
RANSOMWARE: The most recent and most sophisticated attack techniques
What is Ransomware
The word Ransomware is a combination of “Ransom” and “Malware”.
So: a malware that results in a request for ransom.
Technically, they are cryptographic Trojan horses, which have as their only purpose the extortion of money through a “file seizure”, realised using encryption mechanisms that make the files unusable.
In practice, malwares encrypt the files in our computer (or on our servers), making them unreadable.
Afterwards, the payment of a ransom is demanded in order to have the files back.
It is, to all intents and purposes, a seizure of data aimed for extortion.
The spread of Ransomware
Over the recent years, the number of ransomware attacks targeting companies all over the world has increased more and more:
- Garmin (request for a ransom worth 10 million dollars)
- University of California San Francisco (1.14 million dollars paid as ransom)
- Norsk Hydro
- Telecomm Argentina
- United Health Services (USA)
- Barnes & Noble
- Foxconn
- Randstad
- The cities of Atlanta and Baltimore (USA)
- Duesseldorf University Hospital (Germany)
- Canon
- ENEL (Italy)
- Manchester United Football Club
- Accenture.
During the Dusseldorf University Hospital attack of September 2020 a woman even died because of the impossibility to be assisted since the hospital was blocked by the ransomware.
This is the first known case of a casualty directly linked to a cyber attack.
In Italy a lot of cases have been reported as well. We will mention some of them here, but the list could be much longer:
- Campari (2019, request for a ransom of 16 million euros)
- Enel (two attacks in 2019)
- Bonfiglioli (2019)
- Zambon (2020)
- Geox
- Luxottica
- Agenzia Territoriale per la Casa in Turin (2021)
- Municipality of Brescia (2021)
- Up to the most recent and resounding case of the Lazio Region, hit at the beginning of August 2021.
The ransomware phenomenon is hence ever more popular and continues to cause damage.
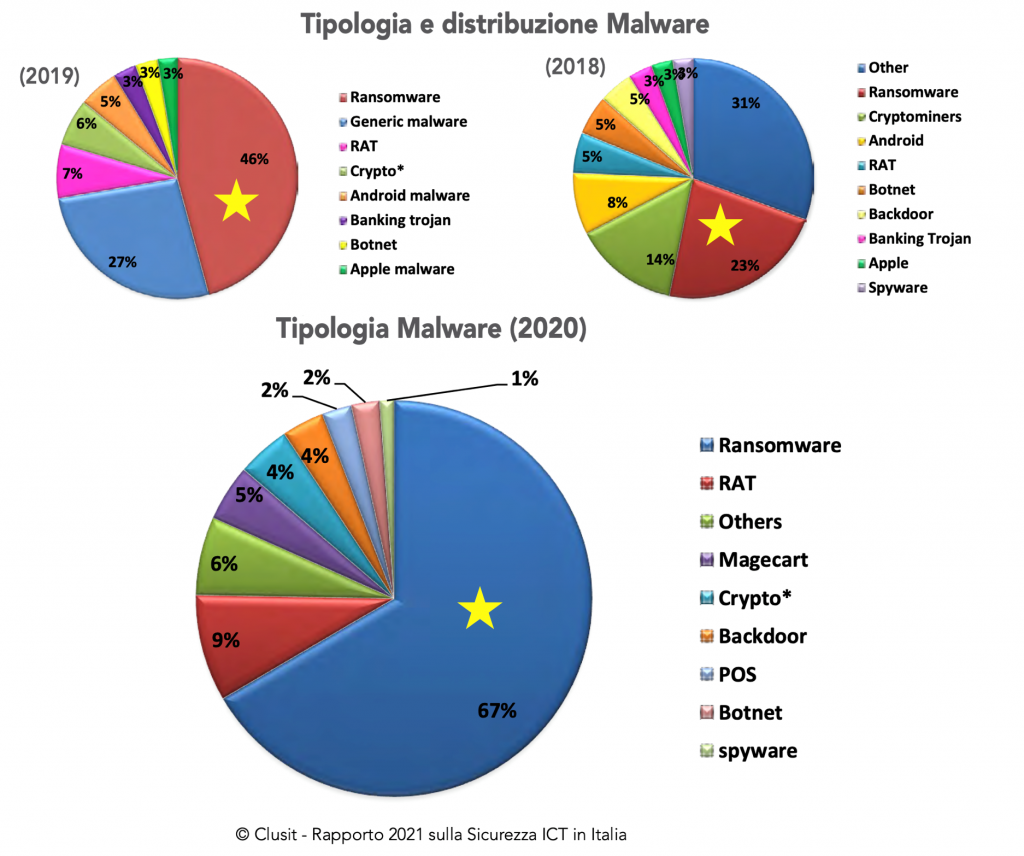
The Clusit Report of 2021 provides some extremely significative evidence. As highlighted in the picture below, Ransomware represented:
» one fourth of all malware in 2018,
» almost half of all malware in 2019,
» growing to 67% of all malware in 2020.
Therefore, today two out of three attacks are ransomware!
According to a study carried out by Check Point Software Technologies, 66% of the surveyed companies declared to have been subject to at least one cyber attack over the last two years (2020-2021).
In 2021 there will be a ransomware attack targeting companies all over the world every 11 seconds.
From floppy discs to Double Extortion
The boom of ransomware started in 2012 and, since then, it hasn’t ever stopped.
But actually, ransomware was born some years before.
It was 1989 when what we consider today as the first ransomware attack in history was launched. The attack was dubbed “PC Cyborg”, because the payments were directed to a ghost company called “PC Cyborg Corporation”. The malware blocked the functioning of the computer using as an excuse the alleged “expiration of the license of a not-better identified software”.
A ransom of 189 dollars was requested to the users who wanted everything to go back to normal.
It was spread during a congress on AIDS using 20,000 infected floppy discs that were delivered to those in attendance: once they inserted the floppy disc, the virus installed itself and encrypted all the files.

Picture 2 – The first ransomware
The spread of this ransomware attack was very limited because back then few people used a personal computer, it was conveyed through a floppy disc (at the time, Internet was a network for few professionals), the technology for encryption was extremely limited and payments were very cumbersome. The perpetrator, Joseph Popp, was discovered and arrested a few weeks later.
Since then, ransomware has evolved enormously, both in spreading and in attack techniques (TTP: tactics, techniques, and procedures).
Today malwares are produced by cybercriminal companies that are well organised and have plenty of resources, with a business model comparable to that of the best “traditional” enterprises.
These companies are capable of doing research and development in order to create ransomwares that are more and more sophisticated and aggressive.
How Ransomware evolved: the most recent attack techniques
Let’s now see how these attacks have changed from 2012 up to today.
Between 2013 and 2017
During the first years (between 2013 and 2017) the attacks were mainly perpetrated using the technique of “trawling”: targets were not chosen specifically and ransoms were usually low, of some hundred dollars. In 80% of the cases the request for ransom did not go over 1,000 dollars.
Today we are witnessing a lower number of opportunistic attacks and a lot more targeted attacks. Cybercriminals prepare the attack using OSINT activities, and the hackers inspect the network of the victim in order to render the protection inactive and highlight points of entry.
As a consequence, the amounts asked as ransom have increased a lot. The average paid ransom went from 115,123 dollars in 2019 to 312,493 dollars in 2020 (+171% in one year).
From 2015 to 2019
From 2015 to 2019 the highest request was for 15 million dollars, while in 2020 it reached 30 million dollars. (Source: “Unit 42 Ransomware Threat Report 2021” di Palo Alto Networks).
2021
In 2021 the record amount of 50 million dollars was asked to company ACER Computer, one of the main producers of computers in the world. Soon after came a request for 70 million dollars to Kaseya (this will be discussed further below).
Another technique detected recently has been that of making people restart infected computers in Windows Safe Mode: in this way, the security functions (antivirus, etc.) are not uploaded and the system becomes more vulnerable.
Alternatively, the ransomware can be spread using a virtual machine (VM) as a means to elude detection.
This innovative technique has been observed for the first time in RagnarLocker and allows the ransomware to spread as a VM on almost all the devices it infects.
Double Extortion
But the main innovation in the market for ransomware has definitely been “Double Extortion”: a practice that has dramatically complicated the life of targeted companies.
The pioneer of Double Extortion was Maze in 2019 and afterwards this technique was used also by other ransomware like:
» NetWalker (one of the most active)
» RagnarLocker
» DoppelPaymer
» Sodinokibi (alias REvil), etc.
Today, in 2021, it has almost become the rule rather than the exception.
Over the years, cybercriminals have understood that more and more frequently victims had created a backup and were therefore not going to pay the ransom.
Double extortion is a particularly subtle technique aimed at making the victim pay for ransom even though s/he has a valid backup. The threat used is that of exposing data – that have been previously exfiltrated before encryption – on a public website or on the dark web. The risk is that of a deep impact on the targeted company, which will have to report a data breach, with all the implications also in terms of GDPR.
Cybercriminals sometimes even warn their victims – when they present their requests for ransom – that the payment of ransom would be the smallest damage, because the threat of publishing data would cause even heavier sanctions from the privacy guarantors.
In practice, these criminals have been able to exploit a “commercial” opportunity after the GDPR policy appeared!
The first known case of double extortion dates back to 2019 and is the work of Maze: it hit Allied Universal, a big American security company. When the victims refused to pay a ransom of 300 Bitcoins (around 2.3 million dollars), the attackers threatened them to use confidential information exfiltrated from the systems of Allied Universal.
In order to demonstrate their thesis, the cybercriminals of Maze published a sample of the stolen files, among which were contracts, medical records, encryption certificates and much more. In a later post on a Russian forum about hacking, the attackers inserted a link to what they deemed to be 10% of the stolen information and a new request for ransom, 50% higher.
In 2020, the requests for ransom by Maze were on average of 4.8 million dollars, a significant increase compared to the average ransom request of 847,344 dollars for all ransomware types in 2020. Direct communication with the operators took place through a Tor website.
In November 2020 the actors behind Maze announced their retirement from the ransomware scene. They did it with a press release, like a “real” company.
However, most likely the group simply split into smaller units, including Egregor ransomware, which started emerging shortly before this announcement. These actions follow a similar model to that of the GandCrab ransomware group, which announced its retirement in May 2019, and then came back under the name REvil (the Russian group responsible for the 2021 attack on Kaseya, as we will see below).
Recently, there have been important cases of ransomware with double extortion also in Italy. The following companies were hit
- Enel (about 5 TeraBytes of data relating to power plants published on the darkweb in 2019)
- Campari
- Telecom
- and others.
In August 2021, the consulting company Accenture was also hit by a ransomware attack: in this case as well it seems that confidential data were published (but it has not been confirmed).
The vectors of infection
The ways in which a ransomware attack can penetrate into our laptops are essentially the same as many other types of attacks and are largely unchanged: the same have been used again and again over time, because they still function well! They have obviously become more refined and, on top of the classic ones, other more innovative ones have been added, as we will see.
- The most common method, because unluckily it still causes victims, is phishing emails: with this technique, which exploits social engineering, over 50% of ransomware is spread. We discussed this more in detail in this article: https://flashstart.com/phishing-and-spear-phishing-attack-techniques/
- Navigating on compromised websites: the so-called “drive-by download”, meaning unaware download, known also as “watering hole”. In this second case, the scenery changes because it is the victim who accesses the infected website with no need for the attacker to push her with an email.
They can be fake sites, created exactly to imitate the most popular websites, but also real websites that have been violated. In both cases, malicious agents such as JavaScript, HTML or exploit kits are injected into the website, exploiting the vulnerabilities of browsers, of Adobe Flash Player, Java and others.
They appear, for example, like advertising banners or buttons that invite us to click on them. After that, we will be connected to a page where the download of the malware takes place.
In these two attack modes (phishing and drive-by download), the protection systems supplied by FlashStart can help us: the FlashStart defence tools can recognise a suspect link to which the violated machine is trying to connect and block the connection…so that the attack will be nipped in the bud. - Using a detachable device, such as a USB key infected with the malicious software. This technique is known as “Baiting” and – as with phishing emails – it exploits the human factor and particularly the curiosity of people. What happens is that an infected memory device, like a USB key, is left in a common place (for example the entrance to a company, a canteen or a parking lot). The device will become active as soon as it gets connected to a computer. Thanks to human curiosity, this bait will most likely succeed.
- Inside (in bundle with) other softwares that are downloaded: for example free programmes that promise to “crack” expensive softwares (often also videogames) in order to use them without paying. Today, this practice has become very dangerous, because the crack we download will be executable (.exe) and the malware will most probably be inside it. Lately, we have often detected this technique: since the first months of 2021 ransomware campaigns that use cracked versions (hence free!) of well-known pay-for programmes, especially Microsoft Office and Adobe Photoshop CC, have been reported.
- Attacks through remote desktops (RDP: remote desktop protocol): these are attacks aimed at stealing credentials (to access servers through the RDP and take control over them). Computers and servers with an active RDP and that are exposed in the web are victim of targeted attacks aimed at obtaining access credentials (usually with “brute force” attacks). Once they have obtained the data needed to access the system, cybercriminals can start a plethora of actions, such as: theft of credentials and data and, indeed, the injection of ransomware. This attack mode has recorded an increase by 197% in 2021 compared to the previous year, especially because of smart working.
- We have therefore seen ransomware attacks perpetrated by exploiting vulnerabilities. Extremely relevant (for the amount of targeted companies) is the attack of March 2021 that used a vulnerability in the Microsoft Exchange Server (the software used by companies and organizations all around the world to manage emails and calendars) to spread ransomware after compromising the servers. Microsoft assigned to this new family the name Win32/DoejoCrypt.A. (or, more simply, DearCry). The attack was likely launched by the group of Chinese cybercriminals named Hafnium and exploited the zero-day vulnerabilities of Microsoft Exchange to infiltrate Server Exchange and its local victims and get access to the email folders of the companies in order to abduct the content and inject the malware. Previously, we remember the famous WannaCry of May 2017, which exploited a vulnerability in the Windows Server Message Block protocol, version 1.0 (SMBv1).
- And finally – last but not least – ransomware can be spread with a Supply Chain Attack: a supplier is used as a means to hit its client companies. At the end of 2020 this happened with Solar Winds: the attackers (deemed to be Russian hackers) violated the company servers by injecting an infected update. The update was then downloaded by about 18,000 client companies, which were obviously hit by the malware.
In July 2021 the attack deemed to be the biggest in the history of ransomware took place. It started from the infection of Kaseya, a company that supplies webnet monitoring systems, and quickly spread to hundreds of its customers, who – in turn – are resellers of services towards other clients. The attack therefore had a chain effect at the international level, putting at risk millions of laptops. Among the victims there was one of the biggest Swedish food chains, Coop, which had to temporarily stop almost all of its 800 shops.
The attack on Kesaya seemed to come from the REvil group, a ransomware band based in Russia, which asked for 70 million dollars (59 million euros) in Bitcoin in order to release publicly what they called a “universal decryptor”.
The author
Giorgio Sbaraglia (https://www.giorgiosbaraglia.it), engineer, is a consultant and trainer on the topics of cyber security and privacy.
He holds training courses about these topics for numerous important Italian companies, including the 24Ore Business School (read here).
He is the scientific coordinator of the Master “Cybersecurity and Data Protection” of the 24Ore Business school.
He is a member of the Scientific Committee CLUSIT (Italian Association for Cyber Security) and an Innovation Manager certified by RINA
He has DPO (Data Protection Officer) positions in companies and Professional Associations.
He is the author of the following books:
“GDPR kit di sopravvivenza” – “GDPR survival kit” (Edited by goWare),
“Cybersecurity kit di sopravvivenza. Il web è un luogo pericoloso. Dobbiamo difenderci!” – “Cybersecurity survival kit. The web is a dangerous place. We must defend ourselves!” (Edited by goWare),
“iPhone. Come usarlo al meglio. Scopriamo insieme tutte le funzioni e le app migliori” – “iPhone. How to use it to its full potential. Let’s discover together all the functions and best apps” (Edited by goWare).
He collaborates with CYBERSECURITY360 a specialised online magazine of the group Digital360 focusing on Cybersecurity.
He writes also for ICT Security Magazine, Agenda Digitale, and the magazine CLASS.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







