Sex
» City and province of birth
» Birthdate (format Date + time, even if not visible on the FB profile)
From the combination of this information it will be possible – for example – to recreate the unique fiscal code of a person.
Also, information about “Job and relationship status” can be very useful to outline the victim’s profile and produce a targeted phishing attempt.
The most critical type of information among that published is probably the telephone number, which many users have added on their Facebook profile.
With the telephone number it is possible to carry out a type of fraud known as “SIM swap fraud”, which means cloning the user’s SIM.
This means that a criminal can transfer from one SIM card to another our phone number. Finalising a SIM swapping illegal operation means obtaining complete access to the telephone number of the legal (and unaware) owner of such number. SIM swap frauds are used especially to finalise financial frauds.
If, in order to transfer money, you need double-factor authentication via SMS, the hacker will receive the SMS containing the authentication codes (obviously after obtaining, usually through a phishing attack, the access credentials to the home banking account).
How can we verify if our data are among the 533 millions leaked?
My advice is to use the popular site “Have I Been Pwned”, produced in 2013 by the Australian expert Troy Hunt and on whose credibility there’s no doubt.
In the HIBP homepage you can enter not only your email address (as it used to be before), but also your telephone number in international format, that is in format E.164 (see the picture below).
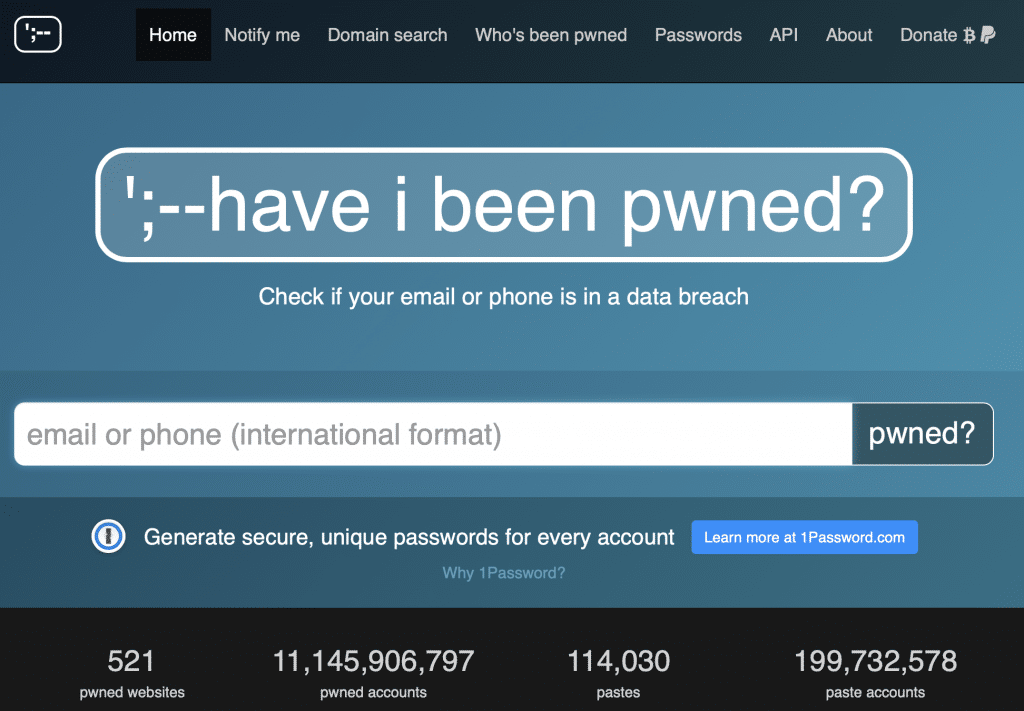
In practice, using as an example the Italian number, this will be inputted as: +39 3xx yyyyyyy (with or without spaces). By clicking on the “pwned?” button, we will discover if our mobile phone number is among the published ones. In this case, we won’t have to change number, but we will need to simply be aware of the risks that we might incur having this information publicly revealed (that is, the SIM swap fraud).
We would like to report also that some users used HIBP and discovered that their number was present, although they had cancelled their Facebook account back in 2015. This raises doubts about how Facebook manages our data…
We received information about the Facebook data breach at the end of March 2021. A few days later, a similar accident happened to LinkedIn: somebody put up for sale on the Dark Web a database with data (email, name, phone number, job positions, skills, etc.) containing the data of more than 500 million users, at a very low price (around USD 1,500). Also in this case the passwords were not available.
The most important attacks of 2021
As mentioned above, also in 2021 ransomware attacks have been by far the most widespread attack technique.
Obviously, only ransomware targeting big companies are reported by the media. But let’s avoid making the mistake – a glaring one – that “only big businesses are hit”!
For one big business victim of ransomware that ends up in the press there are hundreds of SME that are subject to the same attacks and that could go bust. Let’s see which are the main attacks that took place in 2021.
Municipality of Brescia: ransomware attack with a request for USD 1.3 million ransom (March 2021). Shortly afterwards, it was the turn of the municipalities of Rho (MI) and of Caselle Torinese. In all three cases the ransomware was DoppelPaymer.
Boggi Milano: ransomware by the group Ragnarok. In this case the ransomware, before encrypting the data, exfiltered part of them: more than 30GB of data were stolen, divided in several files, which everybody could download. Here is a screenshot from the Ragnarok website.
On April 3 a cyber attack hit the server of Axios, the software company that supplies electronic class registers and other services to 40% of Italian schools. Thousands of schools found it impossible to update the registers and – in some cases – to proceed with online teaching. On the company side, it didn’t lose any data and there was no leak of information.
From 12 to 16 April 2021, company Zambon of Vicenza – one of the Italian top companies in the pharmaceutical sector – had to stop part of its activities because of a ransomware attack.
The attack seems to have begun in a foreign branch of the company in order then to spread to the other branches. The IT protection systems detected the threat straight away, allowing a fast mitigation of the problem. Nevertheless, the plant in Vicenza had to suspend its activities: 217 employees at home for 5 days.
Also financial institutions – despite being better protected – have been targeted: the Bank Credito Cooperativo in Rome suffered an attack. According to what the media published, some laptops in a Roman branch were compromised because of a ransomware attack, probably perpetrated by DarkSide, which we will discuss further below in connection to the much more famous Colonial Pipeline attack.
Also the Washington DC Police was hit by ransomware coming from the Babuk group. This cybercriminal group is relatively recent and uses double extortion as well (it appears that more than 250GB of data were exfiltrated from the police servers and the cybercriminals asked for a ransom in order not to publish the file content. Babuk adopts the more and more popular technique of Ransomware As A Service (RaaS) – meaning a ransom platform for re-sale, where potentially everyone can pay a part of the ransom in order to access the data for his personal aims.
Back to Italy, on Monday morning 11 April 2021 the ATC Turin server (Local Agency for Homes) went haywire because of a ransomware attack with a request for ransom of USD 700 thousand (EUR 584 thousand). The website of ATC was blocked for over a week.
Not even the healthcare sector was saved: on 25 April the Brisbane hospital in Australia was hit by a cyber attack carried out by the REvil group. The attack resulted in the block of the email system of the hospital and of all the reservation system.
On 14 May it was the turn of the Irish Healthcare System. The Conti group, which is very active towards high-profile targets, was responsible for this action. The ransom request in order to free the stolen and encrypted 700GB of data was for USD 20 million.
And finally New Zealand: on 18 May the Waikato District Health Board’s (DHB) was hit. In this case as well the reservation of tests and appointments was blocked.
During the first part of 2021 some “record” ransomware attack were recorded in terms of the amount asked as ransom and of the dimension of the targeted companies.
A lot of these attacks share a common basis: the vulnerabilities discovered on the MicrosoftExchange servers and exploited by numerous criminal groups in order to violate the IT systems of various companies and spread the ransomware.
Microsoft Exchange Server is the software used by companies and organisations all over the world to manage emails and calendars. Compromising the Exchange on-premise servers (cloud versions were not targeted) by exploiting the four vulnerabilities known as “ProxyLogon” allowed access to the attacked systems and inject the malware, especially of the ransomware type.
Microsoft gave this new family of ransomware the name Win32/DoejoCrypt.A (or also the simpler DearCry). It looked like the attack had been launched by the Chinese cyber criminal group known as Hafnium, which exploited the zero-day vulnerabilities of Microsoft Exchange in order to infiltrate the local Exchange servers of victims, accessing the email boxes of companies and stealing their content in order to inject the malware.
According to the Microsoft Threat Intelligence Center (MTIC), the Hafnium group is sponsored by the Chinese state and carries out its operations outside China mainly using Private Virtual Servers (PVS) rented in the United States, where most of its victims are based.
Microsoft rapidly released the safety patches but until the updates were installed, the companies remained vulnerable: it is estimated that, when the patches were released, there were around 400,000 potentially compromised servers because of the ProxyLogon vulnerabilities. Among these, there were also those of the European Banking Authority (EBA), which decided to put its email systems offline as a precaution.
According to the data collected by Palo Alto Networks, the number of Exchange servers all around the world that hasn’t yet received a patch and is therefore still vulnerable decreased, a few days after the patch release, to around 80,000 (14 March).
In the list of countries with the higher number of still vulnerable Exchange servers Italy takes the fifth place with 3,700 after the USA (20,000), Germany (11,000) the UK (4,900) and France (4,000). Unluckily many companies underestimated – as it’s often the case – the importance of running the security updates quickly. This measure is today fundamental in order to protect our systems, because – we will never stress it enough – “an updated system is always safer”.
The companies hit by ransomware through Exchange were many and important ones: one of the most famous is Acer Computer, which was hit by REvil (one of the most aggressive groups), with a ransom request of USD 50 million and the threat to publish the stolen data on the Dark Web.
The hacking happened most likely between 13 and 14 March, during the weekend, a preferred time for attack by all cybercriminals.
The ransom request of USD 50 million represented an absolute record (over 2019 and 2020 the peak was of USD 30 million), but it was shortly afterwards overpassed by the ransom requested to Kaseya.
In July 2021 what is considered by some as the biggest attack in history took place. It started from the infection of Kaseya, a company that supplies network monitoring systems and quickly spread to hundreds of its customers, which in turn are service resellers, with a chain effect at the global level that jeopardized probably millions of PCs. Among the victims there was one of the biggest Swedish food chains, Coop, which had to temporarily close down almost all of its 800 shops.
The Kaseya attack seems to have come from REvil, a ransomware group base in Russia, which asked for a record ransom of USD 70 million dollars (EUR 59 millions) in Bitcoin in order to release publicly what they called a “universal decryptor”.
The action against Kaseya represents a typical case of “supply chain attack”: you violate the systems of a supplier (in this case Kaseya), you inject the malware and then it will spread with a cascade effect to all of the victim’s clients.
REvil, also known as Sodinokibi, boasts a “high level curriculum”: it is deemed to be also responsible for the attack to the giant of meat preparation, JBS.
JBS S.A. is a Brazilian company, the biggest in the world for meat preparation, with plants also in the USA in Greeley (Colorado), which is where the attack most likely started form.
It represents about 20% of the butchering capacity for pork and beef in the USA, so the attack caused a significant disruption to the food supply chain in the US. Luckily, the company managed to fix its production plants quite quickly.
Many of these attacks – as we saw – have hit American companies and are proof of the extreme vulnerability of companies in primary services to ransomware attacks notwithstanding the numerous red flags issued by police forces and security companies. We will now illustrate what could be considered the 2021 ransomware attack that had the most devastating social and economic impacts.
DarkSide and the pipeline attack
In 2021 a ransomware attack – yet one more – had a very heavy impact on the USA, showing how fragile was a critical infrastructure that distributes fuel to almost half of the nation.
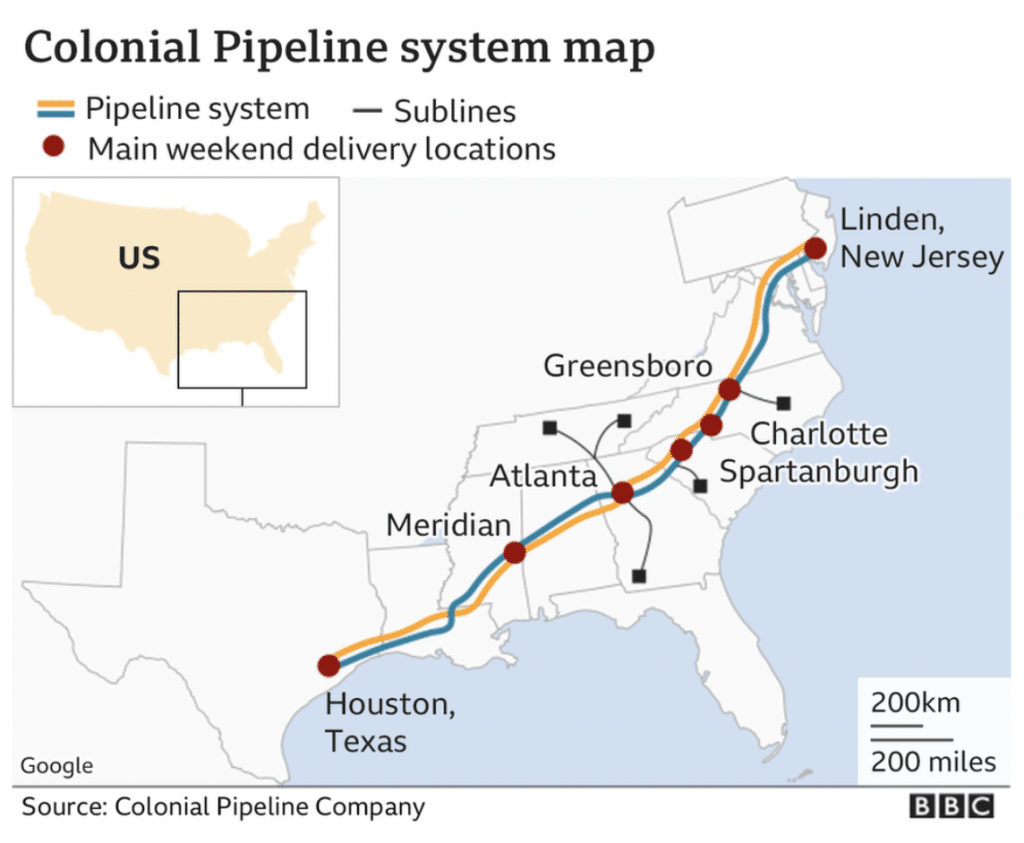
On 7 May 2021 Colonial Pipeline, the operator of the biggest pipeline that transports fuel between Texas and the east coast of the United States (see picture above), was blocked by a double extortion ransomware attack. The pipeline supplies around 45% of fuel in the United States (2.5 million barrels a day) and the provisions of petrol, diesel, domestic heating oil, jet fuel and supplies of military fuels were so heavily hit that the Federal Motor Carrier Safety Administration (FMCSA) on 9 May declared the emergency status in 18 states.
In some cities, including Atlanta, 30% of the gas stations had no fuel left. The block lasted about a week, until the company gave in to the ransom request and paid USD 4.4 million to the cybercriminals of the DarkSide group.
On top of encrypting the files of the Colonial Pipeline IT systems, DarkSide also stole more than 100GB of company data. This data breach represents a double extortion case, a technique that had already been used before by these attackers.
DarkSide was observed for the first time in August 2020. Its origin is either Russian or Ukrainian. It targeted institutions in the Middle East, Europe and, finally, in the United States while it has never targeted Russian companies or institutions.
The group was already known also for the use of the distribution model Ransomware-as-a-Service (RaaS), so it is possible that other different affiliated groups took part in the attacks.
Also the FBI confirmed that the group has Russian origins but is not connected to the Russian secret services. Hence, this was not a state-sponsored attack, but rather a an action aimed at extorting money.
DarkSide has got attack techniques that are similar to those of another famous ransomware group, REvil (known also with the name of Sodinokibi), which we have already discussed.
Once it accessec the target system, this ransomware carries out a range of actions that are typical of ransomware:
» It empties the bins;
» It cancels shadow copies of Windows (to restrain the victim from recovering the pre-attack status);
» It terminates procedures, especially security ones, so as not to have obstacles during the attack;
» It encrypts local discs using a combination of cryptographic algorithms Salsa20 and RSA-1024;
» It encrypts the network shares;
» It exfilters data.
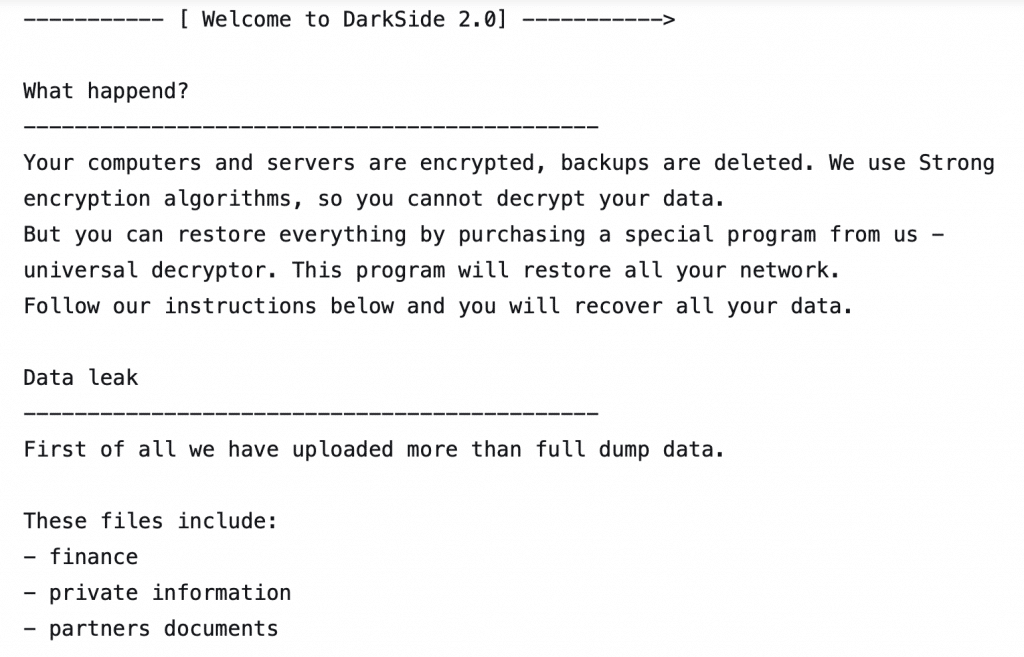
Once all data have been exfiltrated, the attackers publish them on their DarkSide Leaks, together with other information about the attack, like the name of the company, the date when it was attacked, how many data were stolen, sample screenshots of the stolen data and kind of stolen data. On the attacked computers a request for ransom appears with instructions on how to pay (see picture below).
But the impact of the attack was not only economic, it put in a status of crisis the entire economy of the US to the point that the same President Biden intervened with an executive order to strengthen the national IT security.
At this point, the cybercriminals of DarkSide realised that they had exaggerated and – like a “normal” company – they issued a press release of this level, almost to excuse themselves: “We are apolitical, we do not take part in geopolitics, we do not need to connect with a certain government. Our objective is making money and not creating problems to society. Starting from today, we have introduced moderation and we will check every company our partners want to encrypt in order to avoid social consequences in the future”.
And right afterwards, they vanished. It is not clear whether they disappeared willingly or if they were hit by the FBI. Nevertheless, the servers and infrastructures of DarkSide were dismantled and part of ransom paid (about half of it) was recovered. All of the operations of this criminal group were brutally cancelled.
This attack represented a fundamental turning point: the states and politics understood that their actions against cyberthreats were way too weak to contrast the continuously evolving and ever stronger cybercrime. The decision by the American administration to enact strong actions is significant and has set a path that other countries will have to follow, too.
We reached the end of this article, which may continue on indefinitely. Also during these summer months cybercriminals haven’t gone on holiday, to the contrary, they have exploited the reduced level of presence inside companies (like during the weekends) to continue to hit.
We will then report on the most glaring attack that took place in Italy during the first days of August: the servers of the Lazio region were hit by a ransomware attack of the RansomExx group, which seemed to have encrypted also the backup (which was actually later recovered). All of the regional healthcare system and especially the platform for the Covid-19 vaccins, was blocked.
In these early days of September we recorded the attack to Butali, a company that controls part of Euronics, the distribution chain specialised in consumer electronics, with headquarters in Amsterdam.
The ransomware comes from the cyber gang Vice Society, which on its blog in the DarkWeb published part of the stolen data, in several directories containing reserved information of the companies. Among this is sensitive information like lists of usernames and passwords, with a XLS file, which may potentially include access data for branch infrastructures.
Most likely, stolen data refer only to some of the branches of Euronics in Tuscany and Umbria and contain confidential information like stock, invoices, company procedures on top of budget information and data about offer planning and affiliates. Companies Butali and Euronics haven’t commented on what has happened yet, so we do not have any information about the ransom request.
The author
Giorgio Sbaraglia (https://www.giorgiosbaraglia.it), engineer, is a consultant and trainer on the topics of cyber security and privacy.
He holds training courses about these topics for numerous important Italian companies, including the 24Ore Business School (read here).
He is a member of the Scientific Committee CLUSIT (Italian Association for Cyber Security) and an Innovation Manager certified by RINA
He is the scientific coordinator of the Master “Cybersecurity and Data Protection” of the 24Ore Business school.
He has DPO (Data Protection Officer) positions in companies and Professional Associations.
He is the author of the following books:
“GDPR kit di sopravvivenza” – “GDPR survival kit” (Edited by goWare),
“Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” – “Cybersecurity survival kit. The web is a dangerous place. We must defend ourselves!” (Edited by goWare),
“iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” – “iPhone. How to use it to its full potential. Let’s discover together all the functions and best apps” (Edited by goWare).
He collaborates with CYBERSECURITY360 a specialised online magazine of the group Digital360 focusing on Cybersecurity.
He writes also for ICT Security Magazine, Agenda Digitale, and the magazine CLASS.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.
> For more information click here
> For a free trial click here
> To request a quote click here







