
Malware on mobile devices
Mobile malware: a little history
Today, your smartphone has become “the remote control of your life”, a device you use more than the laptop itself, where you save your most important data.
Therefore, our smartphones are mines of precious information for cybercriminals, who attack them with techniques that are more and more sophisticated and new, especially since 2016, when Internet traffic from mobile phones exceeded – for the first time – traffic from computers.
In 2021, traffic from mobile devices represents 55.7% of all the world web traffic (see picture 1 below).
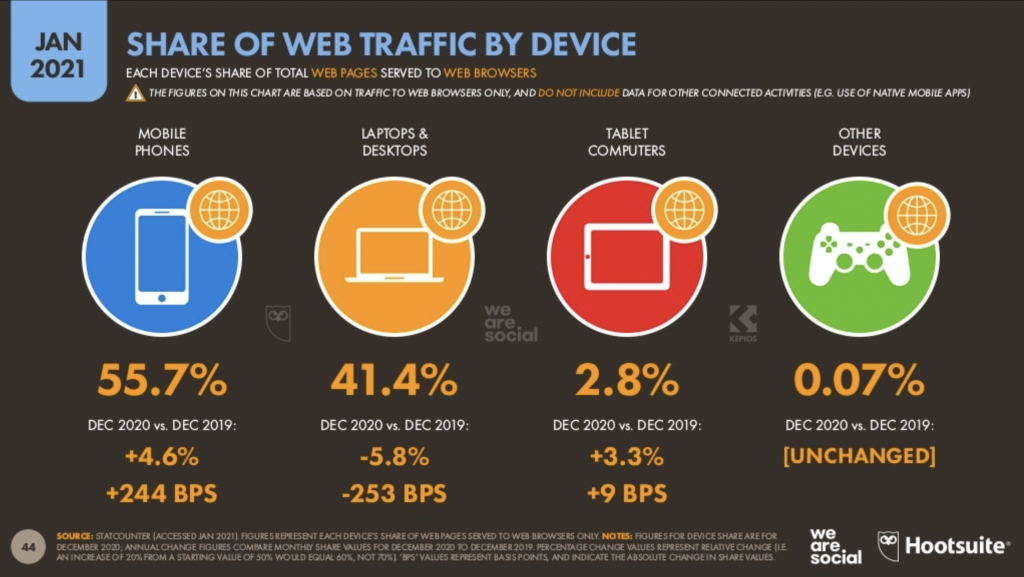
Picture 1 – Distribution of web traffic by device in the world (source: We Are Social)
Malwares on mobile phones are relatively recent. The first case of mobile malware dates back to 2004: it was called Cabir and hit systems of the type Symbian Series 60 (it spread through bluetooth), then came Ilkee and Duh (2009, they hit iPhones using jailbreak), FakePlayer (2010, the first Android malware that managed to steal money by sending pay-for messages to Russia).
2011 was the year of DroiDream, the first massive attack that hit Google Play using applications that contained malware. We will see below how the use of “infected” apps is one of the main vectors to spread malware to mobile devices (picture 2).
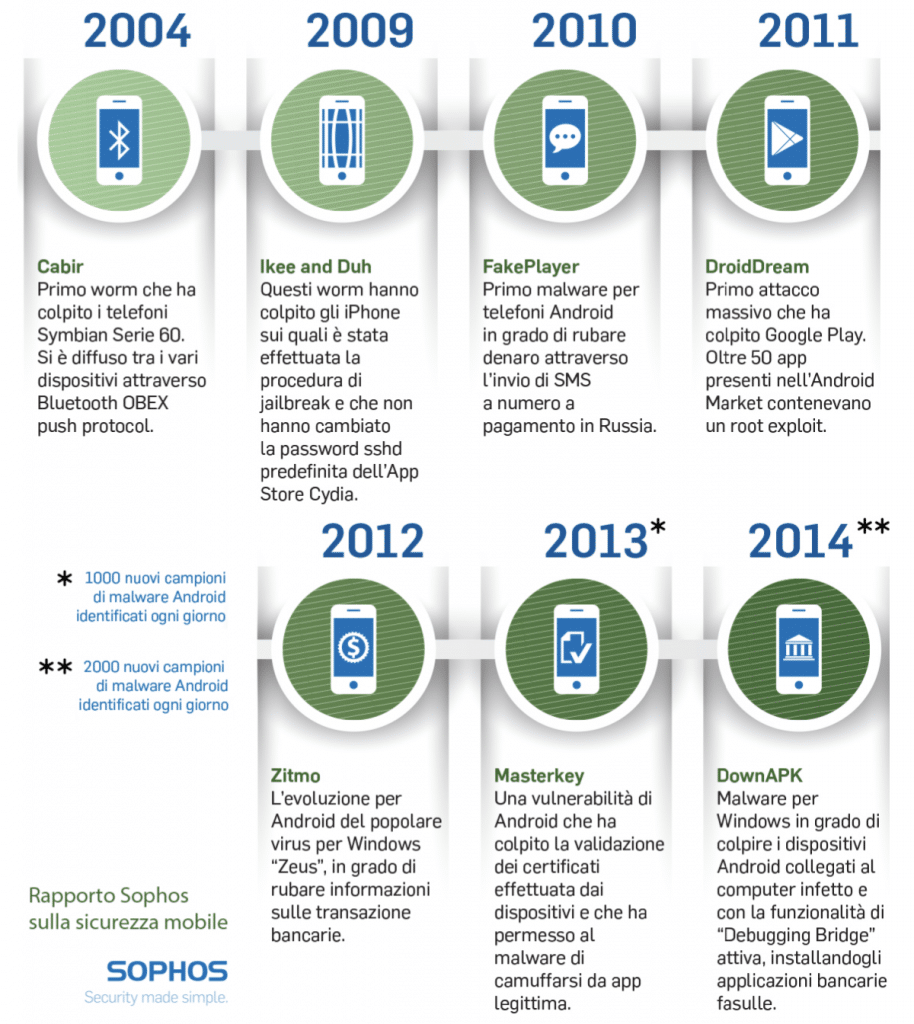
Picture 2 – The first cases of malware on mobile devices (source: Sophos Report on mobile security)
The threat has increased over the recent years mirroring the exponential growth in the spread of smartphones, especially of Android device, which today represent about 85% of the mobile world, while Apple iOS has the remaining 15% of the market.
This explains why Android devices are generally the ones most frequently attacked by malware. This situation is a bit less real in the case of high-level spyware (among which the most popular is Pegasus by the NSO Group), because in this case iPhones represent a particularly aimed-for target. We will discuss this later.
The main threats to mobile devices
Smartphones’ operating systems have an architecture that is different from that of computers (especially Windows) and hence also the attack techniques are different. Both Android and iOS are relatively “closed” operating systems, where applications work without having complete access to the operative system.
It is usually said that in smartphones applications are “sandboxed”, meaning they are segregated in a sandbox and have access only to that part of the operating system to which we grant them permission to access.
Today, the most used way by malwares to infiltrate a mobile device is by downloading a malicious app. Hackers indeed realize applications that include hidden malicious functionalities since try to elude the control processes of the stores from which the apps are downloaded by the users.
Ransomware, which encrypt files and that are causing a lot of damage by attacking the IT systems of companies, haven’t had much success on mobile devices (more on ransomware is available in this article).
This is the case because smartphones have their backup in cloud (iCloud for iPhone and Google Drive for Android). Therefore, if users backup their data regularly, there will be no need to pay a ransom to have their files back, it will be sufficient to recover them through the backup.
This is why cybercriminals don’t find this type of attack convenient.
“Lockscreen ransomwares” are also available for smartphones. They target Android devices. These ransomwares are installed pretending to be a legitimate app (often an antivirus app) and block the smartphone making it impossible to use. Then they ask for a ransom (usually quite low, less than 100 dollars), but they don’t encrypt data (picture 3).
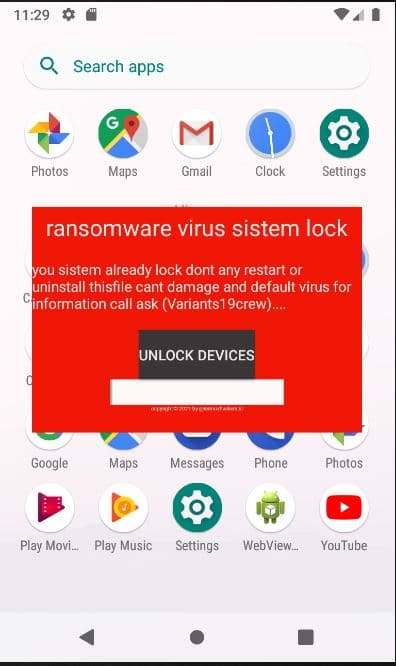
Picture 3 – The screenshot of a lockscreen ransomware
The threat is limited to Android devices, has existed for many years, but nevertheless has a limited spread.
To sum up, we can indicate the following as the main threats to mobile devices:
» Malicious apps
» Vulnerabilities in the operating systems
» Spyware.
Malware through malicious apps
As mentioned above, malware can enter into mobile devices through the installation of a malicious app.
This is a very widespread technique: the attacker realizes an application that contains a malware but that appears like a harmless app. The user downloads it, unaware of what it contains.
Actually, for apps to appear on the official stores (Google Play Store and Apple App Store) they have to be checked by the two companies, which should block the access to apps containing malware.
However, there are frequent cases where this control hasn’t worked: in the following picture we show a recent case.
The security company Quick Heal Technologies Ltd. last June discovered eight malicious apps on Google Play Store, regularly admitted to the store, which used the Joker spyware but appeared as massaging apps or other sorts of apps.
This case is especially subtle, because Joker is not inside the app when it gets downloaded from Play Store but it is downloaded only after the app has been installed on the device
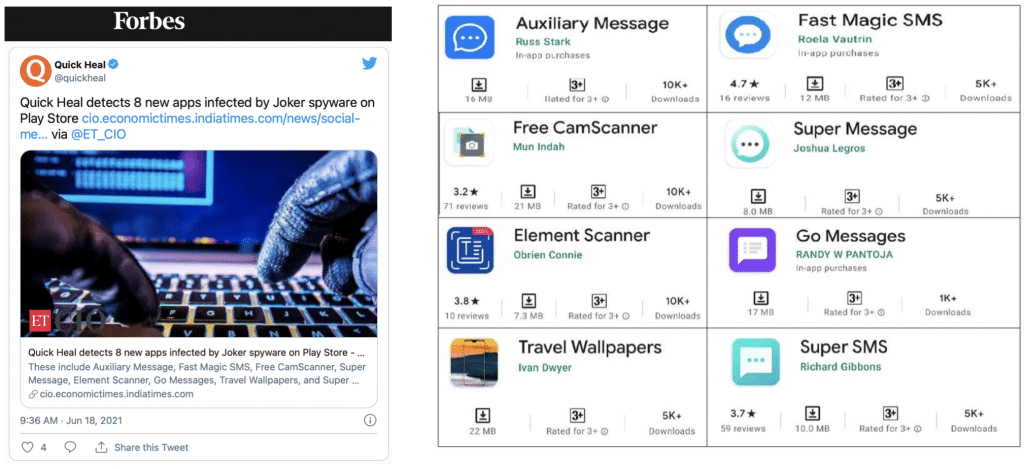
Picture 4 – The Joker spyware and the apps conveyed it
This dissimulation technique might have deceived the Play Store checks.
There are however a lot of other cases where hundreds of malicious apps have been able to be admitted to the stores.
In September 2019 Lukas Stefanko (of ESET) discovered 172 malicious apps on Google Play Store. Naturally, this was reported to the Google Play Store, which immediately removed the apps, but they had already been downloaded 335.952.400 times!
Google is aware of these vulnerabilities of its store, especially when compared to the Apple one, which manages to grant a more stringent control (Apple has declared that about 40% of the apps that are suggested by the developers don’t get admitted to the Apple Store).
This is why Google has formed a partnership with ESER, Lookout and Zimperium to fight the apps that are damaging for its mobile market. The partnership, born at the end of 2019, is called “App Defense Alliance” and has the aim of controlling with a higher level of detail what is published on Play Store, which today counts 2.8 billion users and a market share of around 80% at the world level.
The companies chosen for the partnership are well-known names in the sector of cybersecurity and offer specific products to protect the mobile devices and all the mobile ecosystem. Google hence integrates the “detection engines” of each partner in Google Play Protect, which is the system to detect malicious code inside the apps.
According to what Google declared, Play Protect executes a security check on apps in the Google Play store before their download and verifies the presence of potentially damaging apps coming from other sources on the Android device.
If official stores have shown they cannot grant full security, the situation is even worse on alternative stores, which are widely available for Android apps.
Compared to iOS, that permits to install applications only through the official App Store (unless you execute jailbreak on iPhone, which however is absolutely discouraged for security reasons), on Android there are several alternatives to the Google Play Store.
Many smartphones’ producers (like Samsung) have their own store where users can download apps, but there are also online stores managed by third parties that offer a great deal of free apps and are hence appreciated by those users who pay more attention to cost than security.
And indeed it is in these environments that ill-intentioned hackers are present: publishing malicious apps on these sites is much easier, since controls are minimum – if not totally absent – compared to Google Play Store and Apple AppStore.
We will list hereafter some of these unofficial Android stores and we invite the reader to refrain from using them so as not to have bad surprises: Aptoide, Mobogenie, APKPure, F-Droid, APKMirror and many others.
From these store it is possible to download .apk files, that is the Android Package file for the application. In order to do that, the user must change the settings of his smartphone, deactivating the protection that in most versions of Android blocks the installation of .apk files – which is usually set by default.
It is also possible to block the installation of .apk files downloaded from the Internet and that do not belong to any store following a procedure that varies depending on the device on which you operate, but that is always possible and not particularly complicated.
The risks of Sideloading
The possibility to download and install an app from a third, unofficial source is defined as Sideloading. As we saw, this is possible with Android but not with Apple iOS for iPhone and iPad, since iOS is a closed system.
This choice by Apple is criticized by many, because it is perceived as a way for Apple to consolidate its dominant position and limit free competition in the very rich market for applications.
Also the European Union, through its Competition Commissioner Margrethe Vestager, is evaluating whether this practice by Apple represents an abuse of dominant position. In October 2021 Apple replied decidedly, publishing a very thorough and detailed report that illustrates the threats stemming from a possible opening of iOS to sideloading, if obliged by some antitrust regulations or by some specific EU laws.
The report is titled “Building a Trusted Ecosystem for Millions of Apps” and shows some significant data.
Apple highlights how on Android alone there are 6 million new cases of infections due to malware each month only in Europe. According to other mentioned studies, the quality of malware for Android is superior compared to that of malware for iPhone by a number between 15 and 47 times. It is legitimate to think that Apple supplies useful data to support its stance, but what it claimed is based on solid grounds.
Indeed, also according to another study by PurpleSec titled “2021 Cyber Security Statistics: The Ultimate List of Stats, Data & Trends”, 98% of the attacks that targeted mobile devices in 2021 hit Android devices and in almost all cases they were attacks linked to applications that were installed outside Play Store.
The importance of updates
Non-updated devices are more vulnerable. This postulate is always true, both for computers and smartphones. Keeping your smartphone updated means having a device which is safer and better protected.
Every update can add functionalities, but it will surely also – and mostly – close some vulnerabilities in our devices. Refraining from updating then means keeping the vulnerabilities within the device.
In the iOS system, the chain of update is a very short and vertical one: users receive the updates directly from Apple, with just one step.
Unluckily, this is not possible with Android, because of the complexity of the supply chain, which usually requires at least three steps: from Google, to the chip producers, (Qualcomm, MediaTek, Exynos, etc. which have to updated the code areas relative to their hardware) and then to the smartphone producers (Samsung, Xiaomi, etc., which must integrate the new software supplied by Google with their own interface and add the new functionalities), to then reach – maybe! – the user’s smartphone.
Sometimes a fourth step is added, when the carrier (Tim, Vodafone, etc.) intervenes as well in the personalization of the Android version (picture 5).
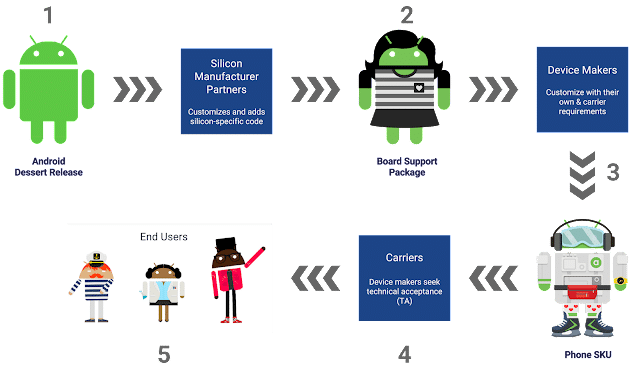
Picture 5 – The update chain for Android (source: Google)
There exists also the chance that the user won’t ever receive the update: this can happen if the device is at least 2 or 3 years old. In this case, the smartphone’s producer could deem it inconvenient to invest time and money to tailor the update to that model, especially if we are talking about a low-priced model.
Google has understood that this cumbersome process represents a competitive disadvantage compared to Apple. Therefore, in 2017 it started “Project Treble”, which was explained in its blog for Android developers.
The project started with the release of Android 8.0 Oreo in 2017.
What Treble does is “subdividing” in sealed sections the code of the operating system, separating the low-level elements – the areas of the code relative to the phone processor, the modem and so on – from the rest of the operating system. In this way, these elements of inferior level must not be updated every time a new version of Android is released.
So, every time Google releases a new version of Android, the device producers will be able to focus exclusively on their part of the operating system, the “superior” part, letting Google/Android update the “inferior” part, that is the one needed for security.
If you wish to have an Android device that maintains for several years the chance to be updated, there exists also another option I advice: choosing a smartphone equipped with Android One.
Android One is the “stock” version of the Google operating system, meaning the one lacking software personalization and the one available on the Pixel smartphones produced by Google, but not only that.
Other companies as well have indeed decided to install it on their smartphones. The list of smartphone with Android One can be found on this website
The interface of this operating system is especially light, since it lacks the tailoring options available with other producers.
But most importantly, the update chain is much faster and long-lasting: when Google releases the Android update, we will reach this immediately and without having to go through the chip and smartphone producers.
To sum it up, the update chain will be similar to that of iOS, with the further advantage of being able to grant updates for a longer period of time (usually at least 3 years).
Spyware
Spyware are applications that get installed (we will see later how) on smartphones and spy on them.
They represent a threat that today is very real for the smartphones. Our devices contain a lot of information and accompany us in each moment of our life; therefore, for cybercriminal (but not only them!) it can be very useful to spy on them rather then stealing them.
These softwares are employed also by the judiciary and by police force for espionage purposes: we talk in this case about “information receivers”, used in order to investigate by wiretapping in on communications or conversations on portable electronic devices.
These tools, even though they are useful for investigative purposes, risk resulting in unacceptable violations of civilians’ liberties when used without the necessary guarantees. Even a scenario of “mass surveillance” can become reality and, consequently, illicit espionage practices.
Indeed, spyware are largely used also for illegal aims, to spy on journalists, dissidents and political rivals.
A lot of different types exist: some are particularly sophisticated and expensive, like the famous Pegasus, realized by the Israeli company NSO Group. Recently (in July 2021) the Ngo Forbidden Stories and Amnesty International have revealed that Pegasus has been used by police forces in some countries (Saudi Arabia, Azerbaijan, Bahrain, United Arab Emirates, India, Kazakhstan, Morocco, Mexico, Rwanda, Togo and Hungary) to spy on important people, journalists and also relevant political figures. The victims are suspected to include also the French president Emmanuel Macron, the ex prime minister Édouard Philippe and 14 ministers of the French government.
Probably also because of these events, in the month of November 2021 the Department of Commerce of the USA has added the Israeli companies NSO Group and Candiru, producers of spyware, to its entity list: this means that exports by American entities to these companies are now subject to restrictions. For the American Department, indeed, these companies act “against the interests of national security and foreign policy of the United States”.
But Pegasus is not the only spyware software, which due to its very high cost (hundreds of thousands of dollars) is likely to be used only for important and specific targets. On the web you can find several applications that do the same thing but in a more “artisanal” way and with costs accessible for all (some hundreds euros).
You don’t need to look for them on the Darkweb, since they are distributed as “legal” applications (or at least they’d like you to believe it is so).
Many of these apps are sold with the official and declared aim of “controlling the smartphone of your children”. Actually, they are programs whose installation in the device of a third party (without their consent) represents a proper crime.
We will list some of them hereafter (without providing the links), which everybody could purchase and use to spy on somebody else (wife, husband, colleague, etc.):
» FlexiSPY
» Highster Mobile
» Hoverwatch
» Mobistealth
» mSpy
» TeenSafe
» TheTruthSpy
» Cerberus
» e molti altri…
Citizen Lab has recently published a thorough report titled “The Predator in Your Pocket”, which analyzes these spywares in a detailed way.
How does a spyware get inside your smartphone
The techniques used to install a spyware are the following, listed by complexity from the most simple ones, accessible by everybody, to the most refined ones:
» by directly accessing the device: this is the most simple technique and the one used by the cheapest spywares (like FleiSPY or mSpy);
» remotely: using a Trojan, with techniques that exploit phishing and social engineering: this is what happened in 2019 to the Judge Palamara, spied thanks to the spyware injected in his iPhone through a warrant of the Judiciary of Perugia;
» through an injection with IMSI Catcher (Stingray, etc.): it’s a “man-in-the-middle” type attack (MitM) and requires the use of dedicated devices, like IMSI Catchers that can connet to the smartphone and take control over it through the mobile network;
» exploiting a vulnerability in the operating system or in an application: in this case 0-Day vulnerabilities are often exploited. In the case of Pegasus, NSO even exploited “zero-click vulnerabilities”, the most powerful ones, since they don’t need any interaction from the user (so no click at all) to infect the smartphone. This is the most sophisticated technique (and the most costly) and it is exactly the one used by Pegasus, which recently started to exploit the vulnerabilities in the iMessage software by Apple, and was hence able to access hundreds of millions of iPhones.
Spyware symptoms: how to understand if you’re being spied upon
It is not easy to understand if a smartphone has been infected by a spyware.
For the most sophisticated products (like those realized by the NSO Group), even resetting your phone to the production conditions could not be enough, since they are designed to be invisible on the victim’s smartphone and – in the most advanced cases – to set into the Bootloader (the software that, when turning on the phone, is in charge of uploading the installed operating system).
The less advanced ones (listed above), even though they manage to be invisible, can generally be eliminated by resetting the phone. In other cases – if you suspect being the victim of spyware – you may need to have your device analyzed by specialized companies, but in this case costs are comparable to those of purchasing a new smartphone…
Anyway, the existence of a spyware can be at least suspected when the following symptoms are present:
» lower lasting of the battery: spywares are always active and consume battery even if we are not using the phone;
» abnormal increase in data traffic: spywares have to send out the collected data;
» consequent unmotivated increase in costs;
» slowed performance and, more in general, an abnormal phone functioning.
Good safety rules in the use of mobile devices
As mentioned above, spywares are always used against specific targets: a political rival, but also a competitor, colleague or – very often – your partner.
Here are some best practices to safely use our smartphones and to defend ourselves from spywares.
As usual, these measures are mainly about the human factor (which is by far the weak point in the security chain):
» install apps downloaded only from reliable sources, like Google Play Store and Apple App Store. Avoid, as explained above, apps coming from questionable sources;
» don’t click on links or attachments in emails and messages;
» keep your operating system updated;
» protect your devices with a strong password. Setting a safe password (the advice is to have a password longer than 4 digits, of at least 6 digits and that includes both numbers and letters) has become necessary to avoid that someone accesses your phone, spies on it and especially installs a malicious app on it. Unluckily, a lot of people still today do not set an unlock password – because of laziness and lack of attention – although the use of biometric systems (TouchID, FaceID) makes this option extremely comfortable: the unlock password will have to be inputted only rarely, for example when turning on the smartphone.
In our smartphone now there is our life, we shall not underestimate their security!
The author:
Giorgio Sbaraglia, engineer, is a consultant and trainer on the topics of cyber security and privacy.
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.
> For more information click here
> For a free trial click here
> To request a quote click here







