
Avoid open DNS resolvers on Mikrotik (and others)
Author: Vittore Zen
It is one of the easiest mistakes to make and in the top 10 Mikrotik mistakes, in this article we see why it is so devastating for our network infrastructure and how to avoid it.
1. A common mistake
During his speech at the “Mikrotik User Meeting USA 2016” Andis ?ri?š ranked it number eight among the “TOP 10 RouterOS Configuration Mistakes” (video), and, the following year, at MikroTik User Meeting Europe, Janis Megis (video) cited it as one of the issues for which MikroTik support was most frequently invoked.
Let’s start with a typical configuration of a Mikrotik router used for simple internet browsing:
/ip firewall nat add action=masquerade chain=srcnat out-interface=Internet
/ip firewall filters add action=fasttrack-connection chain=forward connection-state=established,related
The public ip address is active on the interface called “internet“.
After some time, the user of this connection complains of a degradation in performance. The good technician analyzes the Mikrotik router and notices a high CPU load and a large load of unknown traffic on the public interface. At this point, I used the commands
/tool torch and /tool profile realizes that the CPU is engaged in the dns process and the traffic is DNS resolution traffic: our router is an open DNS or to borrow an expression that derives from the mail servers, we have a DNS open resolver.
2. Where does this malicious traffic come from and why is it so widespread?
When our router receives significant DNS requests from the outside, it means that it has become an endpoint of a DDOS DNS Amplification Attack or DNS Reflector attack. It is therefore not the target of the attack but one of the actors used to amplify the attack. Ideally a recursive DNS server, in our case the Mikrotik router, should accept requests only from clients on our local network but an incorrect configuration can lead to its query from any client even outside our network. These servers are defined as “Open resolvers” and in the context of the ShmooCon (2006) conference analyzing this attack for the first time, Dan Kaminsky and Mike Schiffman made public about 580,000 of them, located throughout the internet.
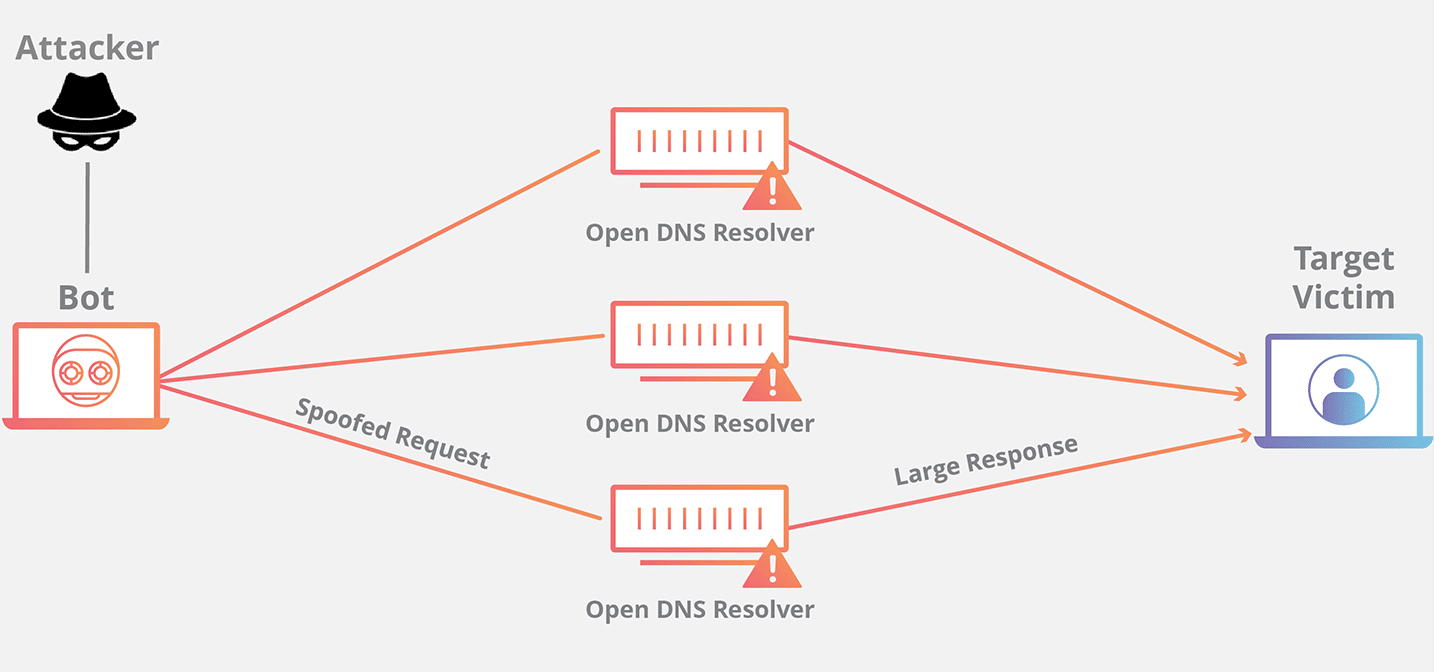
The concept of amplification is based on the fact that very small DNS resolution requests can generate much larger responses, for example, a 60 byte UDP query can generate a 512 response, which is 8.5 times larger than the request. Furthermore, using refraction techniques and making requests that support the EDNS extension, an amplification factor of 66.7 can be reached. CISA has codified this attack in the bulletin
For the details of the attack see this document while at this link you will find an executable version of the same attack. For the more experienced it is recommended to analyze the dns_amp scanner in the Metasploit framework:
msf > use auxiliary/scanner/dns/dns_amp
3. The resolution
Correct configuration
In Mikrotik to solve this problem two simple filtering rules are enough to be placed at the head of our configuration:
add action=drop chain=input connection-state=new dst-port=53 in-interface=Internet protocol=tcp
FlashStart Notification Service
But experience shows that human error is always lurking: we often forget to add this configuration.
Fortunately, there is FlashStart®, market-leading cloud tool for DNS filtering.
One of the new services is email notification in case our Mikrotik behaves as a DNS open resolver. If you use FlashStart® as a DNS resolver and you have forgotten the correct configuration of your router, you will receive an email structured as follows:
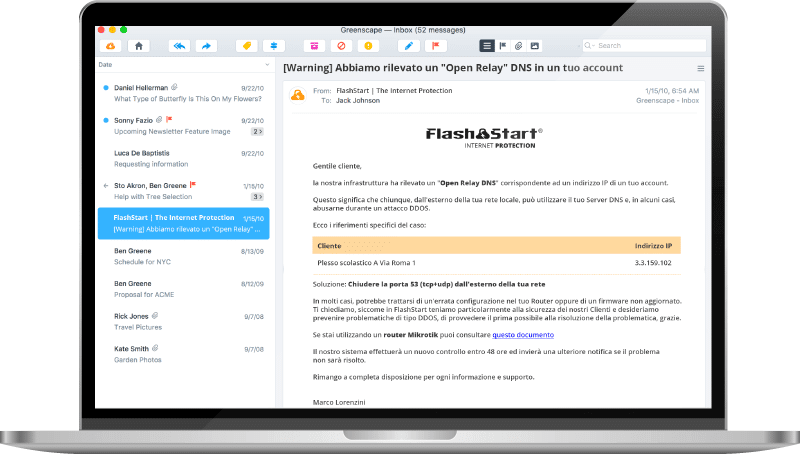
In fact, the Flashstart® servers periodically scan the public IP addresses exposed by customers through a simple DNS request and if it detects that the infrastructure can be used in a DDOS attack, DNS Amplification warns us so that we can take the appropriate corrective actions.
A simple service but appreciated by us sysadmin protects you from your forgetfulness!
4. See other resources about “Router Mikrotik & FlashStart”
» Flashstart and simple integration with all Mikrotik routers
» Content & Malware filter for MikroTik
» Configure Filter on Mikrotik Routeros Device
» Video: “Deploying Content and malware FlashStart® Filter on Mikrotik”
Flashstart is a safe tool for browsing online both on-premise and remotely during smart working
Request a quote and start your free trial now
You can activate the FlashStart® Cloud protection on any sort of Router and Firewall to secure desktop and mobile devices and IoT devices on local networks.







