How to block DNS traffic with MikroTik?
1. Introduction
Network security is a growing concern for businesses and individuals, especially with the increase in malicious DNS traffic. Attacks via DNS traffic can have serious consequences, including the spread of malware, data theft, and service interruptions. This is why protecting DNS traffic has become a key part of every online security strategy.
MikroTik’s high-capacity routers are equipped with RouterOS as a routing, firewall, or QOS operating system. RouterOS offers a wide range of security tools to protect the network. In this article we will explore how to block unwanted or malicious DNS traffic with MikroTik.
Various techniques and strategies will be explained, from setting up a firewall to using address lists to block specific web sites. We will also discuss the importance of adding a DNS system such as FlashStart to our protection.
2. Configuring a MikroTik router in order to block unwanted or malicious DNS traffic
Configuring a MikroTik router in order to block unwanted or malicious DNS traffic is an important step in protecting the network from potential cyber threats and attacks. Firewalls are an effective way to protect the network, as they can monitor and filter incoming and outgoing traffic according to certain rules and security policies. However, it is not the only option; in this post we will explore some alternatives.
RouterOS is equipped with a DNS proxy for web browsing resolution and caching. Filtering different content on a MikroTik router can be done using the DNS function or by directly applying firewall rules on the router. Rules can be configured based upon different factors, such as IP addresses, ports, protocols, or network interfaces. It is also possible to define rules based upon groups of IP addresses or lists of domains known to be malicious.
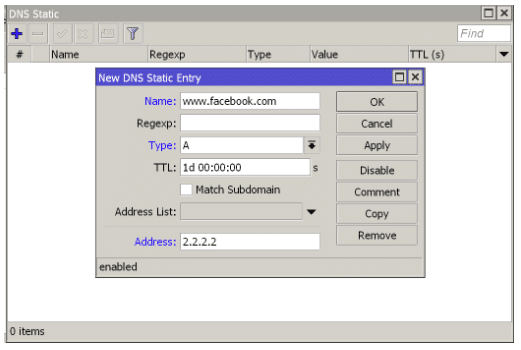
In order to apply a filter to a particular domain, it is possible to use the Static option within DNS and assign an A record to an internal or nonexistent IP, so that a user searching for that domain would not be able to access it.
Keep in mind that, in order to perform this action, the user’s DNS must be our router. There are many techniques within the configuration to ensure that the user always uses our DNS, such as the Redirect action, within the firewall.
In the following example, we see how to assign IP 2.2.2.2.2 to the domain Facebook.com; a user will not be able to navigate to Facebook if this entry is of a static type. We can also use an internal IP address with a web that reads “Access Prohibited”; these options always depend upon the policies and the administrator.
It is important to keep in mind that a firewall is not a one-size-fits-all solution to protect the network from attacks. Therefore, it is advisable to implement additional security measures, such as rules to protect the network and routers which are exposed to the internet. This is one of the ways offered by MikroTik for blocking DNS traffic.
>> FlashStart is totally in cloud based and is easy to activate → Activate now your “Free trial”, our company is active 24/7
3. Using domain lists or IP addresses to identify and block specific websites or groups of websites
MikroTik is very flexible when it comes to domain settings; there are several ways to filter contents:
» Using the Firewall with the contents option.
» Applying TLS-Host type rules.
» Using the address list with domains.
We will analyze these three options below:
3.1 Using the Firewall with the “content” option.
The “content” option of the MikroTik firewall is a tool that allows one to filter network traffic based on its content. This option allows the user to specify keywords or text patterns that the firewall will look for in incoming and outgoing network traffic. If a match is found, the action defined in the corresponding firewall rule will be applied.
For example, a MikroTik firewall rule can be configured to search for all network packets containing the word “video.” If a packet containing this word is found, the rule can block the packet or redirect it to another server.
The “content” option can also be useful for blocking specific websites or inappropriate contents. It is possible to set a rule in the firewall that looks for a specific URL or keyword in the website content and block it if it is found. Remember that the vast majority of traffic is encrypted, using HTTPS; if this rule is not effective for this traffic, there are other options available.
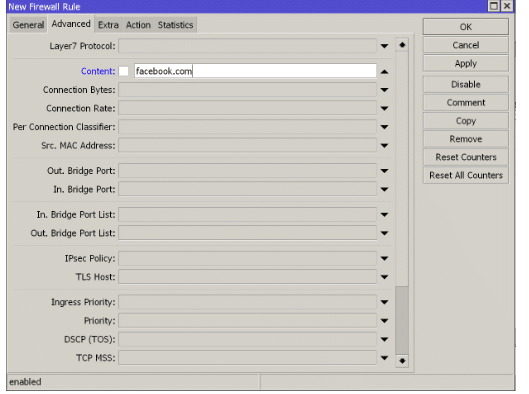
3.2 Apply TLS-HOST type rules
MikroTik’s “tls-host” option is a function of the firewall that allows IPS addresses to be identified before the certificate Hand-shake occurs and the traffic is encrypted. In this part of the certificate negotiation, the data is not encrypted.
By configuring a firewall rule with the “tls-host” option, it is possible to specify the domain name, e.g., *.facebook.com, and add the IPS addresses in a list for further monitoring.
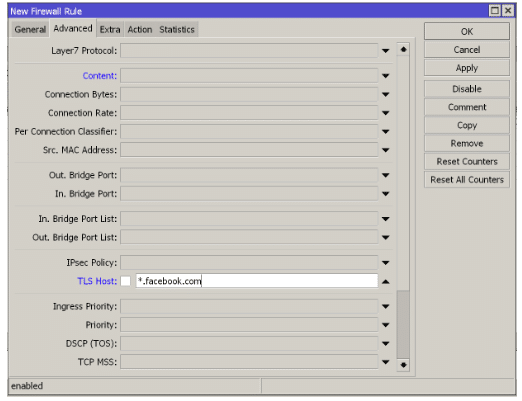
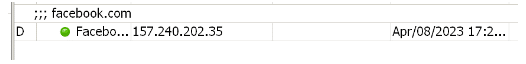
3.3 Using the address list with domains.
If we already have the latest version of RouterOS software, we can use the Address List with domain names; this means that if we create an address list with the name Facebook and the domain www.facebook.com, it will be able to identify those IP addresses automatically.
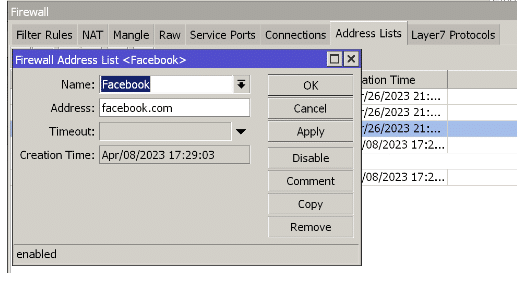
While browsing, domain IP addresses are added to a list of addresses which can be blocked.
4. FlashStart as a DNS integration with MikroTik
It is true that MikroTik has many filtering options, but we often find that there are many domains associated with one main domain, which means that, for example, the domain Facebook.com is linked to different domains such as fb.com, Facebook.es, fbcdn.com, etc.
In these situations, the administrator will need a lot of time to research and configure. Using a DNS system such as FlashStart, integrated with our MikroTik router, is a better choice. It should be remembered that MikroTik has high management capabilities, but, if we are looking for more effective filtering without using the router’s CPU, FlashStart is an excellent choice.
FlashStart has the ability to block DNS traffic just by identifying the domain. Thanks to its artificial intelligence, it can identify all associated domains, without administrator intervention at all times, and it will only require a small initial setup lasting only a few minutes. You can refer to our guide.
We will be able to select categorized domains in a list or add our own domains from the “Personal Blacklist” section.

5. Final notes
In conclusion, blocking unwanted or malicious DNS traffic on the network is an important measure to protect users and prevent cyber attacks. Setting up a firewall on your MikroTik can help you block unwanted or malicious DNS traffic, and, together with integrations like FlashStart, you can effectively and safely block DNS traffic.
In this article we saw how to block DNS traffic on your MikroTik by creating firewall rules and configuring the “content” option. We also saw how the “tls-host” option can be used to identify traffic on secure sites and to then apply Address-List for control.
Blocking DNS traffic is a complex task for an administrator if he or she does not have the right tools for this need. FlashStart will do this job for us, and we no longer have to worry about our subdomains’ being added to a root domain; FlashStart will be able to identify them and block DNS traffic.
You can follow these security recommendations in order to ensure protection of your network from cyber attacks and to provide a safe environment for network users.
See you in the next post!
>> FlashStart is the leader in cloud Internet Security and protects you against malware and undesired content → Try it now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







